Fortinet Fortinet NSE 6 - FortiMail 7.2 NSE6_FML-7.2 Exam Dumps: Updated Questions & Answers (March 2026)
Refer to the exhibit, which shows an inbound recipient policy.
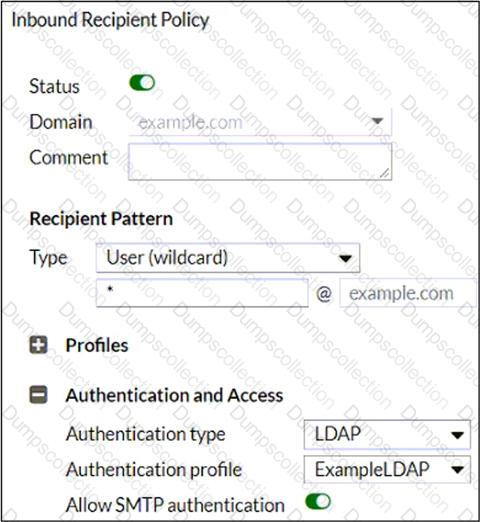
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
Refer to the exhibit, which shows a few lines of FortiMail logs.
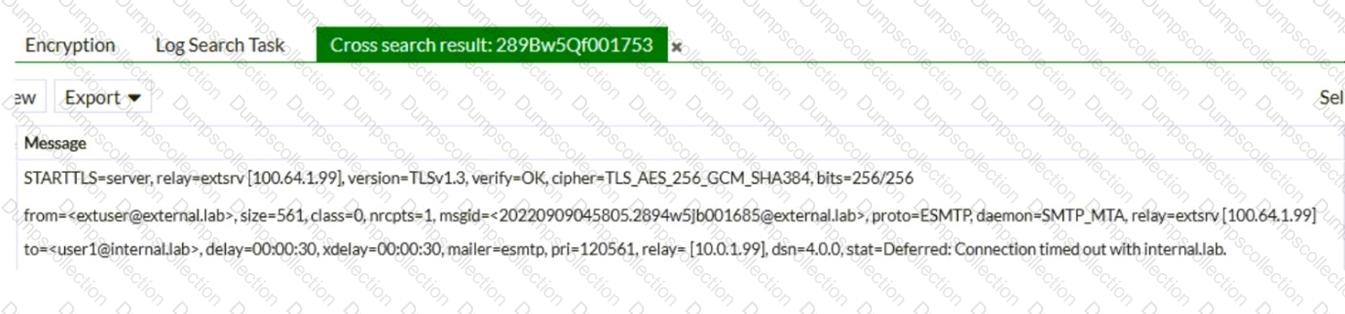
Based on these log entries, which two statements correctly describe the operational status of this FortiMail device? (Choose two.)
Refer to the exhibit which displays a topology diagram.
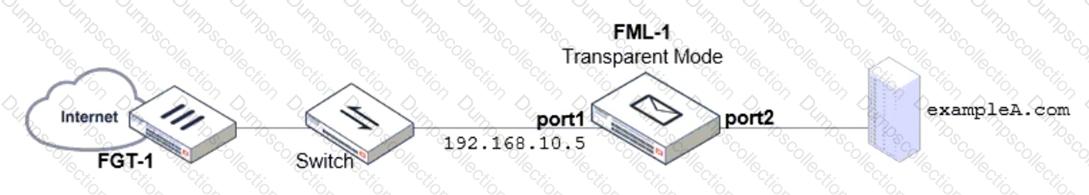
Which two statements describe the built-in bridge functionality on a transparent mode FortiMail? (Choose two.)
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9:INTERNAL.
Which two statements describe what this policy ID means? (Choose two.)
Refer to the exhibit, which shows a topology diagram of two separate email domains.
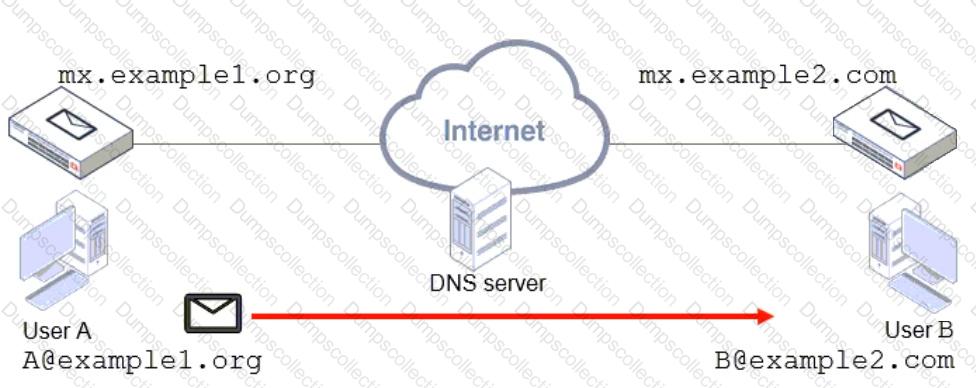
Which two statements correctly describe how an email message is delivered from User A to User B? (Choose two.)
Refer to the exhibit which displays a history log entry.
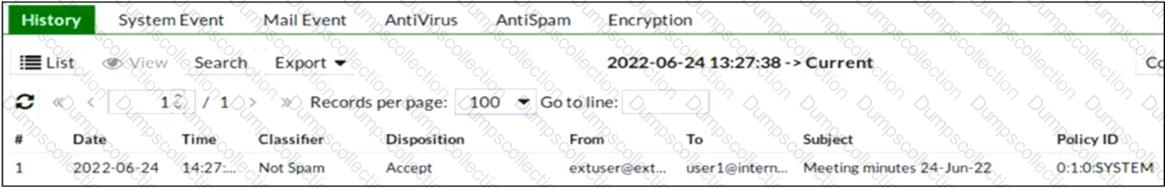
Why does the last field show SYSTEM in the Policy ID column?
Refer to the exhibit which displays the domain configuration of a transparent mode FortiMail device.
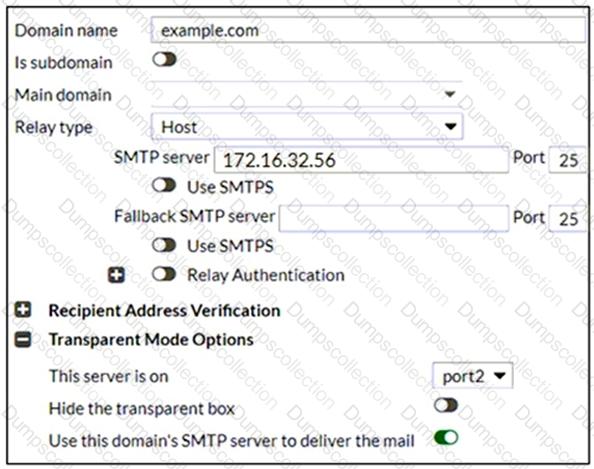
Based on the exhibit, which two sessions are considered incoming sessions? (Choose two.)
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their protected domain. After searching the logs, the administrator identifies that the DSNs were not generated because of any outbound email sent from their organization.
Which FortiMail antispam technique can the administrator use to prevent this scenario?
A FortiMail is configured with the protected domain example.com.
On this FortiMail, which two envelope addresses are considered incoming? (Choose two.)

