Fortinet FCSS - FortiSASE 25 Administrator FCSS_SASE_AD-25 Exam Dumps: Updated Questions & Answers (February 2026)
Refer to the exhibit.
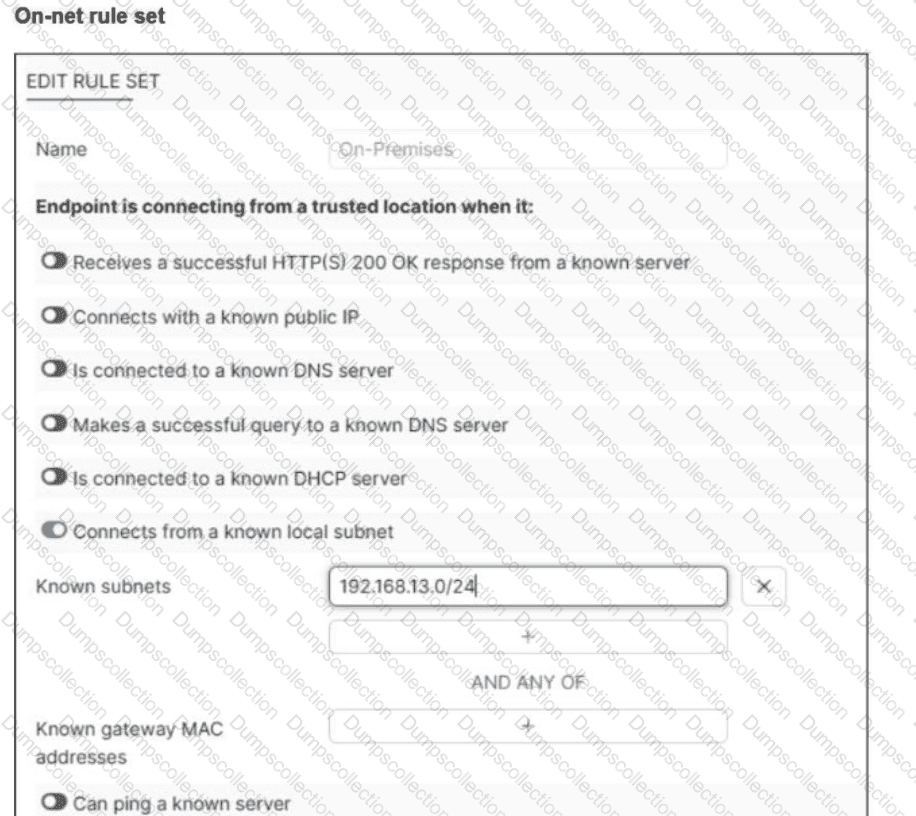
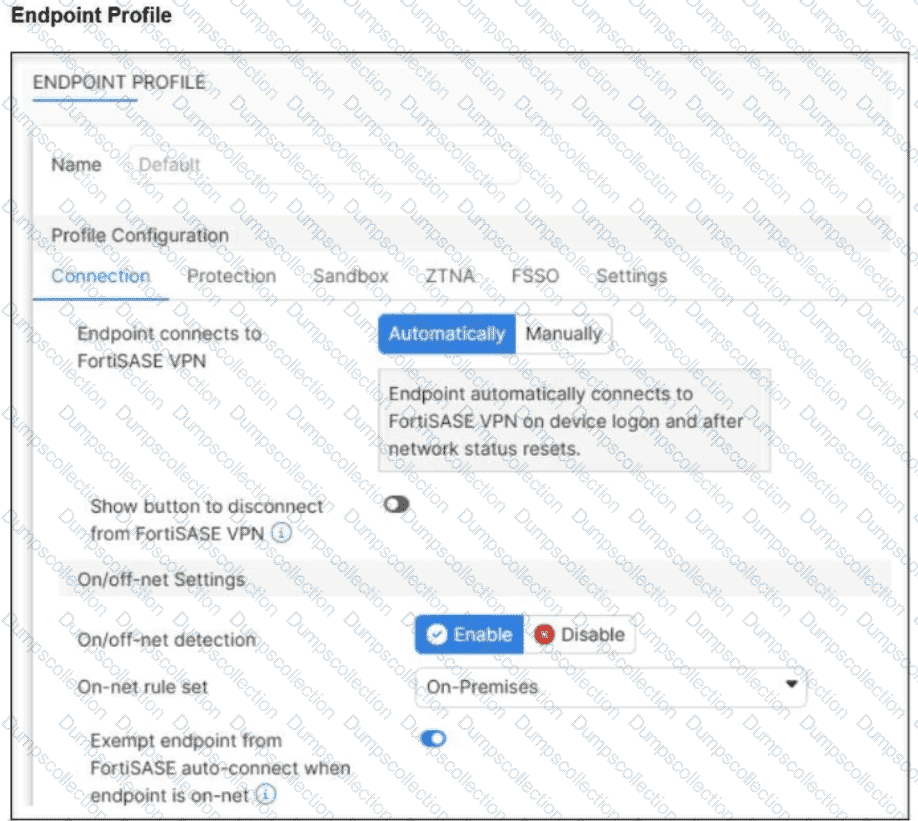
An endpoint is assigned an IP address of 192.168.13.101/24.
