Blue Prism Blue Prism Professional Developer APD01 Exam Dumps: Updated Questions & Answers (February 2026)
A Process Definition Document, for a new process to open ISA accounts, specifies that the value “2008 Cash ISA” is to be entered into the Product Selection field of the following screen:
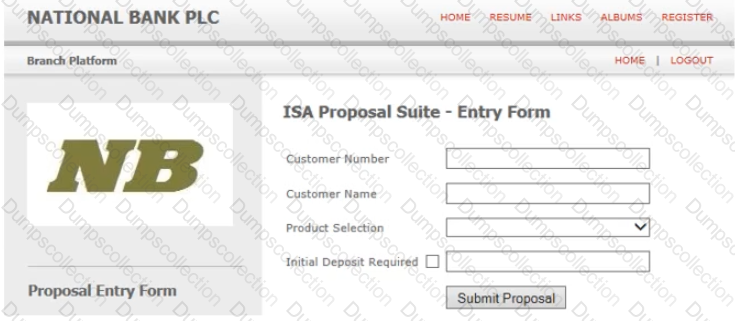
The Product Selection field is a drop down menu with the following options available:

According to Best Practice, which of the following design options are correct for populating the Product Selection field with the value 2008 Cash ISA:
Which of the following are correct? (Choose three.)
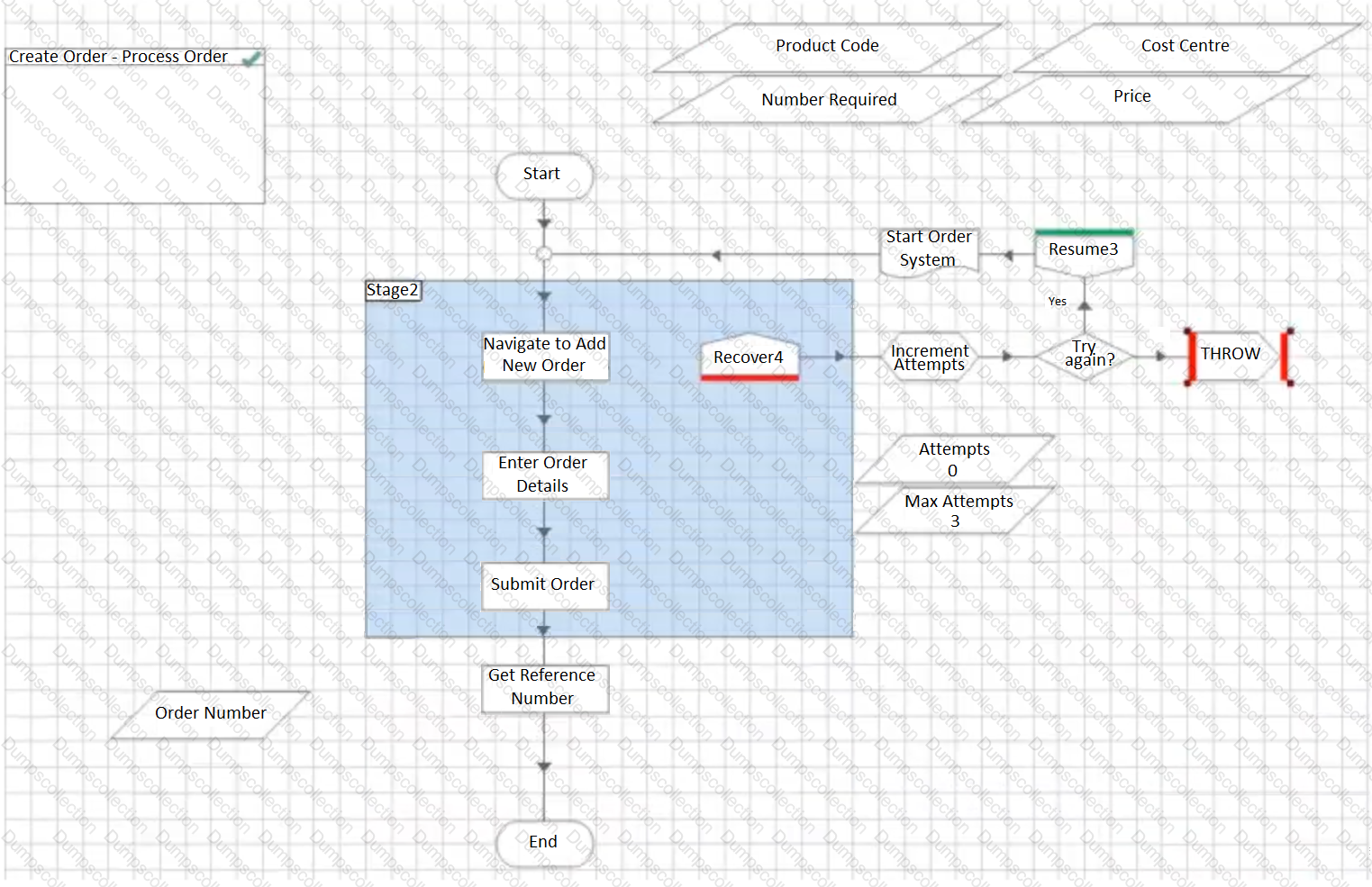
The following sub-page in a process creates an order in an order system.
