Cisco Implementing and Administering Cisco Solutions (200-301 CCNA) v1.1 200-301 Exam Dumps: Updated Questions & Answers (February 2026)
Which function does an SNMP agent perform?
Which type of IPv6 address is publicly routable in the same way as IPv4 public address?
What is a function of TFTP in network operations?
An administrator must secure the WLC from receiving spoofed association requests. Which steps must be taken to configure the WLC to restrict the requests and force the user to wait 10 ms to retry an association request?
How does CAPWAP communicate between an access point in local mode and a WLC?
Which protocol requires authentication to transfer a backup configuration file from a router to a remote server?
Which action is taken by a switch port enabled for PoE power classification override?
A frame that enters a switch fails the Frame Check Sequence. Which two interface counters are incremented? (Choose two)
What does a router do when configured with the default DNS lookup settings, and a URL is entered on the CLI?
Which two components are needed to create an Ansible script that configures a VLAN on a switch? (Choose two.)
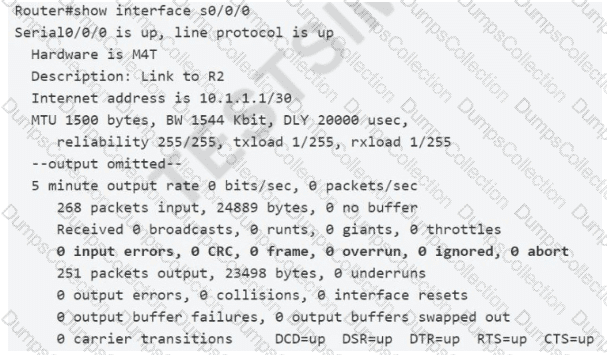
Refer to the exhibit.
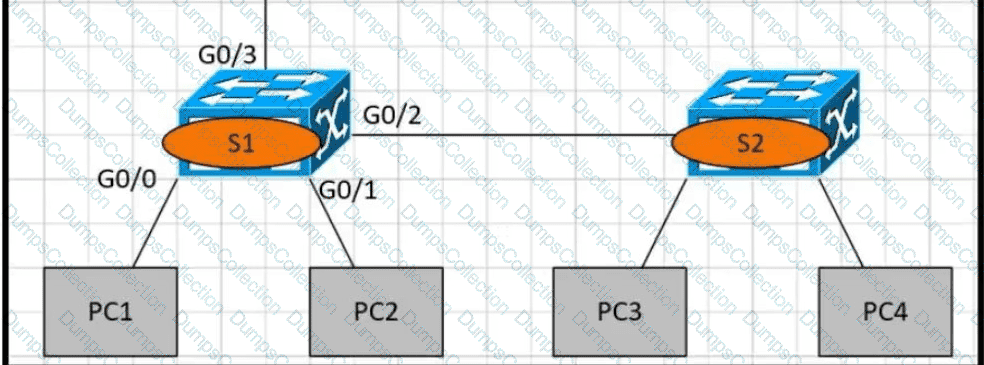
PC1 is trying to ping PC3 for the first time and sends out an ARP to S1 Which action is taken by S1?
Which MAC address is recognized as a VRRP virtual address?
Refer to the exhibit.
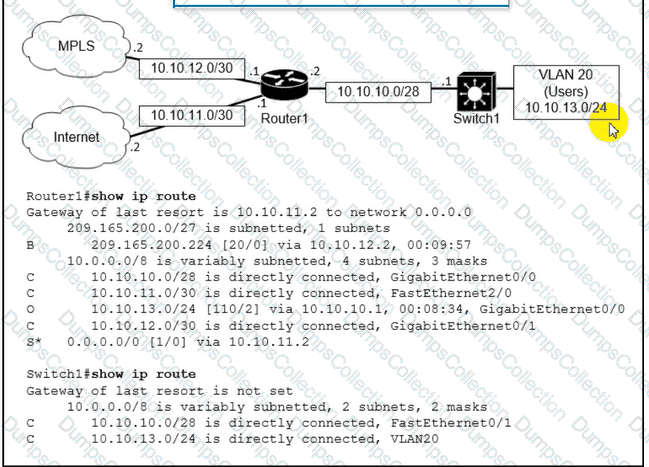
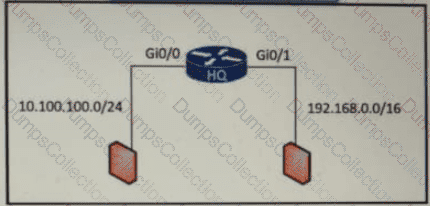
which path is used by the router for internet traffic ?
Which WAN access technology is preferred for a small office / home office architecture?
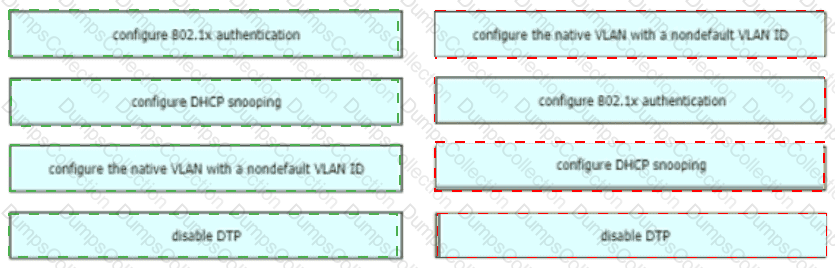
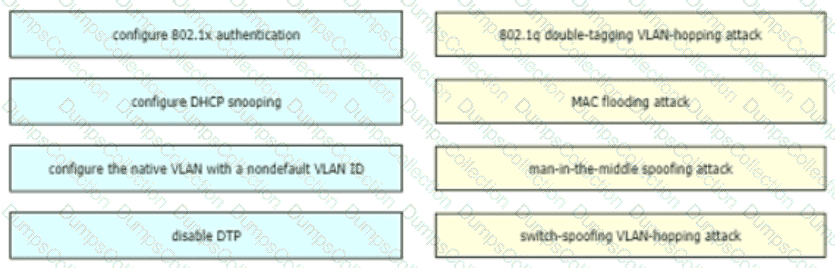
Drag and drop the attack-mitigation techniques from the left onto the Types of attack that they mitigate on the right.
Refer to the exhibit.
An access list is required to permit traffic from any host on interface G0/0 and deny traffic from interface G/0/1. Which access list must be applied?

