ECCouncil Computer Hacking Forensic Investigator 312-49 Exam Dumps: Updated Questions & Answers (March 2026)
Which of the following is a device monitoring tool?
Which of the following reports are delivered under oath to a board of directors/managers/panel of the jury?
Madison is on trial for allegedly breaking into her university’s internal network. The police raided her dorm room and seized all of her computer equipment. Madison’s lawyer is trying to convince the judge that the seizure was unfounded and baseless. Under which US Amendment is Madison’s lawyer trying to prove the police violated?
Hard disk data addressing is a method of allotting addresses to each _______ of data on a hard disk.
Which of the following is a responsibility of the first responder?
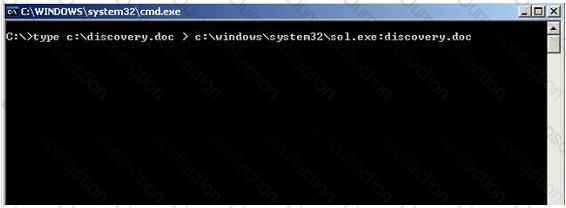
What feature of Windows is the following command trying to utilize?
Gill is a computer forensics investigator who has been called upon to examine a seized computer. This computer, according to the police, was used by a hacker who gained access to numerous banking institutions to steal customer information. After preliminary investigations, Gill finds in the computer’s log files that the hacker was able to gain access to these banks through the use of Trojan horses. The hacker then used these Trojan horses to obtain remote access to the companies’ domain controllers. From this point, Gill found that the hacker pulled off the SAM files from the domain controllers to then attempt and crack network passwords. What is the most likely password cracking technique used by this hacker to break the user passwords from the SAM files?
Using Linux to carry out a forensics investigation, what would the following command accomplish?
dd if=/usr/home/partition.image of=/dev/sdb2 bs=4096 conv=notrunc,noerror
Which of the following commands shows you all of the network services running on Windows-based servers?
A state department site was recently attacked and all the servers had their disks erased. The incident response team sealed the area and commenced investigation. During evidence collection they came across a zip disks that did not have the standard labeling on it. The incident team ran the disk on an isolated system and found that the system disk was accidentally erased. They decided to call in the FBI for further investigation. Meanwhile, they short listed possible suspects including three summer interns. Where did the incident team go wrong?
The offset in a hexadecimal code is:
What type of attack occurs when an attacker can force a router to stop forwarding packets by flooding the router with many open connections simultaneously so that all the hosts behind the router are effectively disabled?
Which of the following registry hive gives the configuration information about which application was used to open various files on the system?
In the following directory listing,
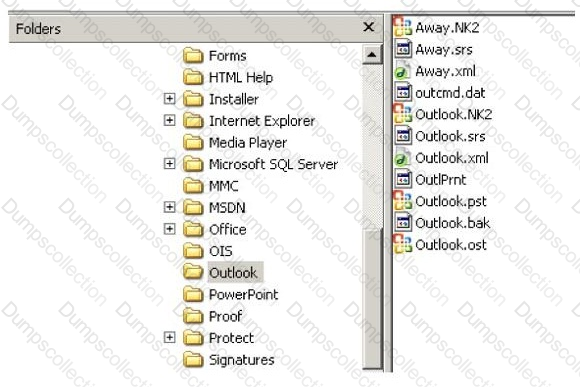
Which file should be used to restore archived email messages for someone using Microsoft Outlook?
What should you do when approached by a reporter about a case that you are working on or have worked on?

