Fortinet FCSS - Security Operations 7.4 Analyst FCSS_SOC_AN-7.4 Exam Dumps: Updated Questions & Answers (March 2026)
Which role does a threat hunter play within a SOC?
Exhibit:
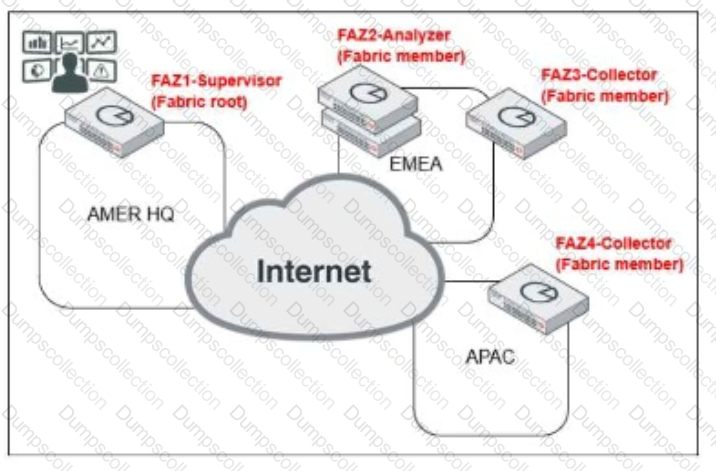
Which observation about this FortiAnalyzer Fabric deployment architecture is true?
Refer to the exhibits.
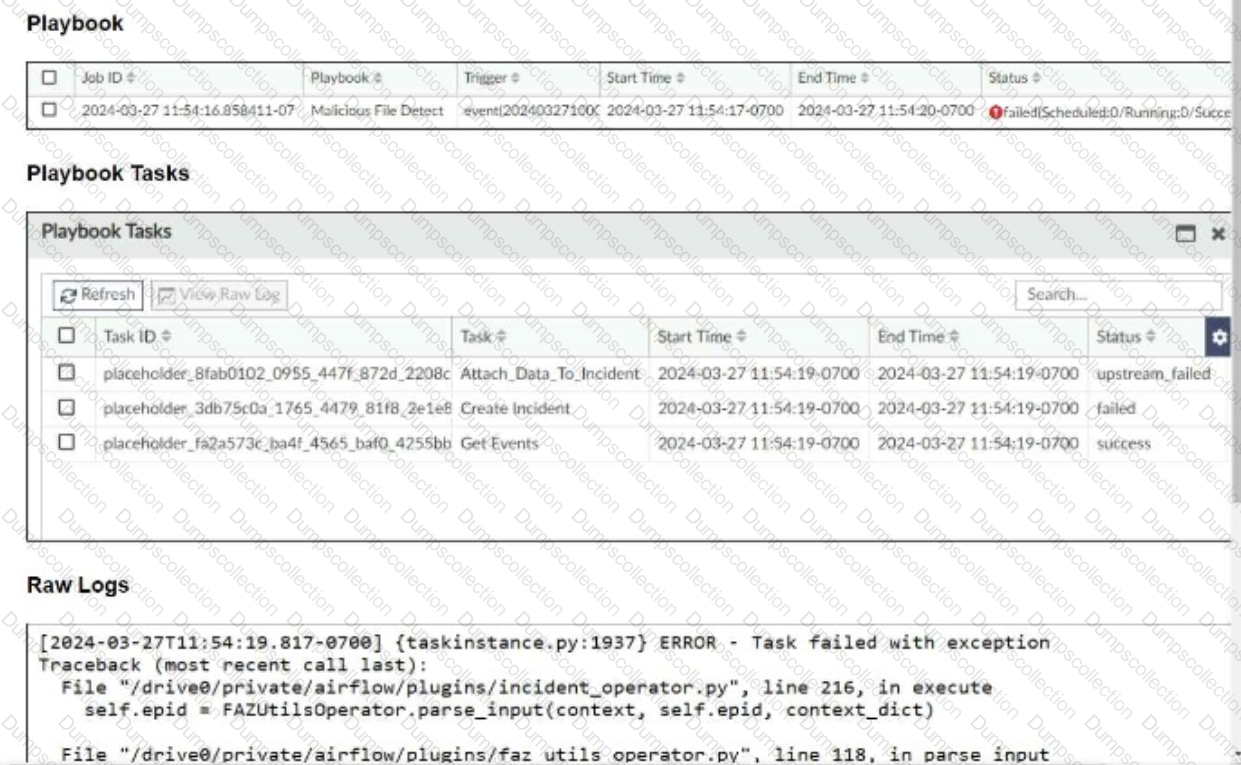
The Malicious File Detect playbook is configured to create an incident when an event handler generates a malicious file detection event.
