Checkpoint Check Point Certified Security Administrator R81.20 CCSA (156-215.81.20) 156-215.81 Exam Dumps: Updated Questions & Answers (March 2026)
When using Automatic Hide NAT, what is enabled by default?
You can see the following graphic:
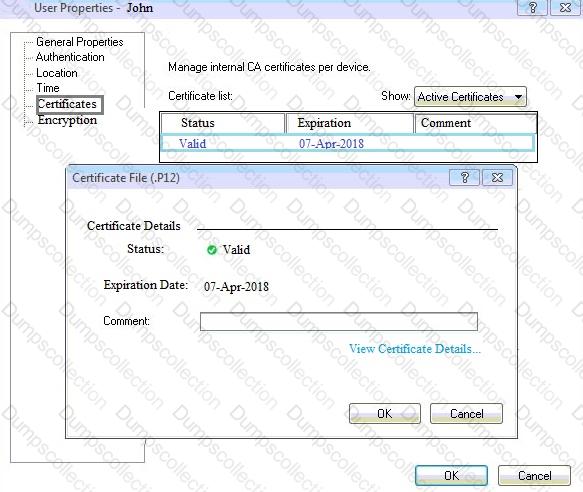
What is presented on it?
Which software blade enables Access Control policies to accept, drop, or limit web site access based on user, group, and/or machine?
You are the Check Point administrator for Alpha Corp with an R80 Check Point estate. You have received a call by one of the management users stating that they are unable to browse the Internet with their new tablet connected to the company Wireless. The Wireless system goes through the Check Point Gateway. How do you review the logs to see what the problem may be?
A Check Point Software license consists of two components, the Software Blade and the Software Container. There are ______ types of Software Containers: ________.
The “Hit count” feature allows tracking the number of connections that each rule matches. Will the Hit count feature work independently from logging and Track the hits even if the Track option is set to “None”?
What are the two elements of address translation rules?
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
How would you determine the software version from the CLI?
Which of the following cannot be configured in an Access Role Object?