Refer to the exhibit.

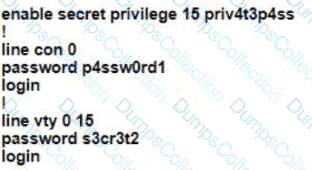
Which password must an engineer use to enter the enable mode?
Which HTTP status code is returned after a successful REST API request?
How are VLAN hopping attacks mitigated?
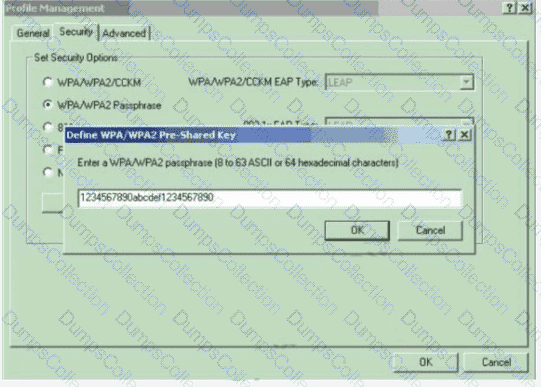
Which type of wireless encryption is used for WPA2 in preshared key mode?
Two switches are connected and using Cisco Dynamic Trunking Protocol SW1 is set to Dynamic Desirable
What is the result of this configuration?
Refer to the exhibit.
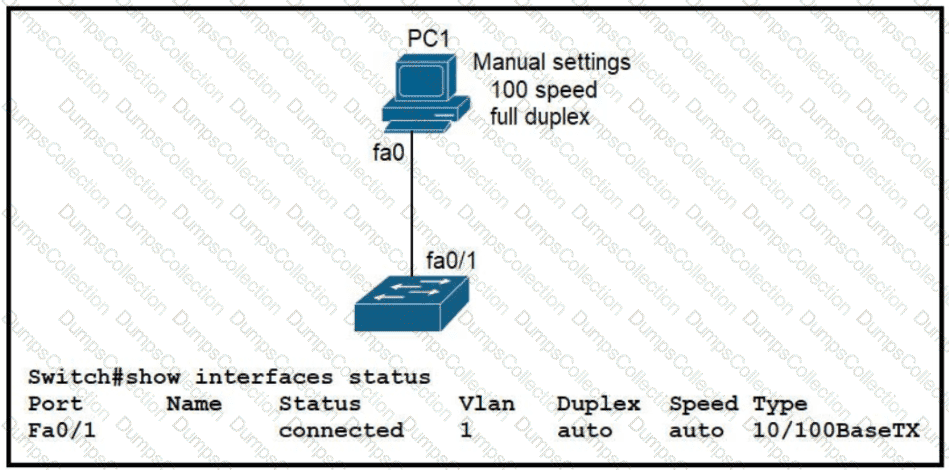
The link between PC1 and the switch is up. but it is performing poorly. Which interface condition is causing the performance problem?
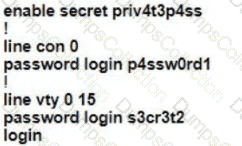
A Cisco engineer is configuring a factory-default router with these three passwords:
• The user EXEC password for console access is p4ssw0rd1
• The user EXEC password for Telnet access is s3cr3t2
• The password for privileged EXEC mode is pnv4t3p4ss Which command sequence must the engineer configured
A)
B)
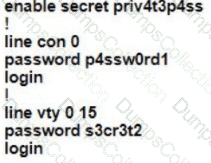
C)
D)

