Fortinet FCSS - FortiSASE 24 Administrator FCSS_SASE_AD-24 Exam Dumps: Updated Questions & Answers (March 2026)
During FortiSASE provisioning, how many security points of presence (POPs) need to be configured by the FortiSASE administrator?
Which two statements describe a zero trust network access (ZTNA) private access use case? (Choose two.)
When viewing the daily summary report generated by FortiSASE, the administrator notices that the report contains very little data.
What is a possible explanation for this almost empty report?
Refer to the exhibit.
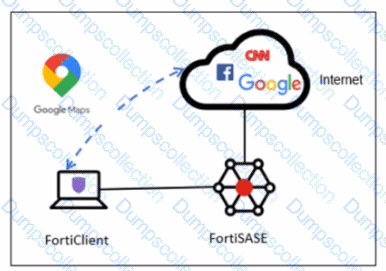
A company has a requirement to inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical Interface.
Which configuration must you apply to achieve this requirement?
Refer to the exhibit.
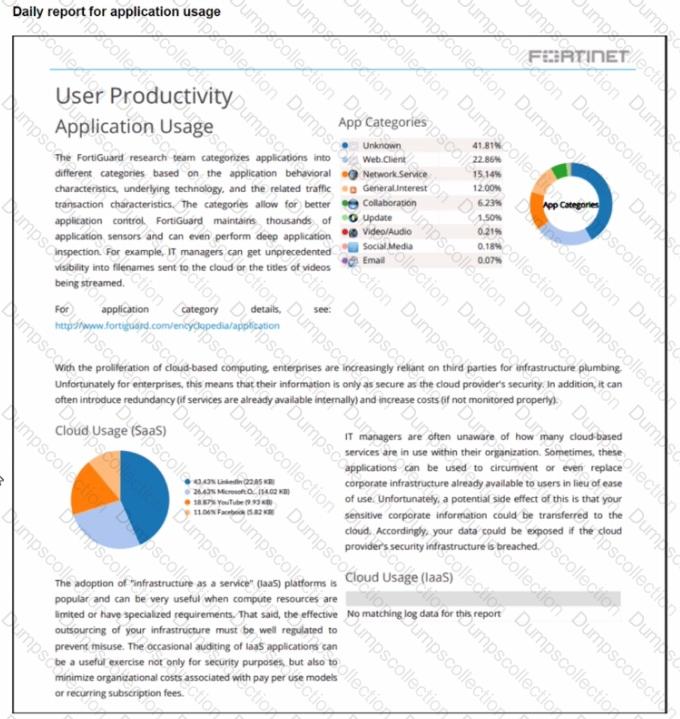
The daily report for application usage shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
What are two advantages of using zero-trust tags? (Choose two.)
Which event log subtype captures FortiSASE SSL VPN user creation?
When accessing the FortiSASE portal for the first time, an administrator must select data center locations for which three FortiSASE components? (Choose three.)
How does FortiSASE hide user information when viewing and analyzing logs?
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
In this scenario, which three setups will achieve the above requirements? (Choose three.)

