Huawei HCIE-WLAN (Written) V1.0 H12-351_V1.0 Exam Dumps: Updated Questions & Answers (March 2026)
To which of the following scenarios is radio calibration applicable?
Which of the following statements about the home agent are true? (Select All that Apply)
After multicast-to-unicast conversion is enabled on an AP's air interface, which of the followings is the destination MAC address of multicast packets sent over the air interface?
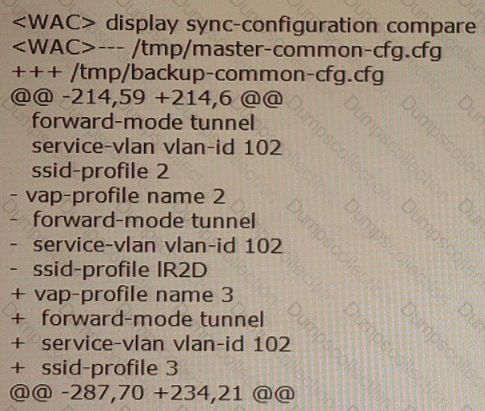
The display sync-configuration compare command is executed on the backup WAC in HSB to check wireless configuration synchronization. Based on the command output, which of the following statements are true? (Select All that apply)
Which of the following methods are used in IPsec to ensure secure transmission of service data on the network through encryption and authentication?
Which of the following are typical 802. IX authentication modes? (Select All that apply)
Which of the following statements about fingerprint-based positioning technology are true? (Select All that Apply)
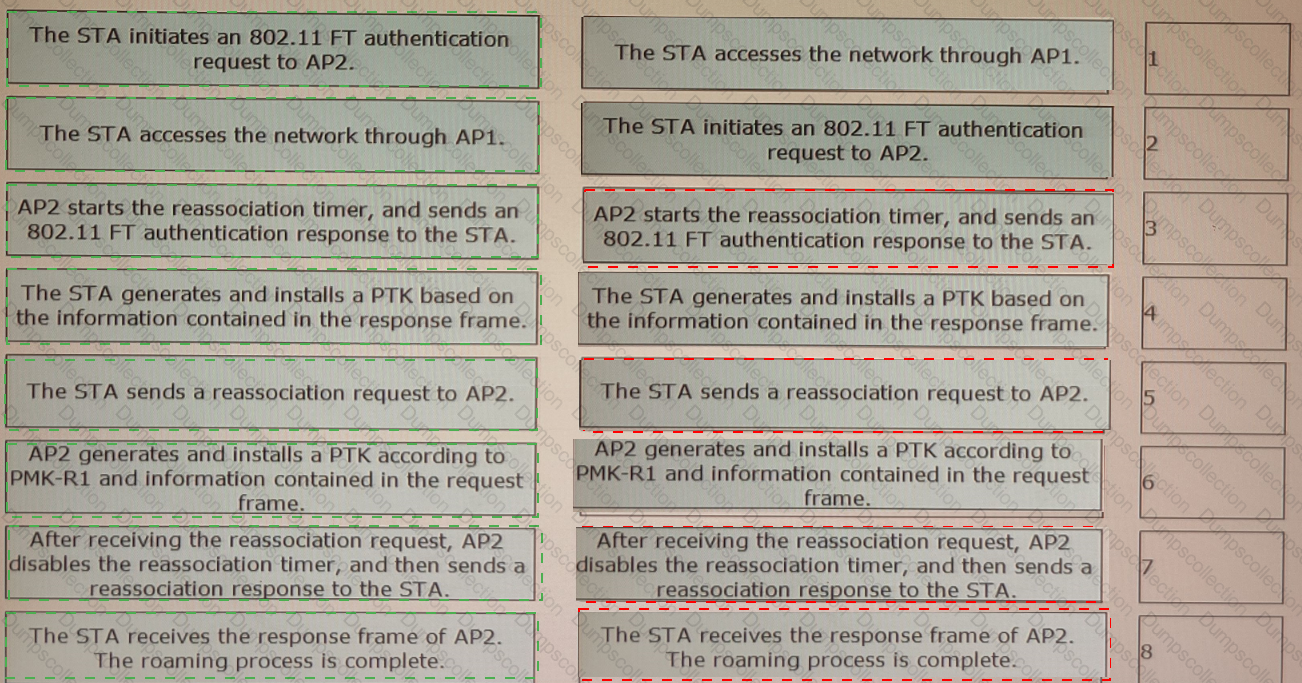
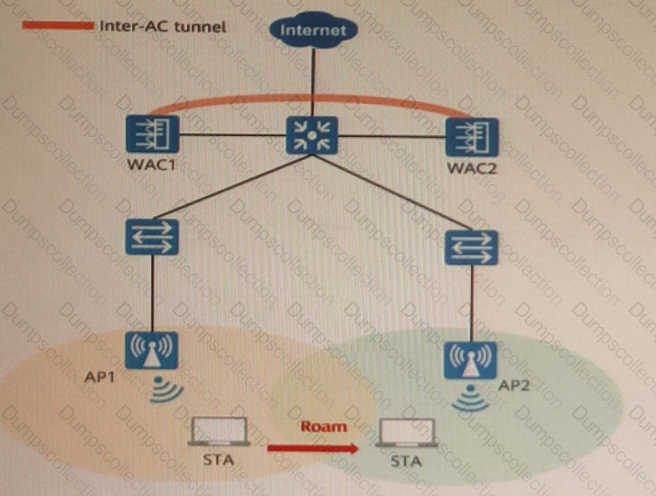
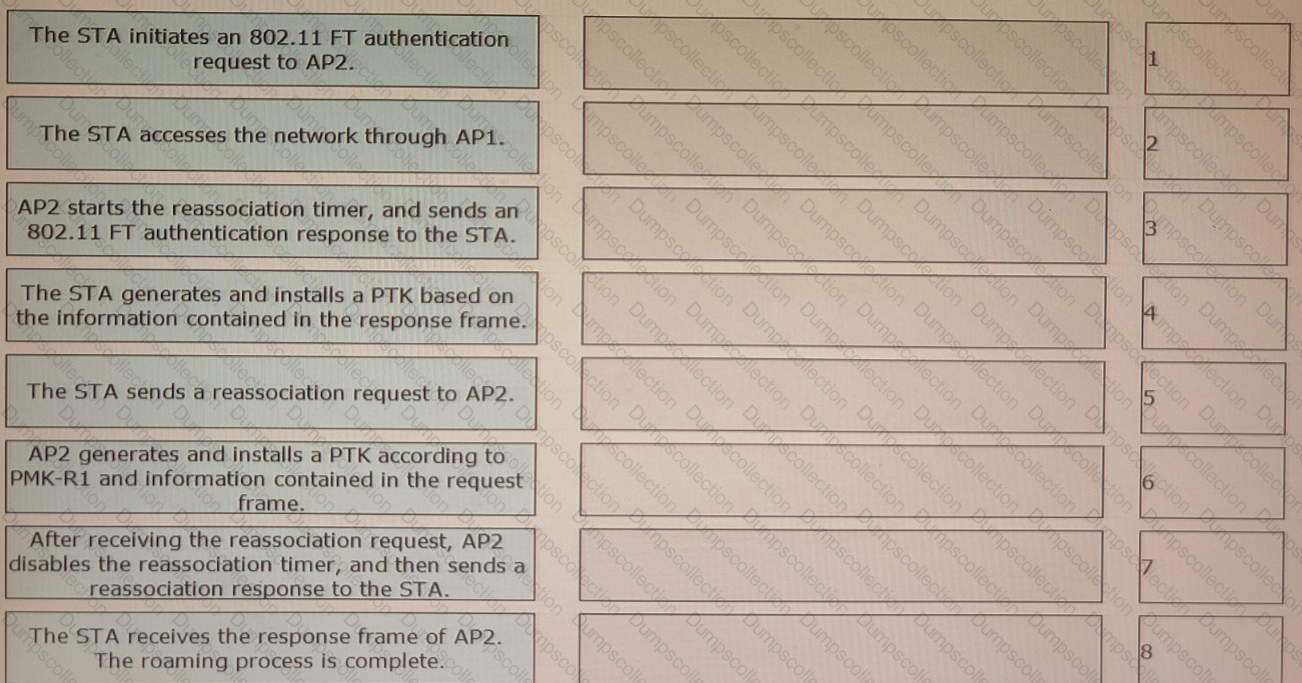
802. 11r fast roaming (over-the-air) is enabled on the WLAN shown in the figure. A STA roams from AP1 to AP2. Sort the steps in chronological order during the 802.11r fast roaming process between WACs.
Which of the following encapsulation formats are used for EAP termination in 802.1X authentication? (Select All that apply)
Which of the following statements about EAP relay and EAP termination are false? (Select All that apply)