Which action will be run on the endpoint?
Refer to the exhibit.
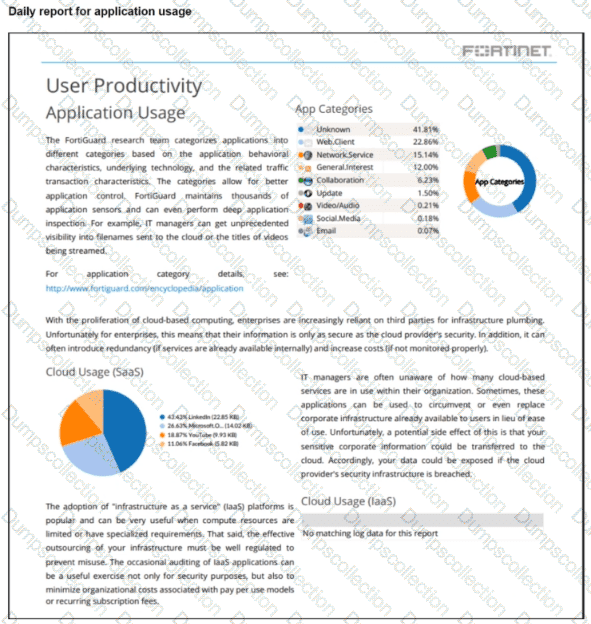
The daily report for application usage for internet traffic shows an unusually high number of unknown applications by category.
What are two possible explanations for this? (Choose two.)