Which WLC management connection type is vulnerable to man-in-the-middle attacks?
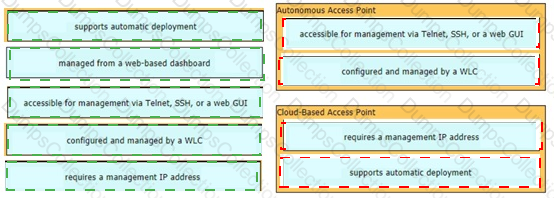
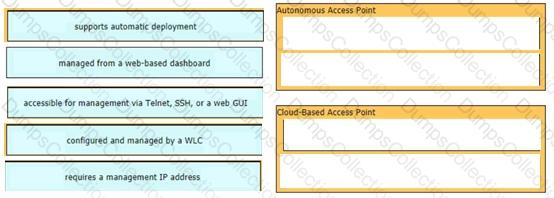
Drag and drop the facts about wireless architectures from the left onto the types of access point on the right. Not all options are used.
What is a requirement for nonoverlapping Wi-Fi channels?
What are two benefits of FHRPs? (Choose two.)
An engineer must configure R1 for a new user account. The account must meet these requirements:
* It must be configured in the local database.
* The username is engineer.
* It must use the strongest password configurable. Which command must the engineer configure on the router?
Refer to the exhibit.

Users need to connect to the wireless network with IEEE 802. 11r-compatible devices. The connection must be maintained as users travel between floors or to other areas in the building What must be the configuration of the connection?
Refer to the exhibit.
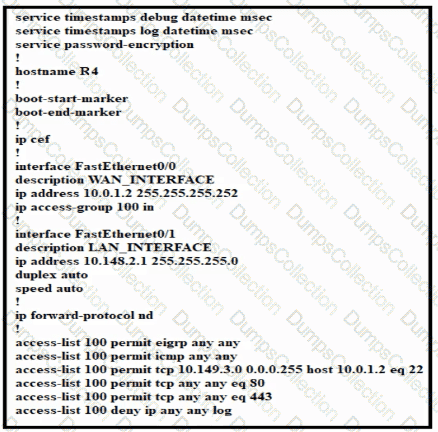
Which configuration enables DHCP addressing for hosts connected to interface FastEthernetO/1 on router R4?
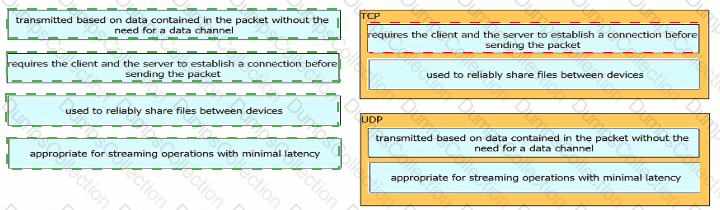
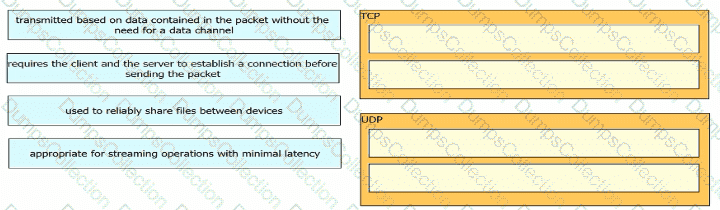
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.
Refer to the exhibit.
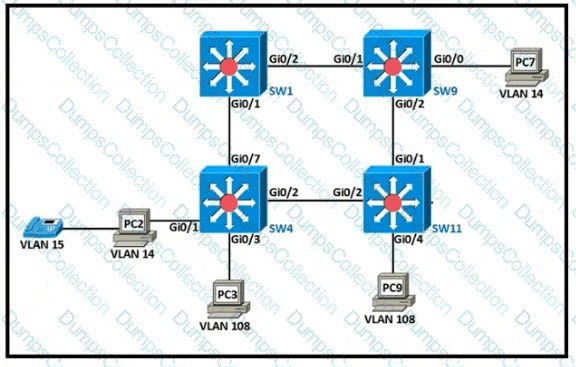
The following must be considered:
• SW1 is fully configured for all traffic
• The SW4 and SW9 links to SW1 have been configured
• The SW4 interface Gi0/1 and Gi0/0 on SW9 have been configured
• The remaining switches have had all VLANs adde d to their VLAN database
Which configuration establishes a successful ping from PC2 to PC7 without interruption to traffic flow between other PCs?
A)