Why did the Malicious File Detect playbook execution fail?
Which statement best describes the MITRE ATT&CK framework?
Refer to the exhibits.
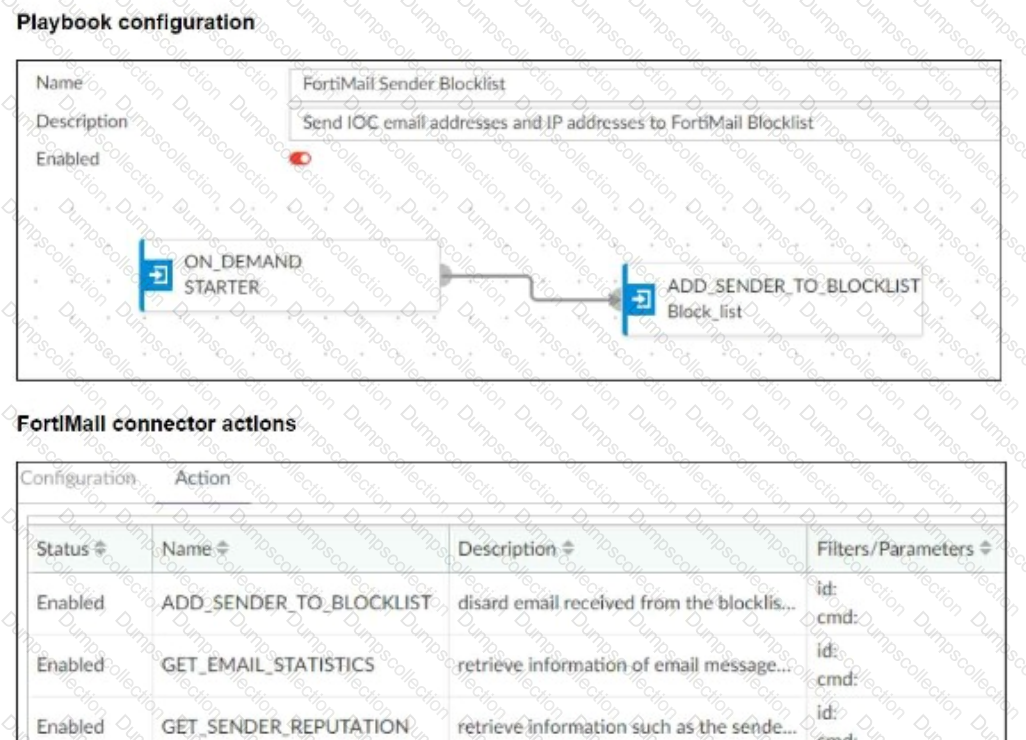
The FortiMail Sender Blocklist playbook is configured to take manual input and add those entries to the FortiMail abc. com domain-level block list. The playbook is configured to use a FortiMail connector and the ADD_SENDER_TO_BLOCKLIST action.
Why is the FortiMail Sender Blocklist playbook execution failing7
Refer to Exhibit:
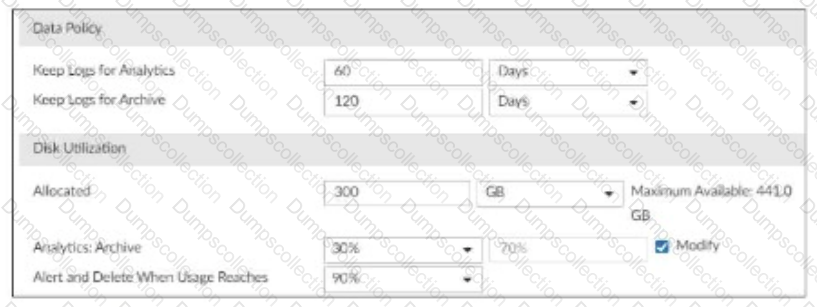
You are tasked with reviewing a new FortiAnalyzer deployment in a network with multiple registered logging devices. There is only one FortiAnalyzer in the topology.
