Fortinet Fortinet NSE 7 - Public Cloud Security 7.6.4 Architect NSE7_CDS_AR-7.6 Exam Dumps: Updated Questions & Answers (January 2026)
Refer to the exhibit.

You are troubleshooting a Microsoft Azure SDN connector issue on your FortiGate VM in Azure.
Which command can you use to examine details about API calls sent by the connector?
Refer to the exhibit.
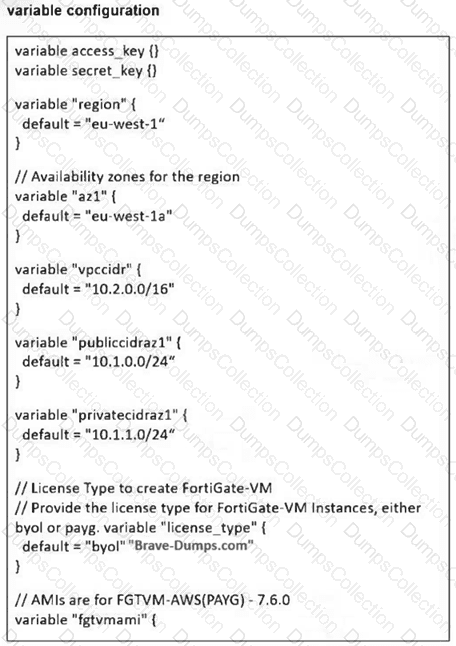
You are tasked to deploy a FortiGate VM with private and public subnets in Amazon Web Services (AWS). You examined the variables.tf file. Assume that all the other terraform files are in place. What will be the final result after running the terraform init and terraform apply commands? (Choose one answer)
Refer to the exhibit.
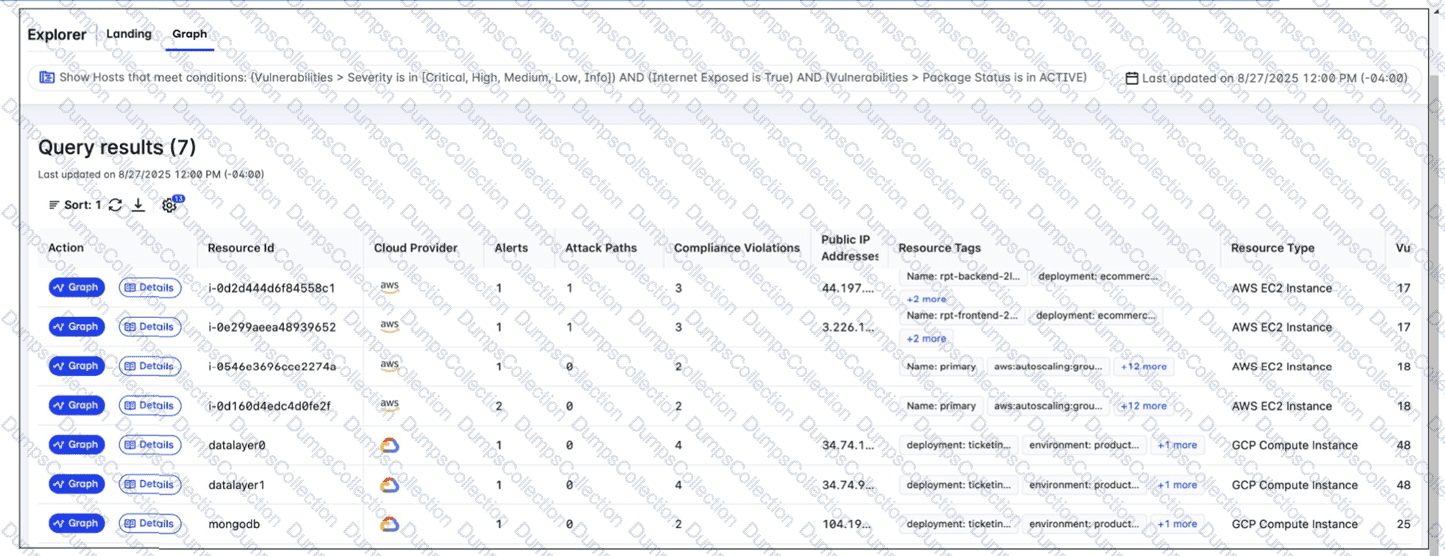
A FortiCNAPP administrator used the FortiCNAPP Explorer to reveal all hosts exposed to the internet that are running active packages with vulnerabilities of all severity levels. Why do only the first two results have an attack path? (Choose one answer)
As part of your organization's monitoring plan, you have been tasked with obtaining and analyzing detailed information about the traffic sourced at one of your FortiGate EC2 instances.
What can you do to achieve this goal?
Refer to the exhibit.

