CyberArk CyberArk Defender - EPM EPM-DEF Exam Dumps: Updated Questions & Answers (March 2026)
An EPM Administrator would like to notify end users whenever the Elevate policy is granting users elevation for their applications. Where should the EPM Administrator go to enable the end-user dialog?
An EPM Administrator would like to enable CyberArk EPM's Ransomware Protection in Restrict mode. What should the EPM Administrator do?
Which programming interface enables you to perform activities on EPM objects via a REST Web Service?
For Advanced Policies, what can the target operating system users be set to?
Which EPM reporting tool provides a comprehensive view of threat detection activity?
How does CyberArk EPM's Ransomware Protection feature monitor for Ransomware Attacks?
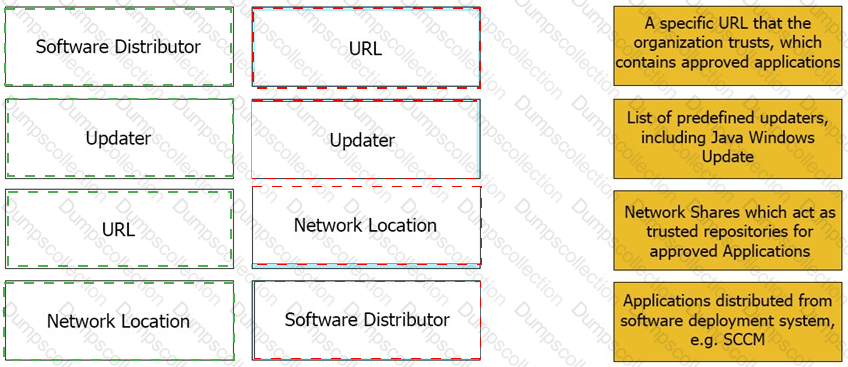
Match the Trusted Source to its correct definition:
When adding the EPM agent to a pre-existing security stack on workstation, what two steps are CyberArk recommendations. (Choose two.)
Where can you view CyberArk EPM Credential Lures events?
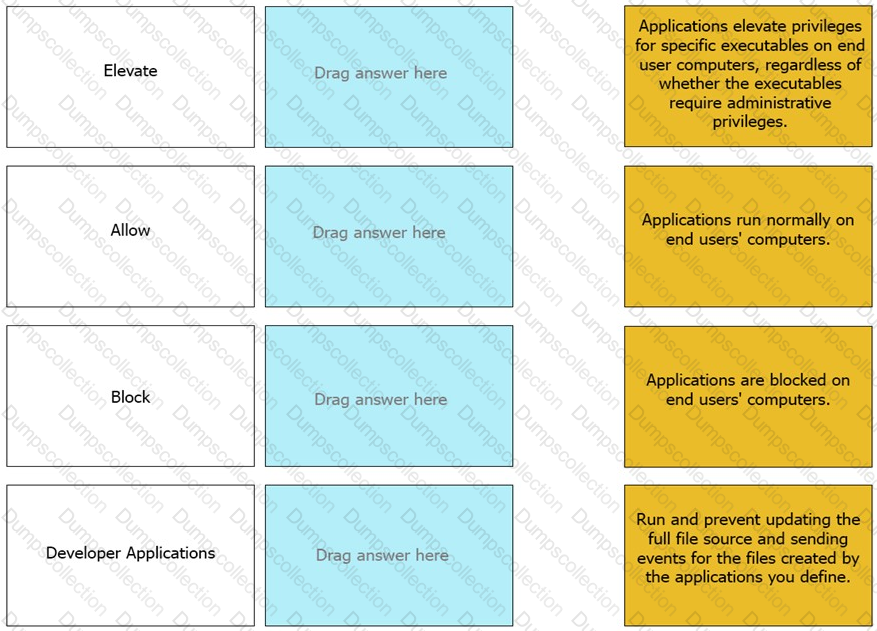
Match the Application Groups policy to their correct description.