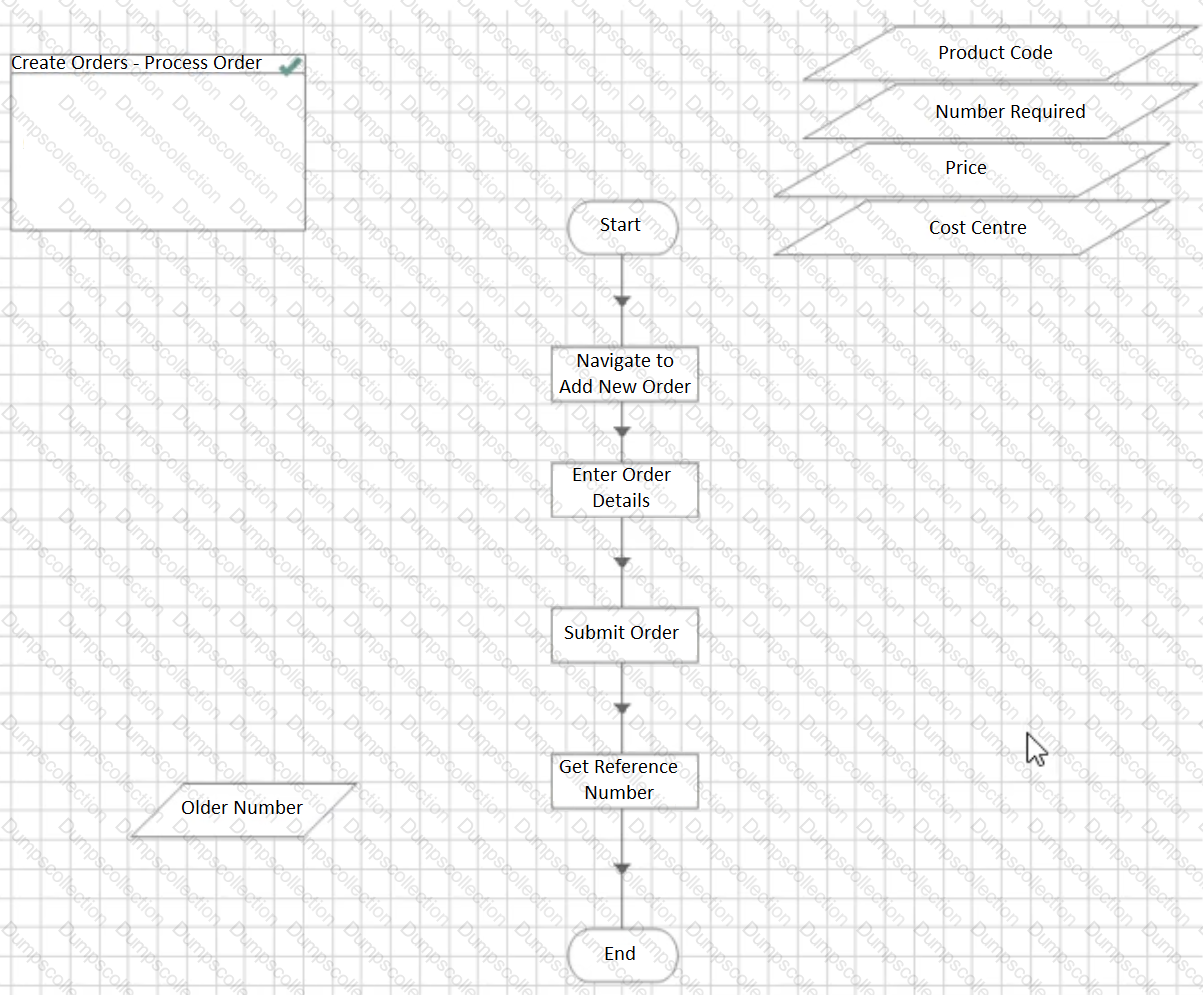
The Actions called perform the following steps:
Navigate to New Order – The application is navigated to a new order screen. There is a wait stage to confirm the navigation is successful – if this wait stage times out, an exception is configured which will bubble up to this page.
