Fortinet FCSS - SD-WAN 7.6 Architect FCSS_SDW_AR-7.6 Exam Dumps: Updated Questions & Answers (February 2026)
Refer to the exhibit.
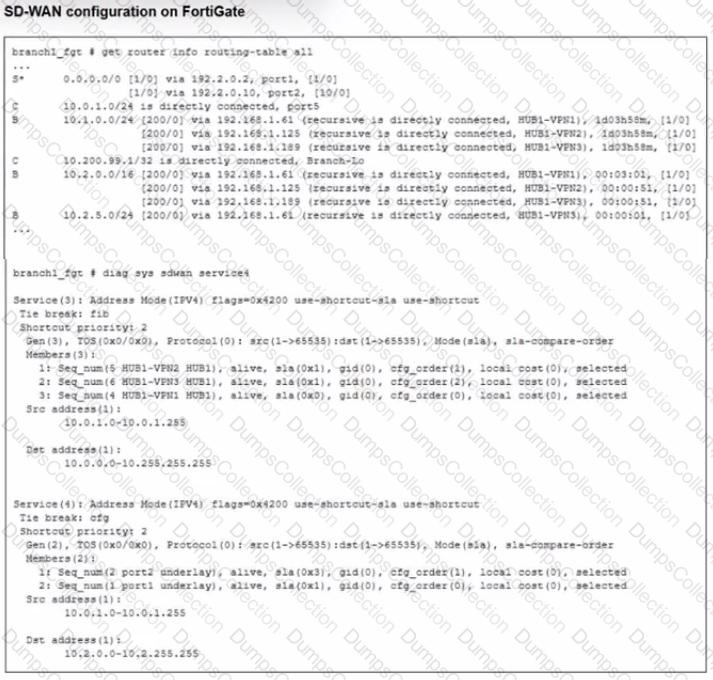
Which SD-WAN rule and interface uses FortiGate to steer the traffic from the LAN subnet 10.0.1.0/24 to the corporate server 10.2.5.254?
(Refer to the exhibits.
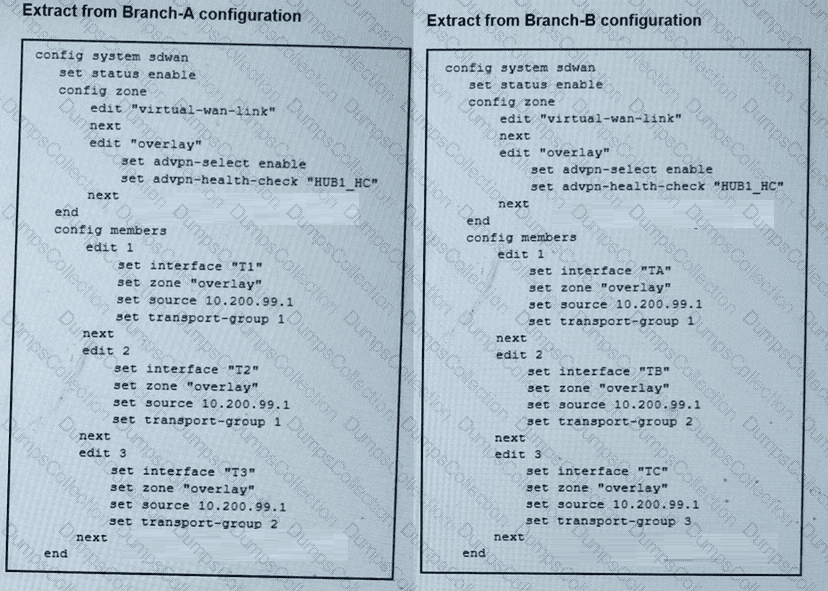
The SD-WAN zones and members configuration of two branch devices are shown. The two branch devices are part of the same hub-and-spoke topology and connect to the same hub. The devices are configured to allow Auto-Discovery VPN (ADVPN). The configuration on the hub allows the initial communication between the two spokes.
When traffic flows require it, between which interfaces can the devices establish shortcuts? Choose one answer.)
