Fortinet FCP - Secure Wireless LAN 7.4 Administrator FCP_FWF_AD-7.4 Exam Dumps: Updated Questions & Answers (March 2026)
Which security solution can you implement in the Security Fabric to identify and prevent threats?
Which two statements are correct about FortiAP and rogue APs? (Choose two.)
Which two rotes does FortiPresence analytics assist in generating presence reports'' (Choose two.)
Which two threats on wireless networks are detected by WIDS? (Choose two.)
You plan to deploy a wireless network at various remote sites with no on-site IT available. The remote sites must have access points to broadcast the wireless networks You can manage the access points using any Fortinet control and management option
Which two items must you consider in addition to deploying the wireless network and enforcing Fortinet UTM on all wireless traffic? (Choose two.)
How can you find the upstream and downstream link rates of a wireless client connected to a FortiAP?
Which wireless monitoring metric is required to optimize a wireless network?
Exhibit.
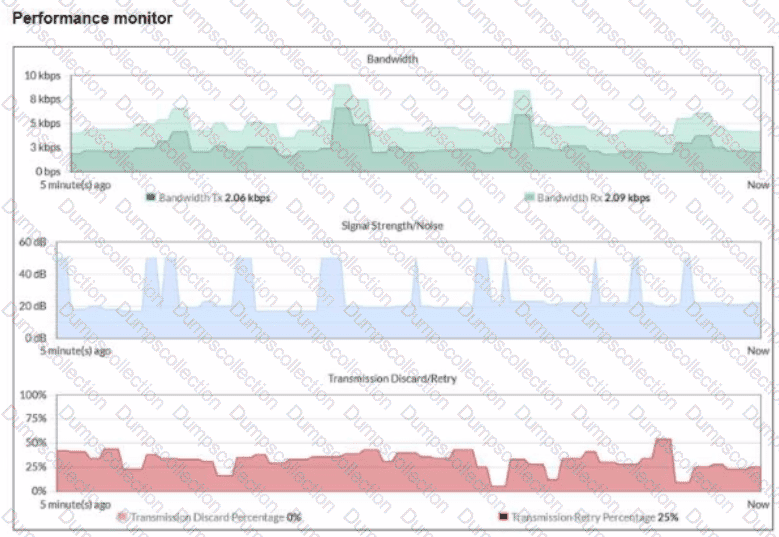
Refer to the exhibit of a wireless client performance monitor Which performance metric is abnormal for this wireless client?
A wireless station has reported several connection issues with FortiAP that have not been resolved using standard troubleshooting tools As a wireless network administrator you are planning to perform additional advanced-level troubleshooting Which two steps must you take to analyze and troubleshoot the issue? (Choose two)