Enter Order Details – The Order details are entered triggering a ‘Confirm Order’ window. At this page, the order has not been submitted. There is a wait stage to confirm the ‘Confirm Order’ window has appeared – if this stage times out, an exception is configured which will bubble up to this page.
Submit Order – The order is confirmed and placed in the Client’s order system. There is a wait stage, for a reference number, configured that the order has been successfully submitted. If this wait stage times out, an exception is configured which will bubble up to this page. There is a known bug in the application which results in the application occasionally freezing when an order is submitted but before the reference number is displayed, thus leaving the user uncertain if the order has been successfully submitted or not.
Get Reference Number – A resultant reference number is read from the application.
In order to build some resilience into the process, some retry logic is to be added. Which of the below options offers the best retry solution?
A)
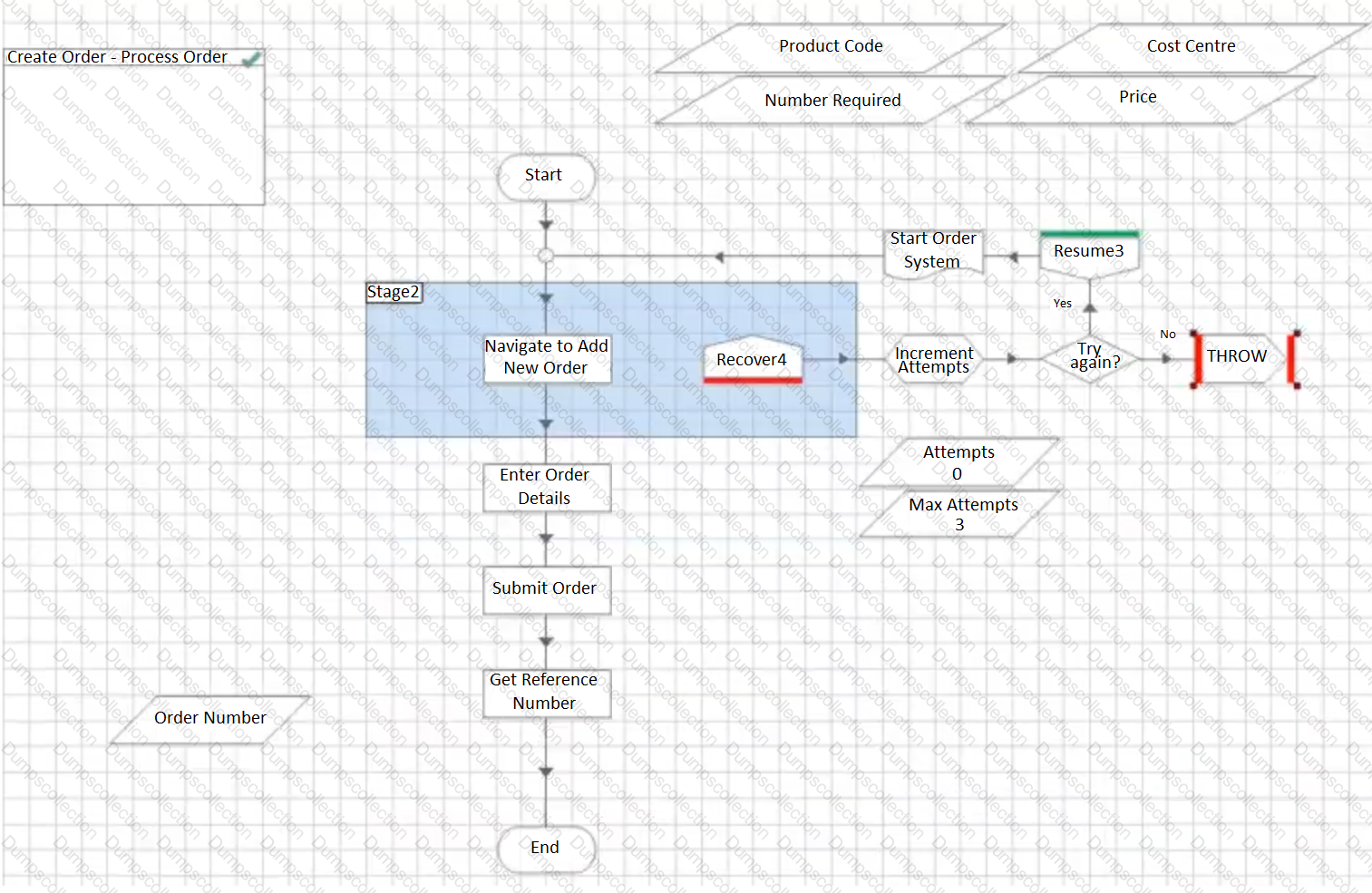
B)
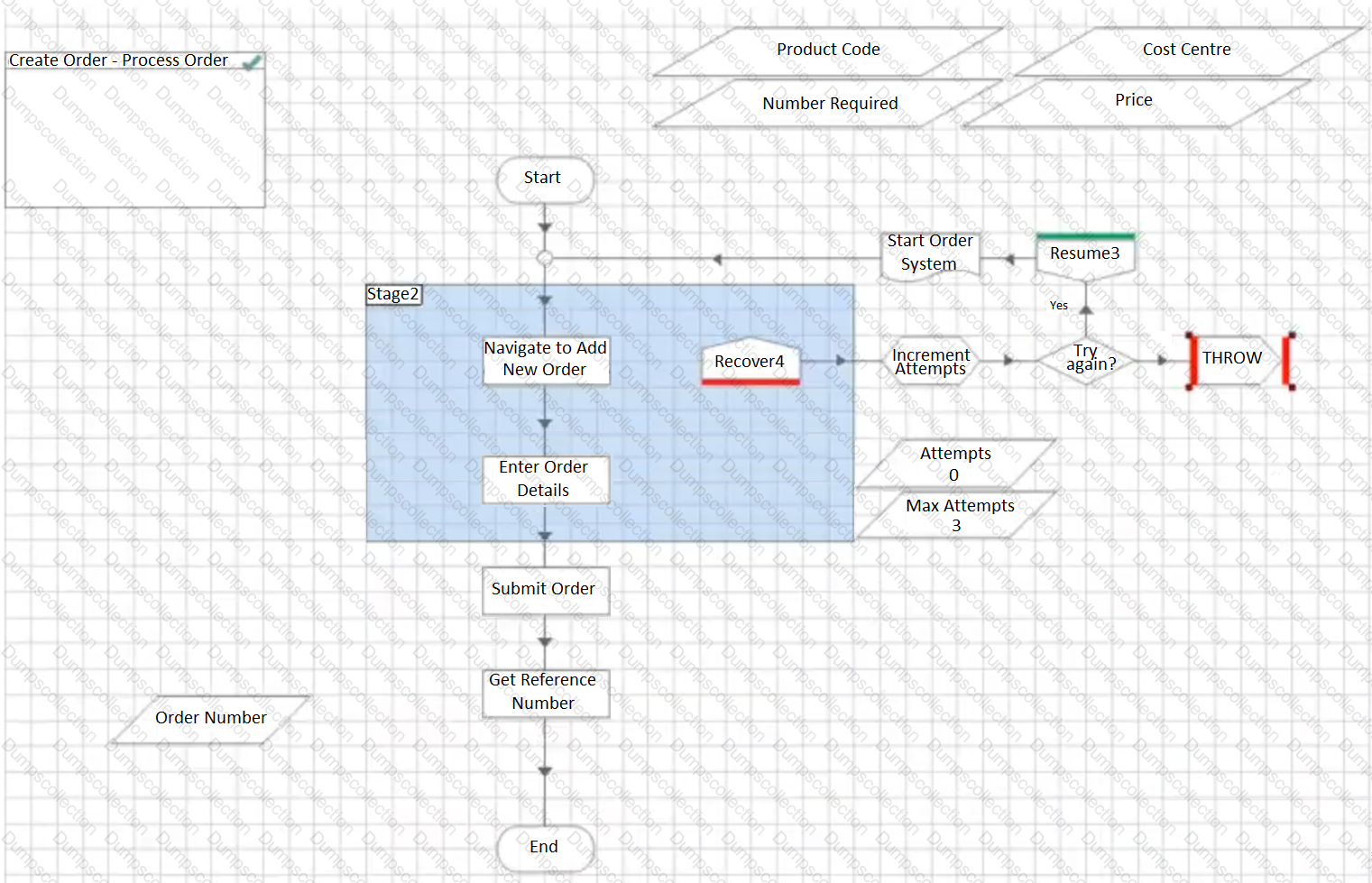
C)
D)

Using a Wait stage to check if a Java element exists requires the Java Application Model tree to be traversed. Constantly accessing the model can be costly in terms of CPU efficiency.
Which of the following tips is a valid method to help manage this CPU efficiency cost?