(In which order does FortiGate consider the following elements during the route lookup process? Choose one answer.)
Refer to the exhibit.
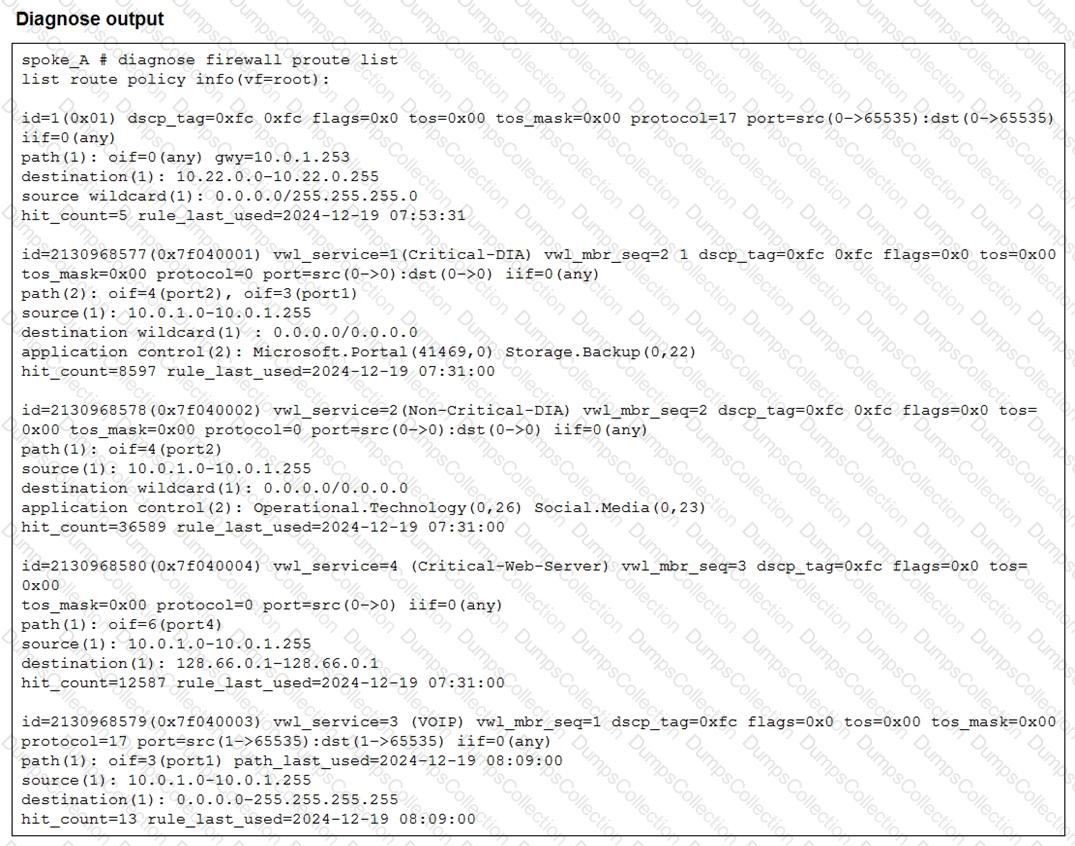
Which two conclusions can you draw from the output shown? (Choose two.)
Refer to the exhibits, which show the configuration of an SD-WAN rule and the corresponding rule status and routing table.

