Fortinet Fortinet NSE 6 - Secure Wireless LAN 6.4 NSE6_FWF-6.4 Exam Dumps: Updated Questions & Answers (February 2026)
Which statement is correct about security profiles on FortiAP devices?
Refer to the exhibit.
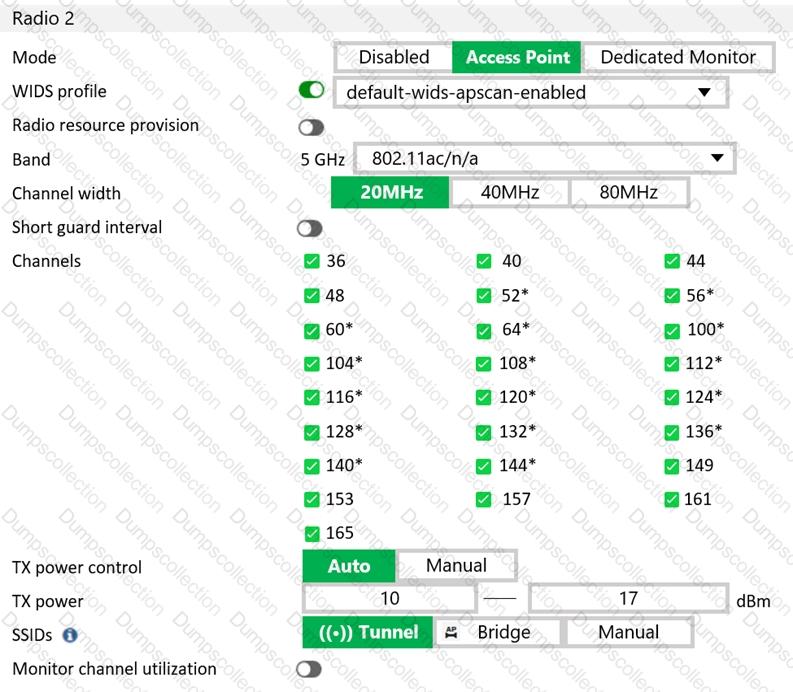
What does the asterisk (*) symbol beside the channel mean?
When enabling security fabric on the FortiGate interface to manage FortiAPs, which two types of communication channels are established between FortiGate and FortiAPs? (Choose two.)
Where in the controller interface can you find a wireless client’s upstream and downstream link rates?
When configuring Auto TX Power control on an AP radio, which two statements best describe how the radio responds? (Choose two.)
When using FortiPresence as a captive portal, which two types of public authentication services can be used to access guest Wi-Fi? (Choose two.)
You are investigating a wireless performance issue and you are trying to audit the neighboring APs in the PF environment. You review the Rogue APs widget on the GUI but it is empty, despite the known presence of other APs.
Which configuration change will allow neighboring APs to be successfully detected?
When deploying a wireless network that is authenticated using EAP PEAP, which two configurations are required? (Choose two.)
Which two statements about distributed automatic radio resource provisioning (DARRP) are correct? (Choose two.)
Which two roles does FortiPresence analytics assist in generating presence reports? (Choose two.)

