Fortinet Fortinet NSE 7 - Enterprise Firewall 7.6 Administrator FCSS_EFW_AD-7.6 Exam Dumps: Updated Questions & Answers (February 2026)
An administrator is setting up an ADVPN configuration and wants to ensure that peer IDs are not exposed during VPN establishment.
Which protocol can the administrator use to enhance security?
An administrator must enable direct communication between multiple spokes in a company's network. Each spoke has more than one internet connection.
The requirement is for the spokes to connect directly without passing through the hub, and for the links to automatically switch to the best available connection.
How can this automatic detection and optimal link utilization between spokes be achieved?
Refer to the exhibit.
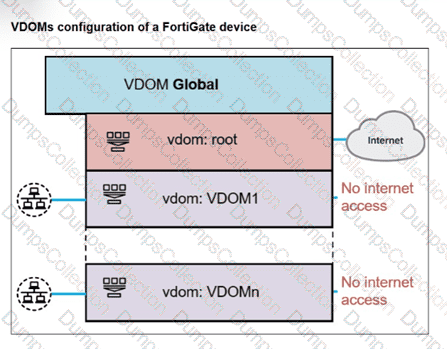
A FortiGate segmented into VDOMs is shown. You must ensure effective and accelerated internet access for all of the VDOMs in this enterprise network. How can you achieve this? (Choose one answer)
Refer to the exhibit, which shows the ADVPN network topology and partial BGP configuration.
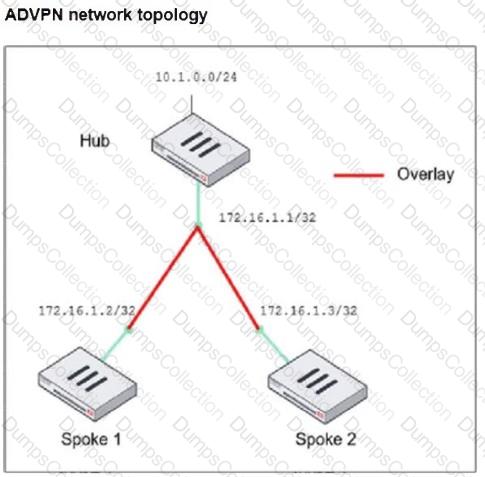

Which two parameters must an administrator configure in the config neighbor range for spokes shown in the exhibit? (Choose two.)
An administrator is checking an enterprise network and sees a suspicious packet with the MAC address e0:23:ff:fc:00:86.
What two conclusions can the administrator draw? (Choose two.)
Refer to the exhibit, which shows the ADVPN IPsec interface representing the VPN IPsec phase 1 from Hub A to Spoke 1 and Spoke 2, and from Hub В to Spoke 3 and Spoke 4.
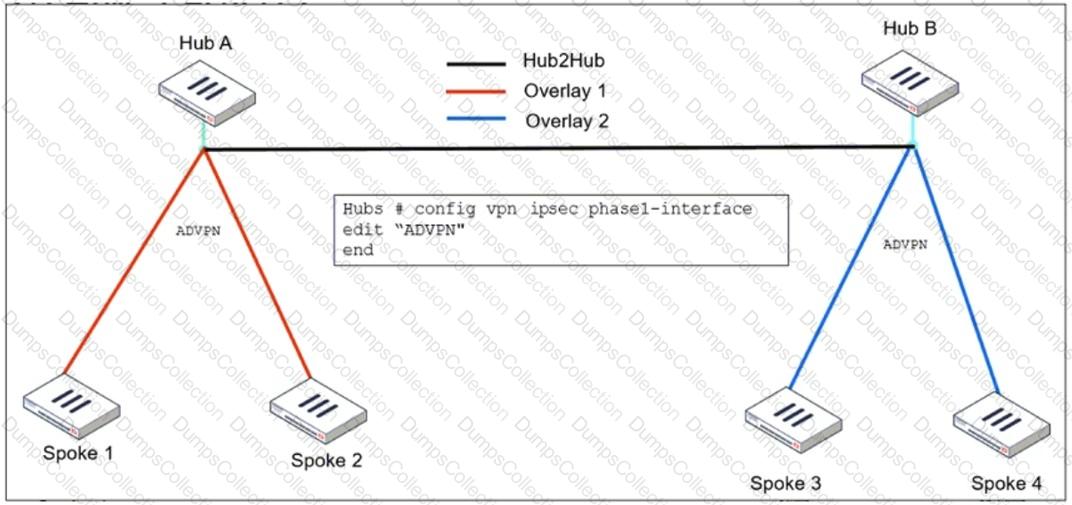
An administrator must configure an ADVPN using IBGP and EBGP to connect overlay network 1 with 2.