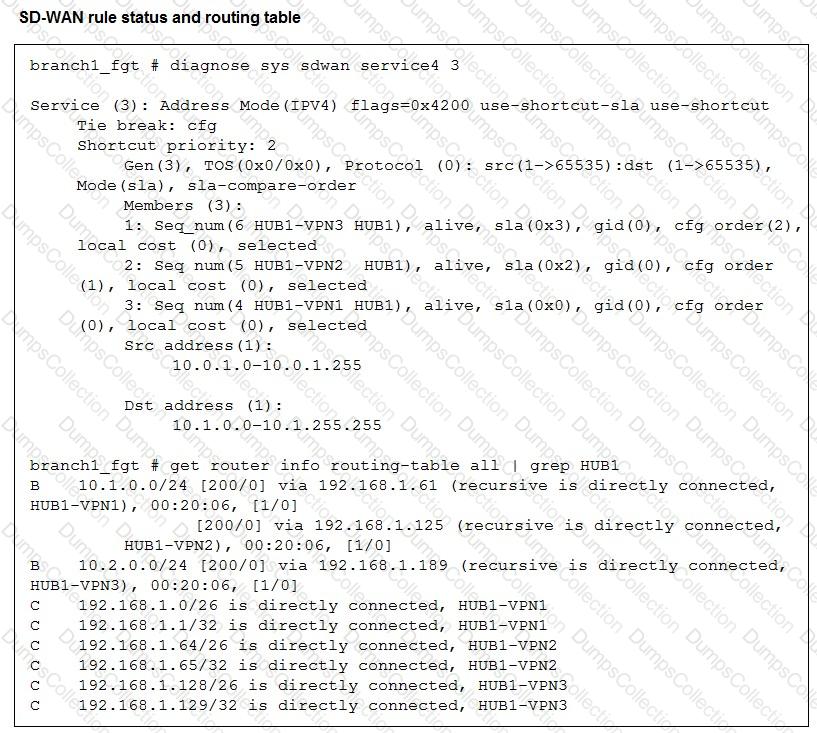
The administrator wants to understand the expected behavior for traffic matching the SD-WAN rule.
Based on the exhibits, what can the administrator expect for traffic matching the SD-WAN rule?
(Refer to the exhibit.
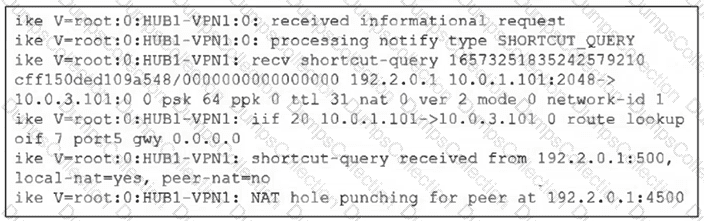
Which statement correctly describes the role of the ADVPN device in handling traffic? Choose one answer.)
Refer to the exhibits.
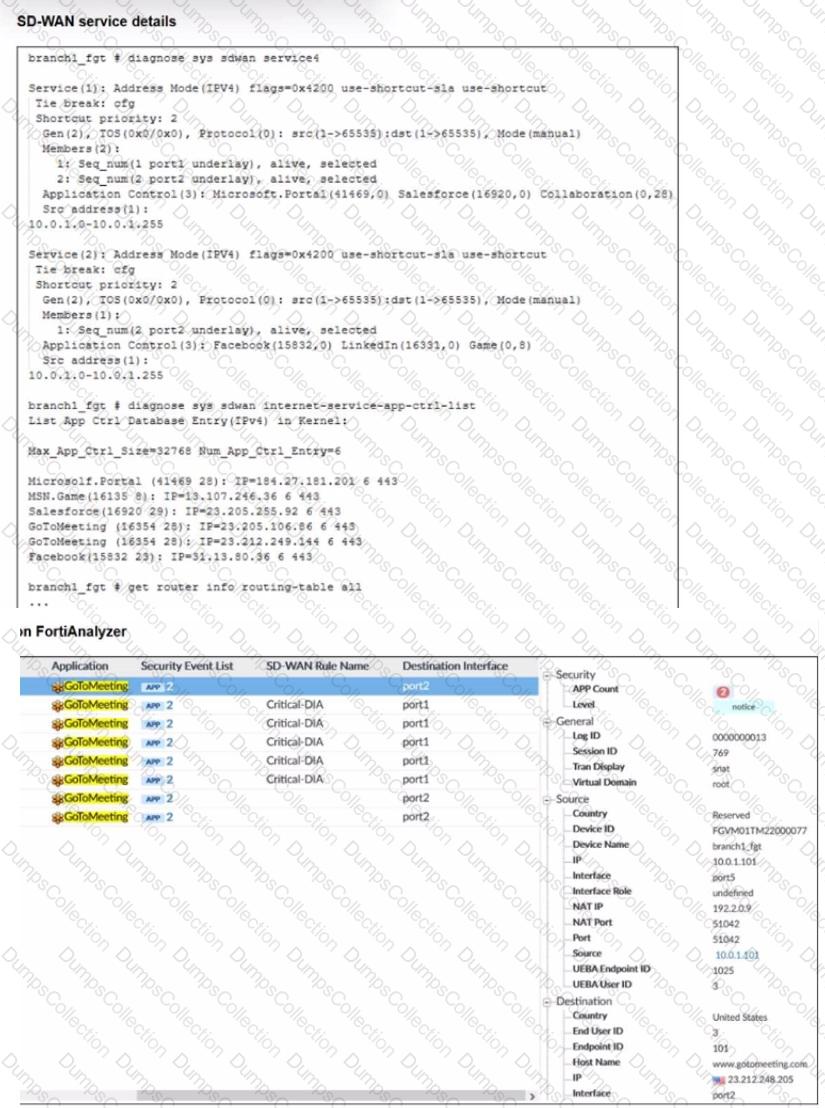
An administrator is testing application steering in SD-WAN. Before generating test traffic, the administrator collected the information shown in the first exhibit. After generating GoToMeeting test traffic, the administrator examined the corresponding traffic log on FortiAnalyzer, which is shown in the second exhibit.
The administrator noticed that the traffic matched the implicit SD-WAN rule, but they expected the traffic to match rule ID 1.
Which two reasons explain why some log messages show that the traffic matched the implicit SD-WAN rule? (Choose two.)
Refer to the exhibit.
