AccessData AccessData Certified Examiner A30-327 Exam Dumps: Updated Questions & Answers (February 2026)
You currently store alternate hash libraries on a remote server. Where do you configure FTK to access these files rather than the default library, ADKFFLibrary.hdb?
Click the Exhibit button.
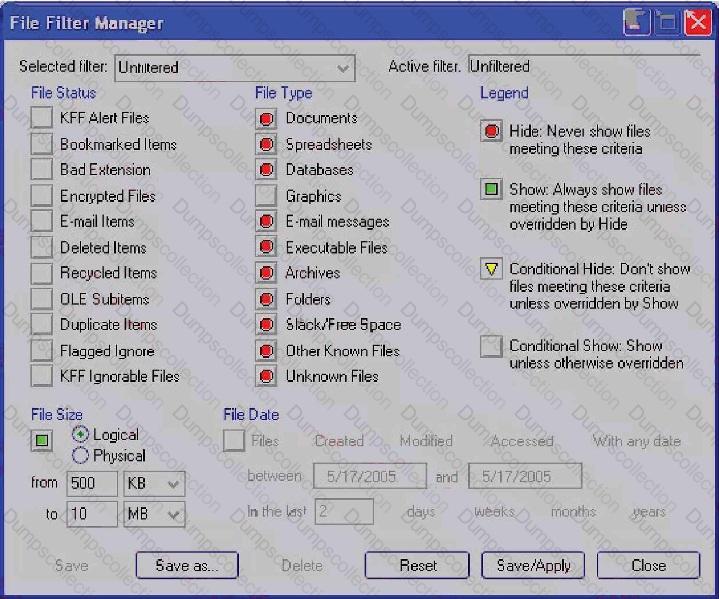
What change do you make to the file filter shown in the exhibit in order to show only graphics with a logical size between 500 kilobytes and 10 megabytes?
What is the most effective method to facilitate successful password recovery?
What are three image file formats that can be read by FTK Imager? (Choose three.)
In FTK, which search broadening option allows you to find grammatical variations of the word "kill" such as "killer," "killed," and "killing"?
FTK uses Data Carving to find which three file types? (Choose three.)
In PRTK, which type of attack uses word lists?
Using the FTK Report Wizard, which two options are available in the List by File Path
window? (Choose two.)
Click the Exhibit button.
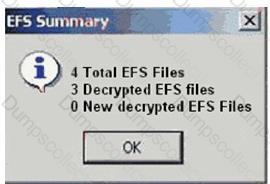
When decrypting EFS files in a case, you receive the result shown in the exhibit. What is the most plausible explanation for this result?
What are three types of evidence that can be added to a case in FTK? (Choose three.)