Which statement applies to a single sign-on (SSO) deployment on FortiSASE?
Refer to the exhibits.
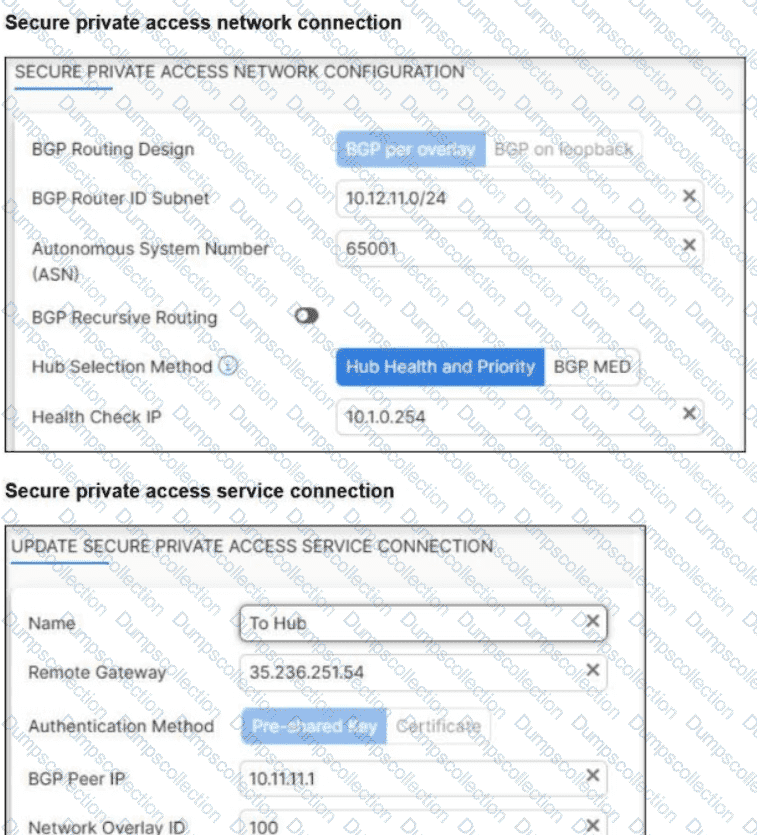
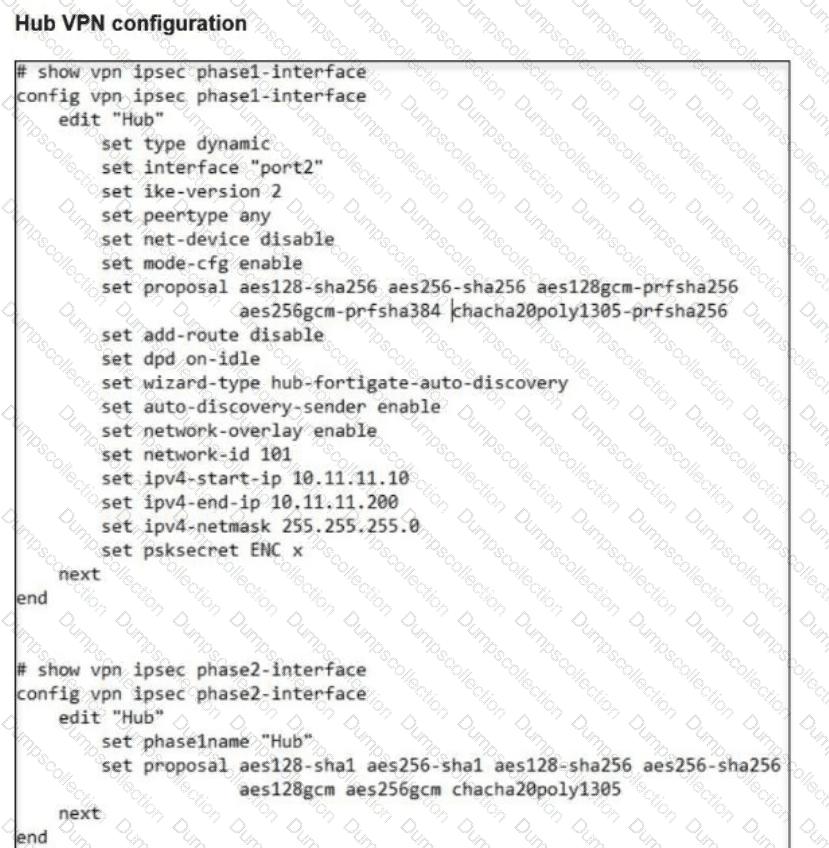
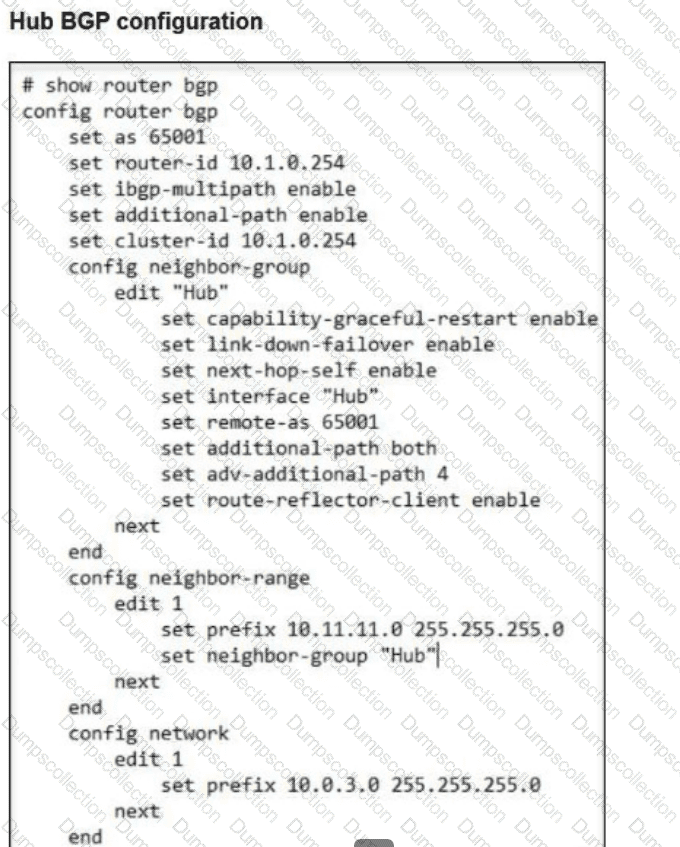

A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub.