B)
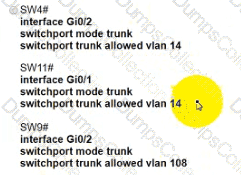
C)

D)

Which protocol uses the SSL?
What causes a port to be placed in the err-disabled state?
Refer to the exhibit.
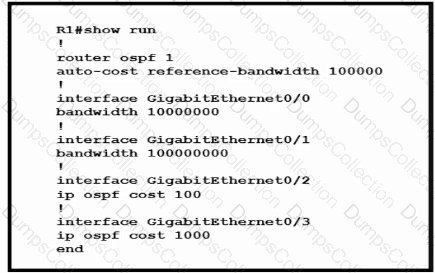
Router R1 resides in OSPF Area 0. After updating the R1 configuration to influence the paths that it will use to direct traffic, an engineer verified that each of the four Gigabit interfaces has the same route to 10.10.0.0/16. Which interface will R1 choose to send traffic to reach the route?
Refer to the exhibit.

Which plan must be Implemented to ensure optimal QoS marking practices on this network?
Refer to the exhibit.
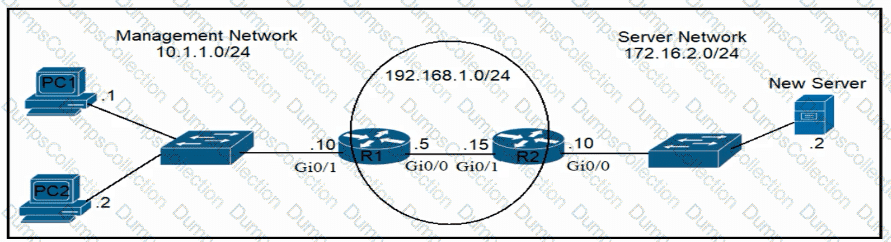
An engineer is updating the R1 configuration to connect a new server to the management network. The PCs on the management network must be blocked from pinging the default gateway of the new server. Which command must be configured on R1 to complete the task?
Which two spanning-tree states are bypassed on an interface running PortFast? (Choose two.)
Refer to the exhibit.
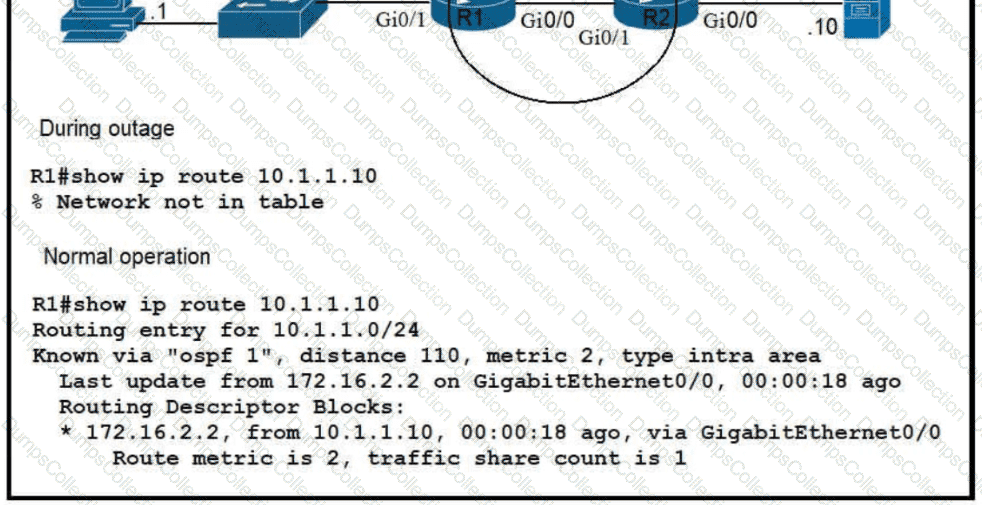
Which route must be configured on R1 so that OSPF routing is used when OSPF is up. but the server is still reachable when OSPF goes down?
Refer to the exhibit.
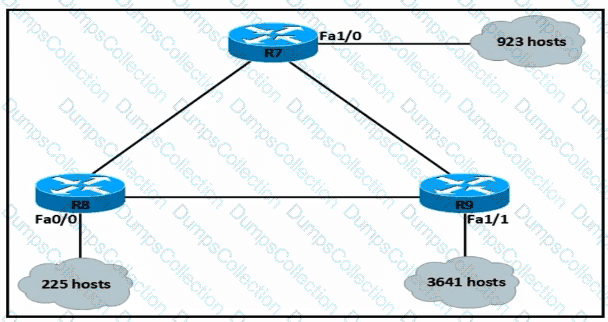
An IP subnet must be configured on each router that provides enough addresses for the number of assigned hosts and anticipates no more than 10% growth for now hosts. Which configuration script must be used?
A)

B)
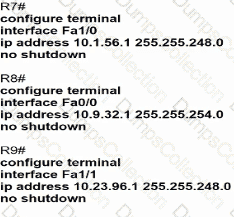
C)

D)
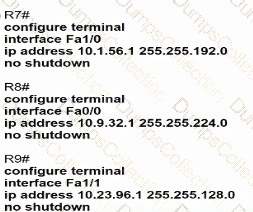
Refer to the exhibit.
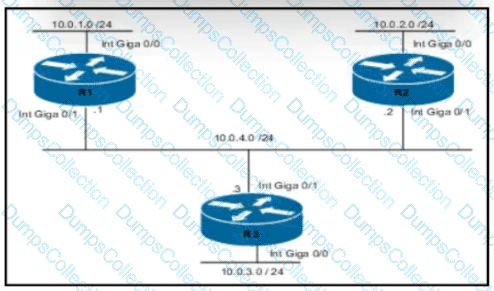
Routers R1 and R3 have the default configuration The router R2 priority is set to 99 Which commands on R3 configure it as the DR in the 10.0 4.0/24 network?
Refer to the exhibit.

