Cisco Implementing and Operating Cisco Security Core Technologies (SCOR 350-701) 350-701 Exam Dumps: Updated Questions & Answers (March 2026)
What provides the ability to program and monitor networks from somewhere other than the DNAC GUI?
Which two application layer preprocessors are used by Firepower Next Generation Intrusion Prevention
System? (Choose two)
Which attack gives unauthorized access to files on the web server?
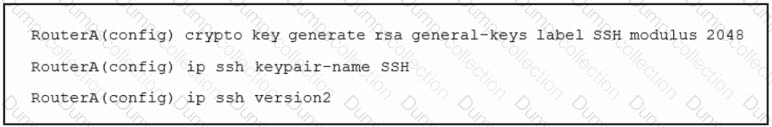
Refer to the exhibit. An engineer must enable secure SSH protocols and enters this configuration. What are two results of running this set of commands on a Cisco router? (Choose two.)
What is the purpose of the certificate signing request when adding a new certificate for a server?
What is a benefit of using Cisco CWS compared to an on-premises Cisco WSA?
With regard to RFC 5176 compliance, how many IETF attributes are supported by the RADIUS CoA feature?
Which information is required when adding a device to Firepower Management Center?
Which Cisco security solution secures public, private, hybrid, and community clouds?
A customer has various external HTTP resources available including Intranet. Extranet, and Internet, with a proxy configuration running in explicit mode Which method allows the client desktop browsers to be configured to select when to connect direct or when to use the proxy?
What is the result of running the crypto isakmp key ciscXXXXXXXX address 172.16.0.0 command?
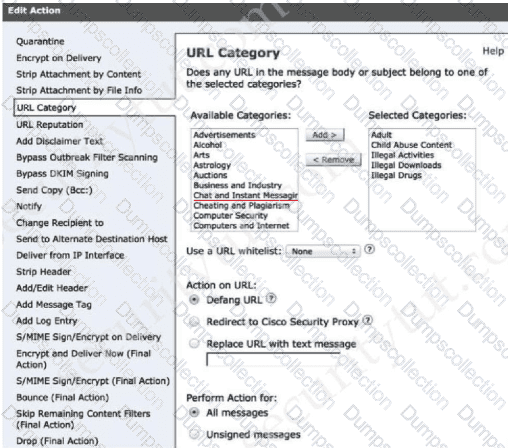
A network administrator is configuring a rule in an access control policy to block certain URLs and selects the “Chat and Instant Messaging” category. Which reputation score should be selected to accomplish this goal?
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files which need analysis?
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware?
(Choose two)
What is the term for when an endpoint is associated to a provisioning WLAN that is shared with guest
access, and the same guest portal is used as the BYOD portal?