ECCouncil Certified SOC Analyst (CSA) 312-39 Exam Dumps: Updated Questions & Answers (January 2026)
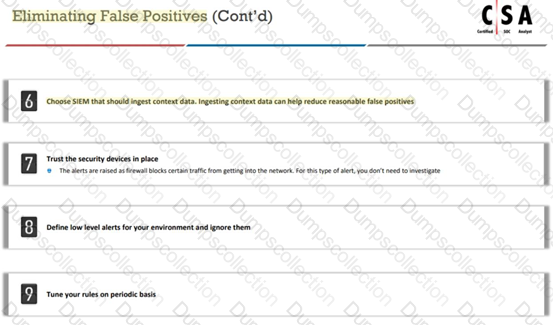
Which of the following can help you eliminate the burden of investigating false positives?
Which of the following tool can be used to filter web requests associated with the SQL Injection attack?
Which of the following data source can be used to detect the traffic associated with Bad Bot User-Agents?
Which of the following is a set of standard guidelines for ongoing development, enhancement, storage, dissemination and implementation of security standards for account data protection?
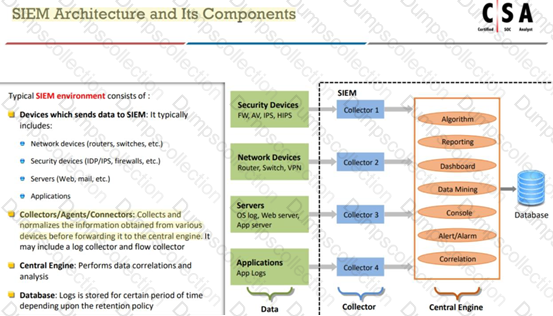
Which of the following are the responsibilities of SIEM Agents?
1.Collecting data received from various devices sending data to SIEM before forwarding it to the central engine.
2.Normalizing data received from various devices sending data to SIEM before forwarding it to the central engine.
3.Co-relating data received from various devices sending data to SIEM before forwarding it to the central engine.
4.Visualizing data received from various devices sending data to SIEM before forwarding it to the central engine.
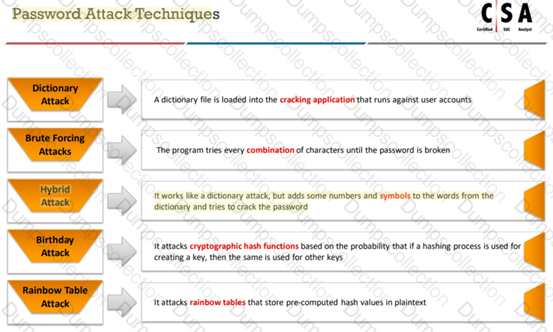
Which attack works like a dictionary attack, but adds some numbers and symbols to the words from the dictionary and tries to crack the password?
Juliea a SOC analyst, while monitoring logs, noticed large TXT, NULL payloads.
What does this indicate?
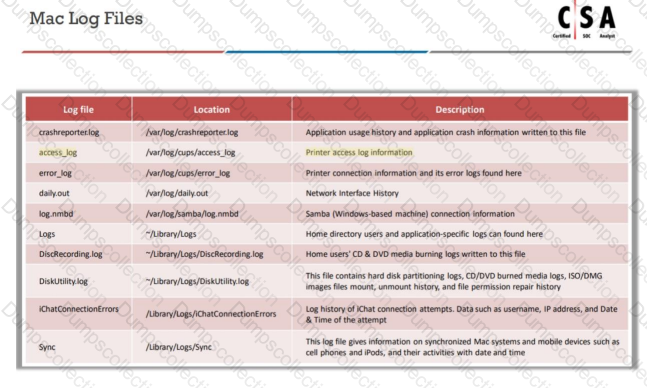
Which of the following directory will contain logs related to printer access?
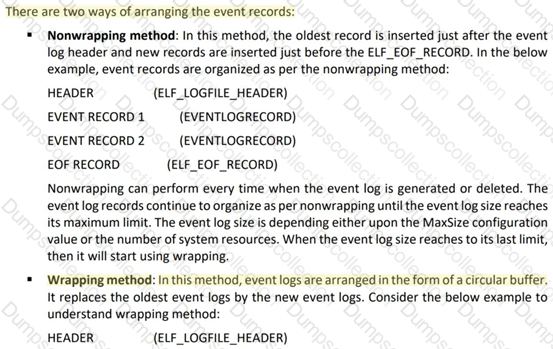
Which of the log storage method arranges event logs in the form of a circular buffer?
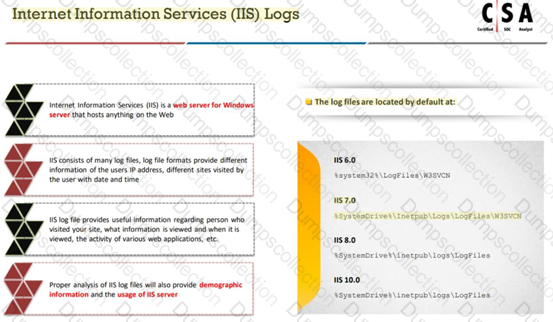
Harley is working as a SOC analyst with Powell Tech. Powell Inc. is using Internet Information Service (IIS) version 7.0 to host their website.
Where will Harley find the web server logs, if he wants to investigate them for any anomalies?

 Graphical user interface
Description automatically generated with low confidence
Graphical user interface
Description automatically generated with low confidence