Cisco Cisco Certified Support Technician (CCST) Cybersecurity 100-160 Exam Dumps: Updated Questions & Answers (February 2026)
You need to transfer configuration files to a router across an unsecured network.
Which protocol should you use to encrypt the files in transit?
Which Windows app is a command-line interface that includes a sophisticated scripting language used to automate Windows tasks?
You work for a hospital that stores electronic protected health information (ePHI) in an online portal. Authorized employees can use their mobile devices to access patient ePHI.
You need to ensure that employees’ mobile devices comply with HIPAA regulations.
Which safeguard should you develop and implement?
Which two passwords follow strong password policy guidelines?(Choose 2.)
Which macOS security feature encrypts the entire macOS volume?
Which encryption type is commonly used to secure WiFi networks?
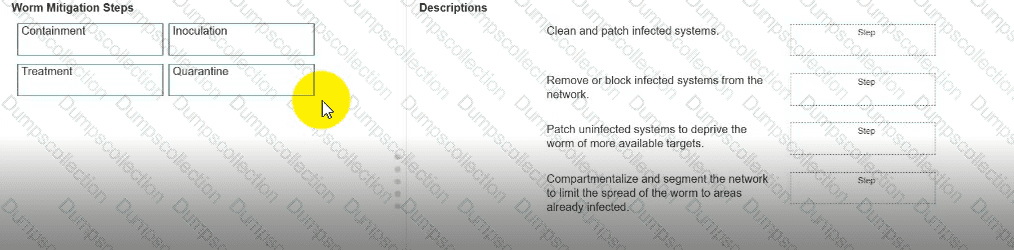
Move each worm mitigation step from the list on the left to the correct description on the right.
Note: You will receive partial credit for each correct answer.
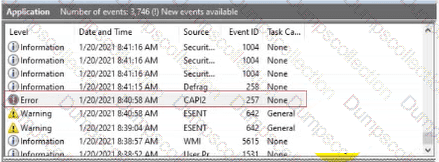
You are reviewing the Application log on a Windows computer. You see an event with an error-level message as shown.
What can you determine about the application that generated the event message?
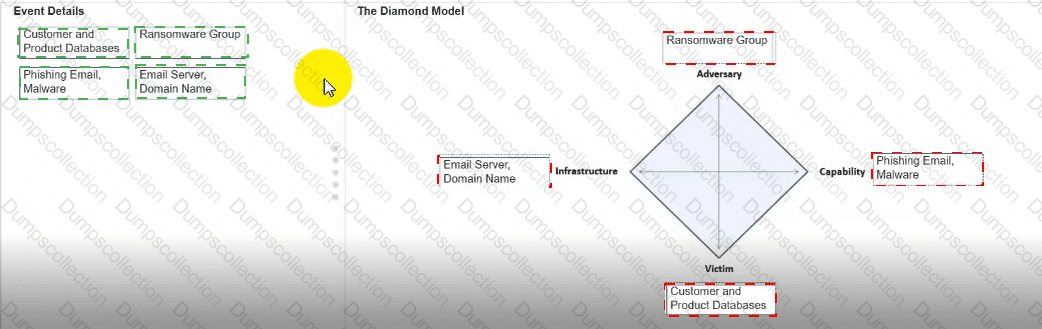
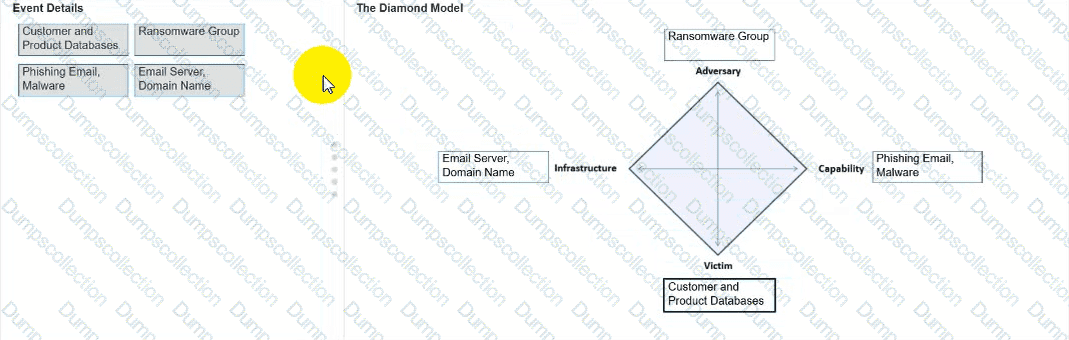
You need to diagram an intrusion event by using the Diamond Model.
Move each event detail from the list on the left to the correct location in the diagram on the right.
Note: You will receive partial credit for each correct response.
You are planning to work from home. Your company requires that you connect to the company network through a VPN.
Which three critical functions do VPNs provide to remote workers?(Choose 3.)