Packets received by the router from BGP enter via a serial interface at 209.165.201.10. Each route is present within the routing table. Which interface is used to forward traffic with a destination IP of 10.10.10.24?
Refer to the exhibit.
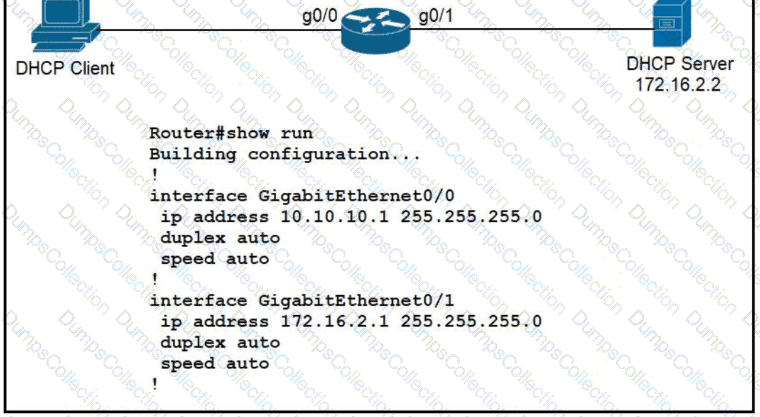
An engineer is configuring a new router on the network and applied this configuration. Which additional configuration allows the PC to obtain its IP address from a DHCP server?
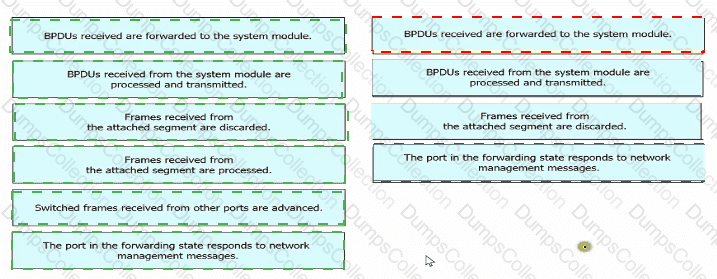
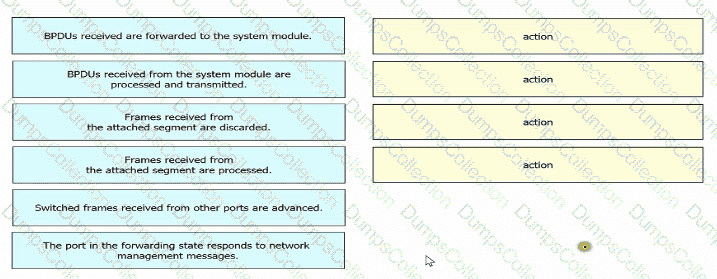
Drag and drop the Rapid PVST+ forwarding slate actions from the loft to the right. Not all actions are used.
A network engineer is configuring a switch so that it is remotely reachable via SSH. The engineer has already configured the host name on the router. Which additional command must the engineer configure before entering the command to generate the RSA key?
Refer to the exhibit.
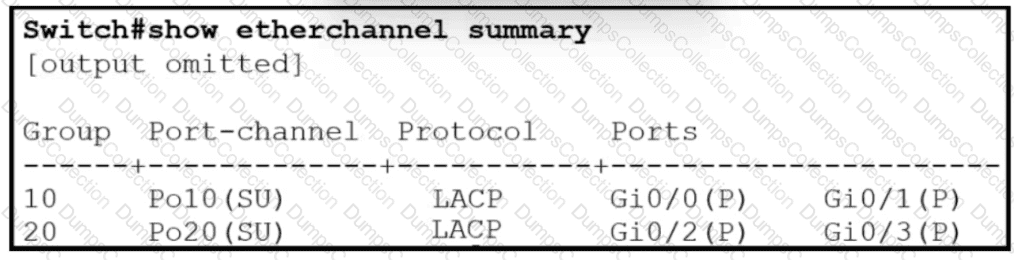
Which two commands when used together create port channel 10? (Choose two.)
What is the difference between IPv6 unicast and anycast addressing?
Refer to the exhibit.
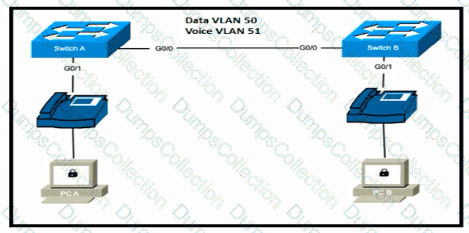
Switch A is newly configured. All VLANs are present in the VLAN database. The IP phone and PC A on Gi0/1 must be configured for the appropriate VLANs to establish connectivity between the PCs. Which command set fulfills the requirement?
A)
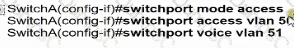
B)

C)

D)

Refer to the exhibit.
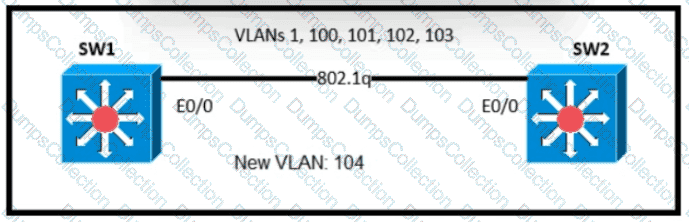
An engineer is asked to insert the new VLAN into the existing trunk without modifying anything previously configured Which command accomplishes this task?
Which type of network attack overwhelms the target server by sending multiple packets to a port until the half-open TCP resources of the target are exhausted?