You deployed a FortiGate HA active-passive cluster in Microsoft Azure.
Which two statements regarding this particular deployment are true? (Choose two.)
Refer to the exhibit.
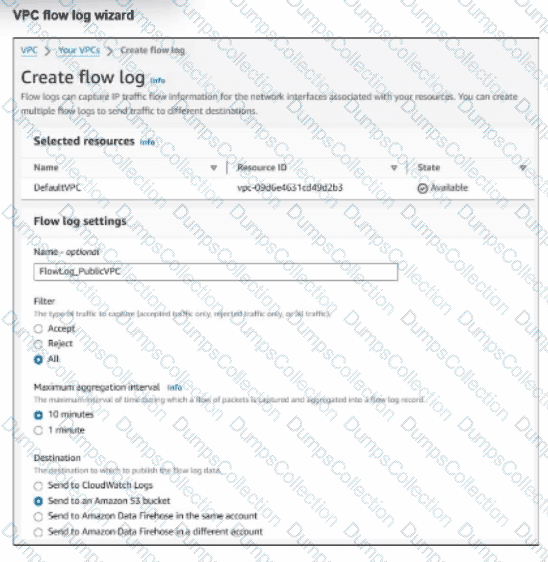
An experienced AWS administrator is creating a new virtual public cloud (VPC) flow log with the settings shown in the exhibit.
What is the purpose of this configuration?
Refer to the exhibit.
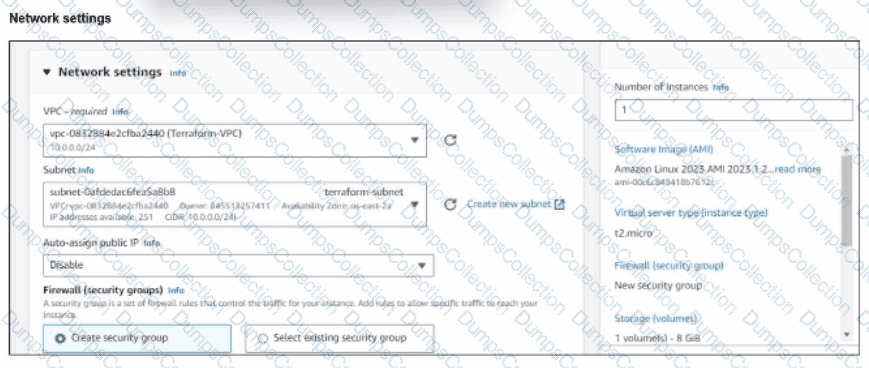
You have deployed a Linux EC2 instance in Amazon Web Services (AWS) with the settings shown on the exhibit.
What next step must the administrator take to access this instance from the internet?
Refer to the exhibit.

After the initial Terraform configuration in Microsoft Azure, the terraform plan command is run.
Which two statements about running the terraform plan command are true? (Choose two.)
What is the main advantage of using SD-WAN Transit Gateway Connect over traditional SD-WAN?
Refer to the exhibit.
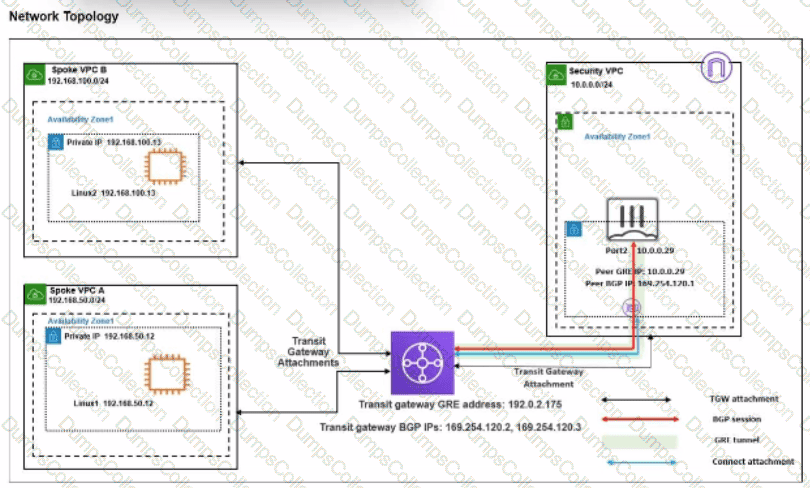
You attempted to access the Linux1 EC2 instance directly from the internet using its public IP address in AWS. However, your connection is not successful.
Given the network topology, what can be the issue?

