Cisco Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) 200-201 Exam Dumps: Updated Questions & Answers (March 2026)
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
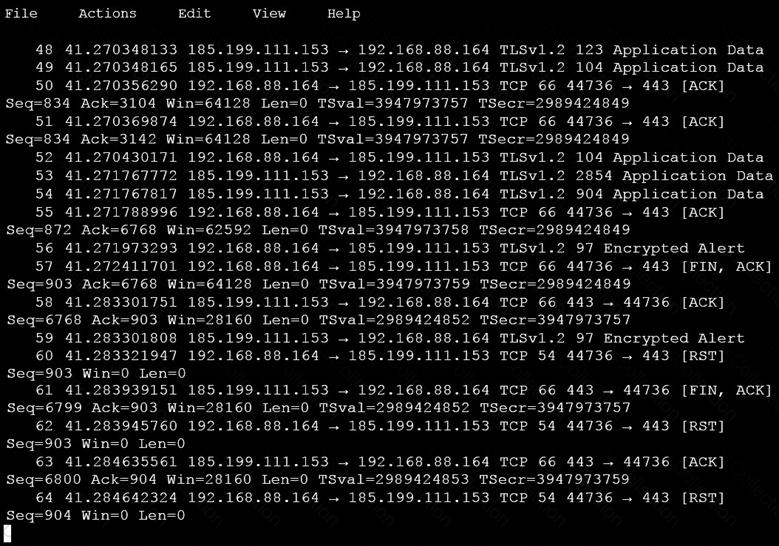
Which obfuscation technique is the attacker using?
What is the difference between a threat and an exploit?
What is the difference between inline traffic interrogation and traffic mirroring?
What is the benefit of processing statistical data for security systems?
Refer to the exhibit.
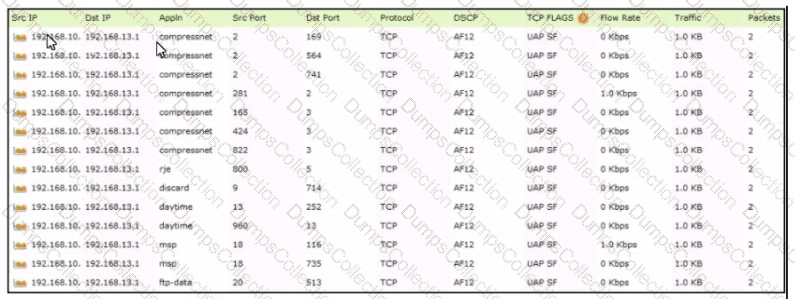
Which tool was used to generate this data?
Which type of data is used to detect anomalies in the network?
Which type of attack is a blank email with the subject "price deduction" that contains a malicious attachment?
What is the difference between the ACK flag and the RST flag?
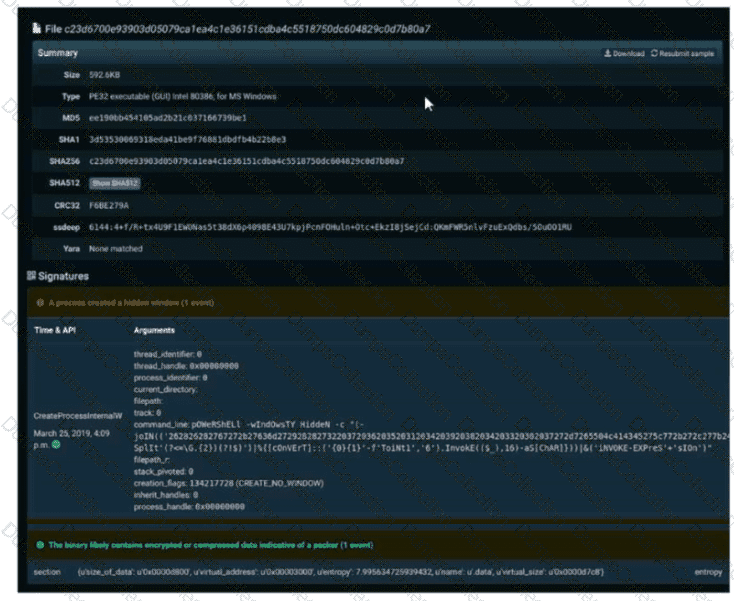
Refer to the exhibit. A SOC engineer is analyzing Cuckoo Sandbox report for a file that has been identified as suspicious by the endpoint security system. What is the state of the file?

