Cisco Conducting Threat Hunting and Defending using Cisco Technologies for Cybersecurity 300-220 CBRTHD 300-220 Exam Dumps: Updated Questions & Answers (February 2026)
During multiple investigations using Cisco telemetry, analysts observe attackers consistently perform internal discovery before privilege escalation and avoid high-risk actions. Why is this observation useful for attribution?
A threat hunter usesCisco Secure Endpointto investigate a suspected credential-harvesting attack that does not involve dropping files to disk. Which capability is MOST critical for detecting this activity?
A threat hunter usesCisco Secure Network Analytics (Stealthwatch)to identify potential command-and-control traffic. Which characteristic MOST strongly indicates beaconing behavior?
Refer to the exhibit.
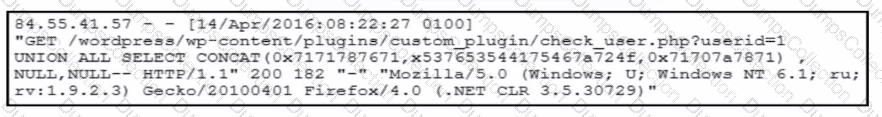
A forensic team must investigate how the company website was defaced. The team isolates the web server, clones the disk, and analyzes the logs. Which technique was used by the attacker initially to access the website?
A SOC team wants to detect lateral movement performed using legitimate administrative tools rather than malware. Which telemetry source provides the MOST reliable visibility for this hunting objective?
What triggers unstructured threat hunting?
During an investigation, analysts observe that attackers consistently avoid PowerShell logging, disable AMSI, and prefer WMI for execution. Why is this information critical for attribution?
A SOC team using Cisco security technologies wants to improve its ability to detect threats that bypass traditional security controls by abusing valid user credentials. Which hunting focus MOST effectively addresses this challenge?
While investigating multiple incidents, analysts notice that attackers consistently use SMB for lateral movement and avoid PowerShell execution. Why is this observation valuable for attribution?
A SOC manager wants to evaluate whether the organization’s Cisco-based threat hunting program is improving over time. Which metric BEST reflects increased threat hunting effectiveness?