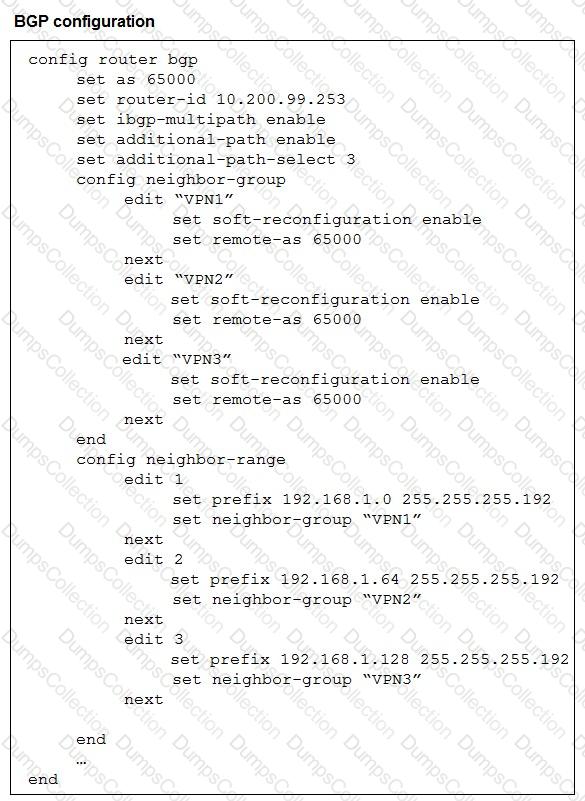
The exhibit shows the BGP configuration on the hub in a hub-and-spoke topology. The administrator wants BGP to advertise prefixes from spokes to other spokes over the IPsec overlays, including additional paths. However, when looking at the spoke routing table, the administrator does not see the prefixes from other spokes and the additional paths
Which three settings must the administrator configure inside each BGP neighbor group so spokes can learn the prefixes of other spokes and their additional paths? (Choose three.)
Refer to the exhibit.

The exhibit shows output of the command diagnose sys adwan aervice4 collected on a FortiGate device.
The administrator wants to know through which interface FortiGate will steer traffic from local users on subnet 10.0.1.0/255.255.255.192 and with a destination of the social media application Facebook.
Based on the exhibits, which two statements are correct? (Choose two.)
Which three characteristics apply to provisioning templates available on FortiManager? (Choose three.)

