Cisco Designing and Implementing Secure Cloud Access for Users and Endpoints (SCAZT) 300-740 Exam Dumps: Updated Questions & Answers (March 2026)
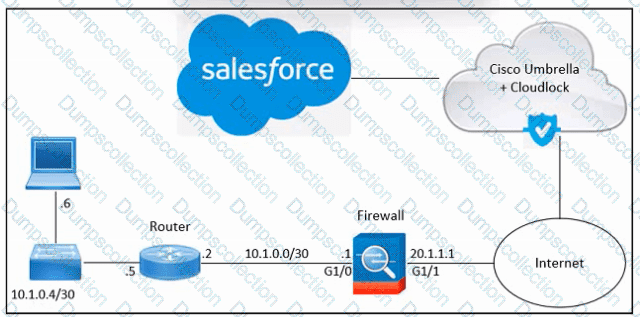
Refer to the exhibit. An engineer must integrate Cisco Cloudlock with Salesforce in an organization. Despite the engineer's successful execution of the Salesforce integration with Cloudlock, the administrator still lacks the necessary visibility. What should be done to meet the requirement?
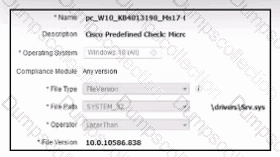
Refer to the exhibit. A security engineer must configure a posture policy in Cisco ISE to ensure that employee laptops have a critical patch for WannaCry installed before they can access the network. Which posture condition must the engineer configure?
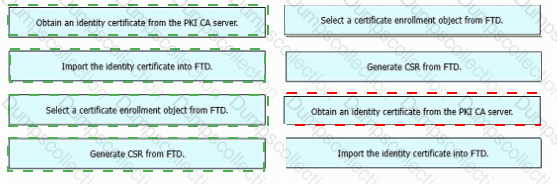
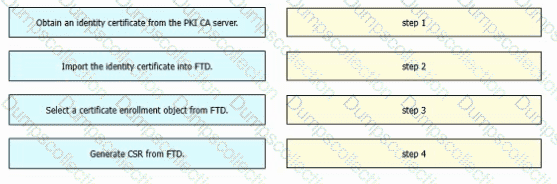
An engineer must configure certificate-based authentication in a cloud-delivered Cisco Secure Firewall Management Center. Drag and drop the steps from left to right to manually enroll certificates on a Cisco Secure Firewall Threat Defense Virtual device.

Refer to the exhibit. An engineer is analyzing a Cisco Secure Firewall Management Center report. Which activity does the output verify?
An engineer configures trusted endpoints with Active Directory with Device Health to determine if an endpoint complies with the policy posture. After a week, an alert is received by one user, reporting problems accessing an application. When the engineer verifies the authentication report, this error is found:
"Endpoint is not trusted because Cisco Secure Endpoint check failed, Check user's endpoint in Cisco Secure Endpoint."
Which action must the engineer take to permit access to the application again?
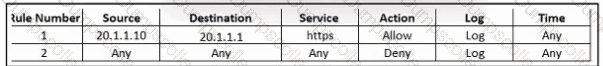
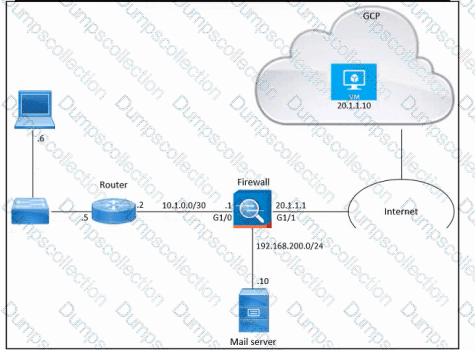
Refer to the exhibit. An engineer must provide HTTPS access from the Google Cloud Platform virtual machine to the on-premises mail server. All other connections from the virtual machine to the mail server must be blocked. The indicated rules were applied to the firewall; however, the virtual machine cannot access the mail server. Which two actions should be performed on the firewall to meet the requirement? (Choose two.)
An engineer is configuring multifactor authentication using Duo. The implementation must use Duo Authentication Proxy and the Active Directory as an identity source. The company uses Azure and a local Active Directory. Which configuration is needed to meet the requirement?
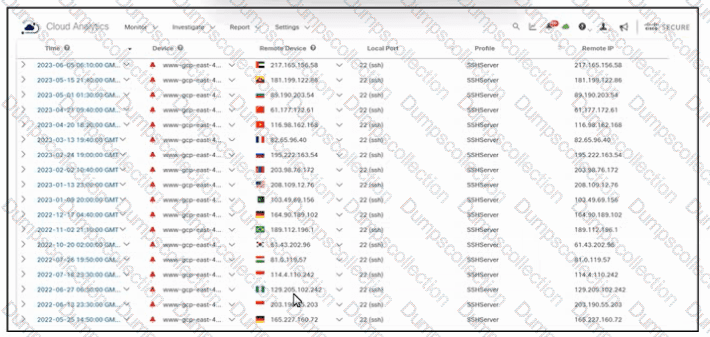
Refer to the exhibit. An engineer must analyze the Cisco Secure Cloud Analytics report. What is occurring?
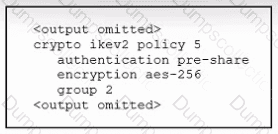
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv2 VPN that will use SHA-512 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the tunnel fails to establish. Which command must be run to meet the requirement?
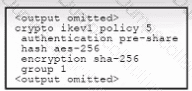
Refer to the exhibit. An engineer must configure a remote access IPsec/IKEv1 VPN that will use AES256 and SHA256 on a Cisco ASA firewall. The indicated configuration was applied to the firewall; however, the tunnel fails to establish. Which two IKEv1 policy commands must be run to meet the requirement? (Choose two.)