Fortinet Fortinet NSE 7 - Security Operations 7.6 Architect NSE7_SOC_AR-7.6 Exam Dumps: Updated Questions & Answers (January 2026)
Refer to the exhibit.
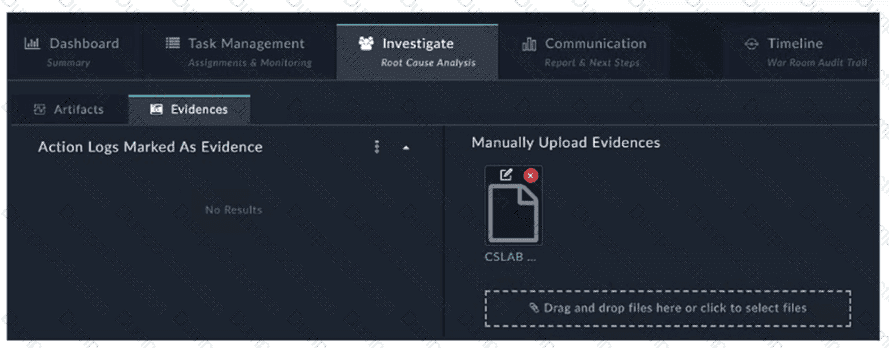
How do you add a piece of evidence to the Action Logs Marked As Evidence area? (Choose one answer)
Refer to the exhibits.
You configured a custom event handler and an associated rule to generate events whenever FortiMail detects spam emails. However, you notice that the event handler is generating events for both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?
When you use a manual trigger to save user input as a variable, what is the correct Jinja expression to reference the variable? (Choose one answer)
A customer wants FortiAnalyzer to run an automation stitch that executes a CLI command on FortiGate to block a predefined list of URLs, if a botnet command-and-control (C&C) server IP is detected.
Which FortiAnalyzer feature must you use to start this automation process?
Which two types of variables can you use in playbook tasks? (Choose two.)
Which three statements accurately describe step utilities in a playbook step? (Choose three answers)
Which two ways can you create an incident on FortiAnalyzer? (Choose two answers)
According to the National Institute of Standards and Technology (NIST) cybersecurity framework, incident handling activities can be divided into phases.
In which incident handling phase do you quarantine a compromised host in order to prevent an adversary from using it as a stepping stone to the next phase of an attack?
When does FortiAnalyzer generate an event?
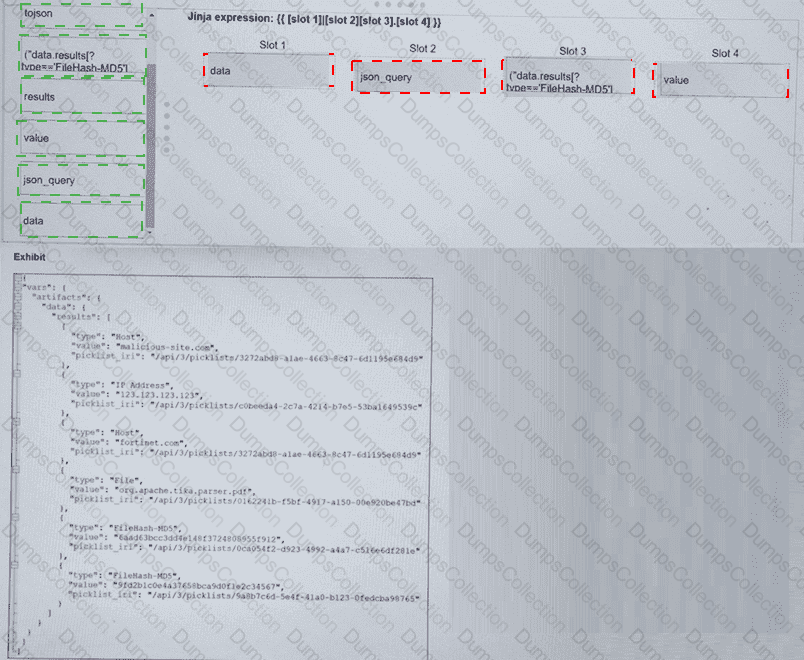
Refer to the exhibit. What is the correct Jinja expression to filter the results to show only the MD5 hash values?
{{ [slot 1] | [slot 2] [slot 3].[slot 4] }}
Select the Jinja expression in the left column, hold and drag it to a blank position on the right. Place the four correct steps in order, placing the first step in the first slot.