ECCouncil EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing ECSAv10 Exam Dumps: Updated Questions & Answers (March 2026)
Identify the person who will lead the penetration-testing project and be the client point of contact.
Identify the correct formula for Return on Investment (ROI).
What is the following command trying to accomplish?
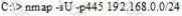
Which of the following reports provides a summary of the complete pen testing process, its outcomes, and recommendations?
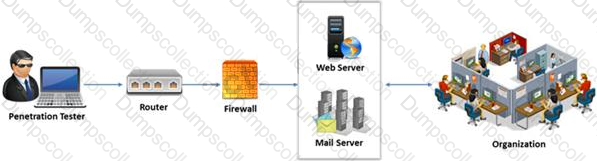
External penetration testing is a traditional approach to penetration testing and is more focused on the servers, infrastructure and the underlying software comprising the target. It involves a comprehensive analysis of publicly available information about the target, such as Web servers, Mail servers, Firewalls, and Routers.
Which of the following types of penetration testing is performed with no prior knowledge of the site?
What is the target host IP in the following command?
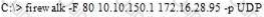
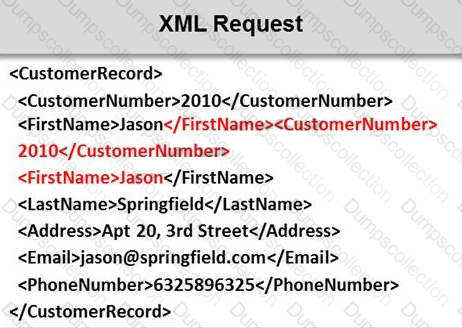
Identify the injection attack represented in the diagram below:
Which of the following attacks does a hacker perform in order to obtain UDDI information such as businessEntity, businesService, bindingTemplate, and tModel?
Which one of the following is a supporting tool for 802.11 (wireless) packet injections, it spoofs 802.11 packets to verify whether the access point is valid or not?
DMZ is a network designed to give the public access to the specific internal resources and you might want to do the same thing for guests visiting organizations without compromising the integrity of the internal resources. In general, attacks on the wireless networks fall into four basic categories.
Identify the attacks that fall under Passive attacks category.