What must the administrator configure in the phase 1 VPN IPsec configuration of the ADVPN tunnels?
Refer to the exhibit.
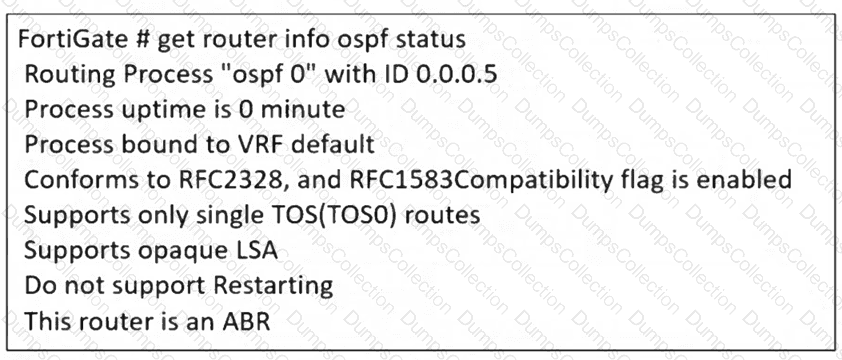
The partial output of an OSPF command is shown. While checking the OSPF status of FortiGate, you receive the output shown in the exhibit. Based on the output, which two statements about FortiGate are correct? (Choose two answers)
Refer to the exhibit, which contains a partial command output.
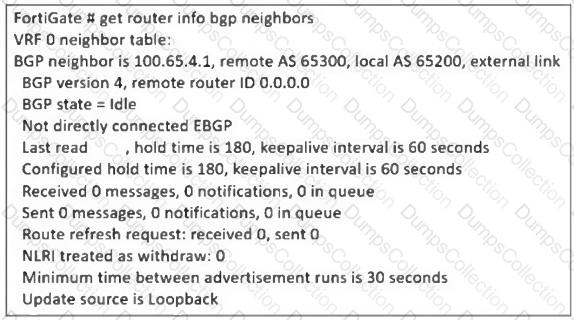
The administrator has configured BGP on FortiGate. The status of this new BGP configuration is shown in the exhibit.
What configuration must the administrator consider next?
Refer to the exhibit, which shows a corporate network and a new remote office network.
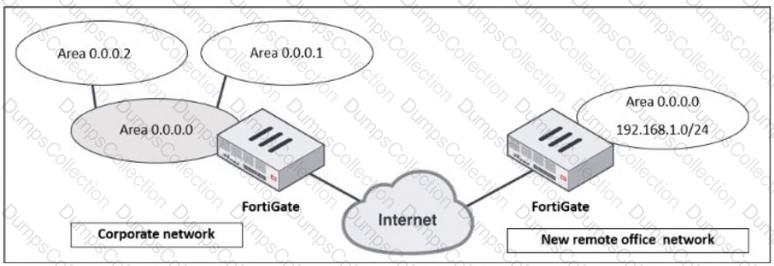
An administrator must integrate the new remote office network with the corporate enterprise network.
What must the administrator do to allow routing between the two networks?
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)