An Insurance company has created 4 Blue Prism processes:
Change of Address
Claims Processing
Renewals
Order Letter
The Order Letter process is not a published process but is called as a sub process by each of the 3 other processes.
Each day at 6am a scheduler starts:
2 instances of the Renewals process on the same virtual machine
9 instances of the Claims Processing process on 3 different virtual machines
1 instance of the Change of Address process on its own virtual machine
How many robot licenses will be consumed by the running processes?
Which of the following statements, about interfacing with browser applications are true? (Choose three.)
Which of the following statements about setting and using Work Queue priority are correct?
The Blue Prism Work Queue business object can be used to change the priority of an item after it has been added to the queue.
Items are worked in order of lowest priority number first.
The default priority setting is 1.
Setting the priority for a Work Queue item is done when the item is first added to the queue using the Add To Queue action.
An action within an object has been written that automates a browser based application. All elements can be spied successfully and the object runs without defect in Object Studio. However, when ran in Control Room, exceptions are thrown that indicate elements cannot be found. This is because elements on the web page do not load all at once, they load slowly one after another instead. Which of the following would be the most appropriate to improve the resilience of the automation?
Which of the following statements regarding Blue Prism Credentials are true?
1. The Business Object; Internal - Credentials cannot retrieve encrypted credentials from the Blue Prism database
2. It is best practice to hold application credentials within the Process that requires them
3. It is best practice to hold application credentials within the Object that requires them
4. It is possible to hold Blue Prism Credentials in an unencrypted state
A retail bank has promoted 5 Blue Prism processes to production:
Email Poller
Customer Onboarding
Amend Contact Details
Direct Debit Cancellations
Onboarding Reporting
One instance of the email Poller process will run 24/7 feeding work queues for the other two processes.
Two concurrent instances of the Customer Onboarding process will run between 6am and 11pm each day on the same VM.
Two concurrent instances of the Amend Contact Details process will run between 8am and 8pm each day on two VMs.
One instance of the Direct Debit Cancellations process will run between 6am and 4pm each day on the same VM as the Email Poller process. The scheduler that starts the Direct Debit Cancellations process is configured to run the Onboarding Reporting process when the Direct Debit Cancellations process has successfully completed.
How many robot licenses are required?