The VPN tunnel does not establish.
Which configuration needs to be modified to bring the tunnel up?
What are two benefits of deploying secure private access with SD-WAN? (Choose two.)
Which two additional features does FortiClient integration provide with FortiSASE, when compared to secure web gateway (SWG) deployment? (Choose two.)
Which authentication method overrides any other previously configured user authentication on FortiSASE?
Your organization is currently using FortiSASE for its cybersecurity. They have recently hired a contractor who will work from the HQ office and who needs temporary internet access in order to set up a web-based point of sale (POS) system.
What is the recommended way to provide internet access to the contractor?
Which two purposes is the dedicated IP address used for in a FortiSASE deployment? (Choose two.)
Refer to the exhibits.
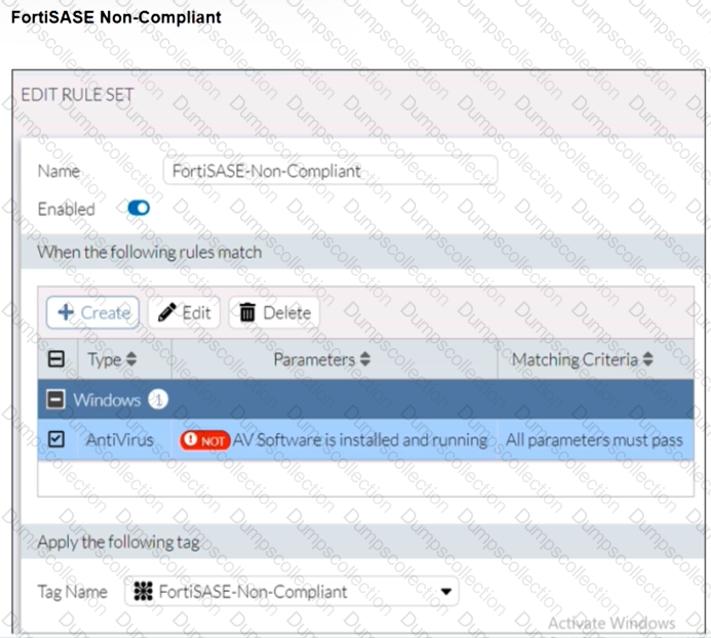
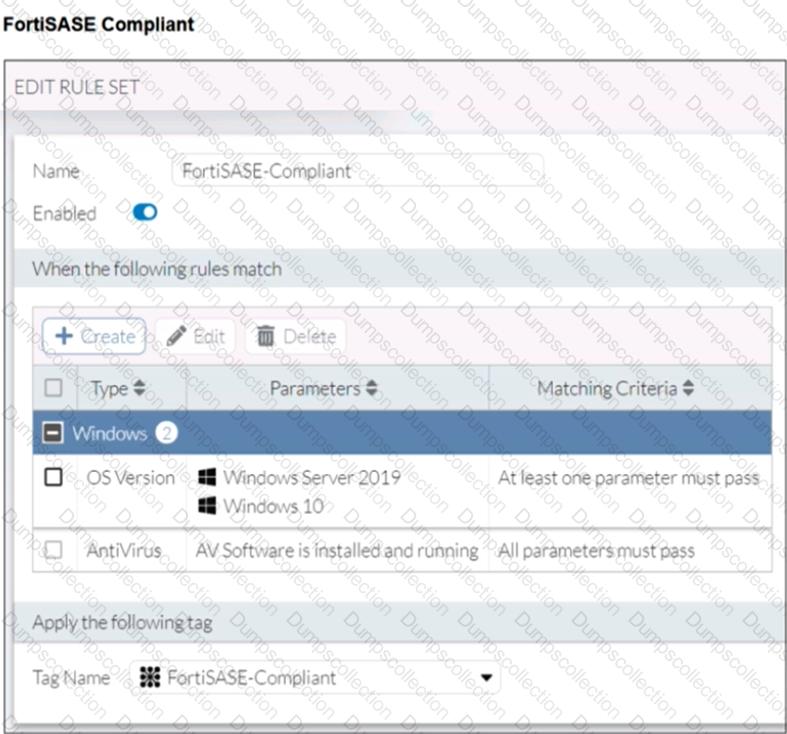
Antivirus is installed on a Windows 10 endpoint, but the windows application firewall is stopping it from running.
What will the endpoint security posture check be?