Which potential problem do you observe?
Which FortiAnalyzer feature uses the SIEM database for advance log analytics and monitoring?
Refer to the Exhibit:
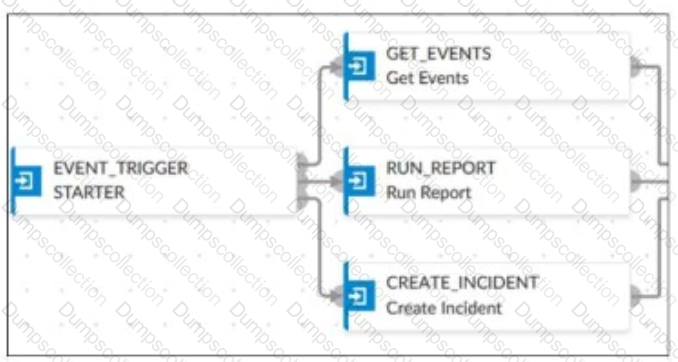
An analyst wants to create an incident and generate a report whenever FortiAnalyzer generates a malicious attachment event based on FortiSandbox analysis. The endpoint hosts are protected by FortiClient EMS integrated with FortiSandbox. All devices are logging to FortiAnalyzer.
Which connector must the analyst use in this playbook?
Refer to the exhibit.
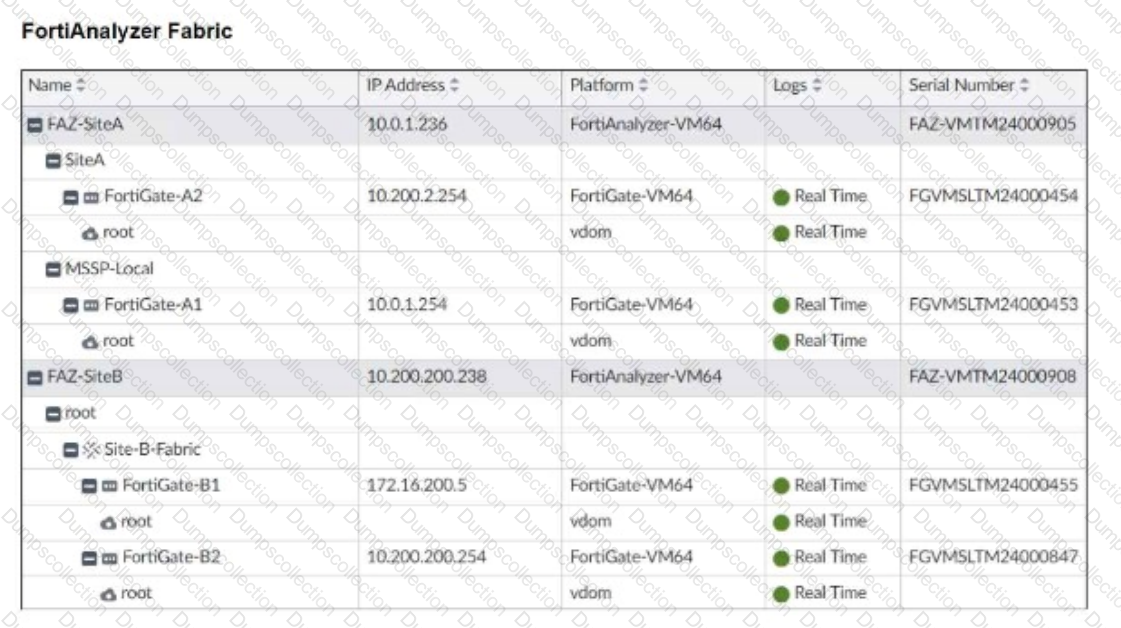
Assume that all devices in the FortiAnalyzer Fabric are shown in the image.
Which two statements about the FortiAnalyzer Fabric deployment are true? (Choose two.)

