EMC Dell PowerProtect Cyber Recovery Deploy v2 Exam D-PCR-DY-01 Exam Dumps: Updated Questions & Answers (March 2026)
What is a key technological limitation that warrants the use of an air-gapped vault in dell PowerProtect Cyber Recovery?
What are the three characteristics of CyberSense? (Choose three.)
Which application object is required in the Dell PowerProtect Cyber Recovery vault to perform data analysis for malware or anomalies?
You execute the crsetup.sh --check command to upgrade the Dell PowerProtect Cyber Recovery software using the precheck option.
What is the first check that the update precheck performs?
What is a pre-requisite for performing Automated Recovery of Dell PowerProtect Data Manager?
After successfully completing the PoC for the Dell PowerProtect Cyber Recovery solution with Dell APEX Protection Storage All-Flash, the customer decided to purchase a license for the further use in the production environment.
Which information is required to generate the License Authorization Code (LAC) for the Dell APEX Protection Storage instance?
An IT manager needs to rerun a previously generated Dell PowerProtect Cyber Recovery report to verify the job activities for a specific period. They want to ensure that report includes the latest data.
What action should the IT manager take to rerun the report?
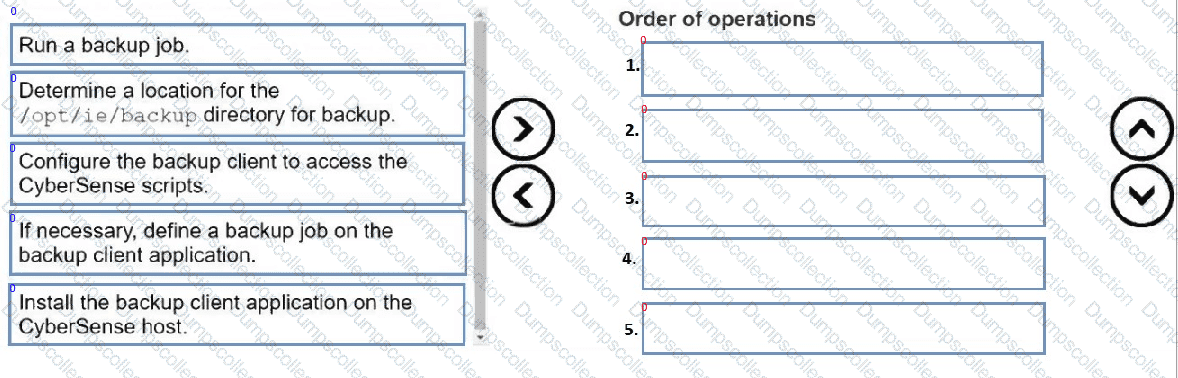
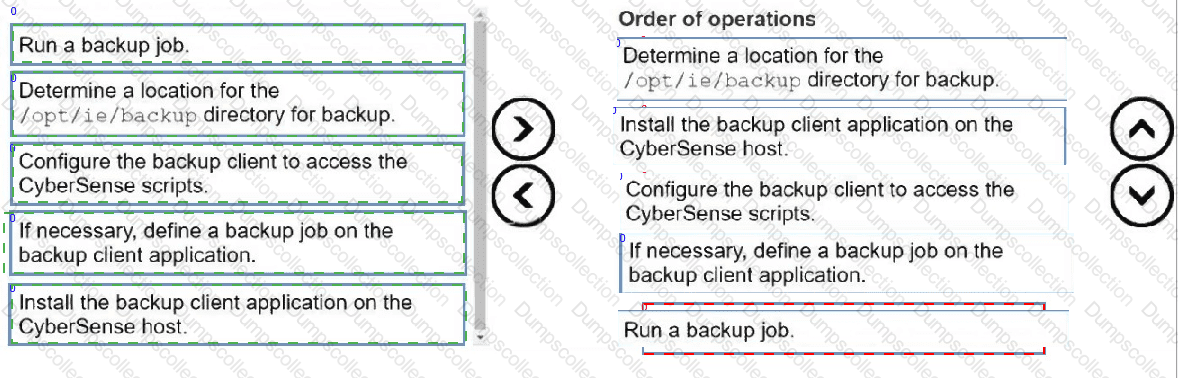
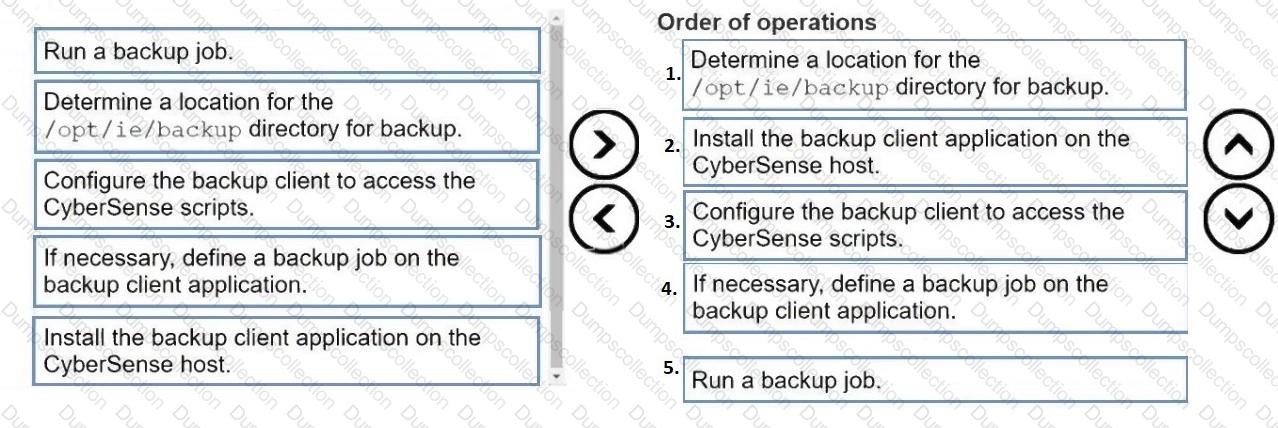
DRAG DROP
Put the following steps in the correct order to back up the Index Engines CyberSense configuration files:
Which is the best practice when securing PowerProtect Data Domain in Dell PowerProtect Cyber Recovery vault?
Which common cyber-attack overwhelms the resources of the system with excessive requests that consume all the resources to bring it down?

 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg