Huawei HCIA-Security V4.0 Exam H12-711_V4.0 Exam Dumps: Updated Questions & Answers (March 2026)
ARP man-in-the-middle attacks are a type of spoofing attack technique.
What is correct about the following description of device management in the operating system?
Which of the following characteristics does a denial-of-service attack include?
Among the various aspects of the risk assessment of IS027001, which of the following does not belong to the system design and release process?
Which of the following descriptions about the main implementation of single sign-on is wrong? ( )[Multiple choice]*
An engineer needs to back up the firewall configuration. Now he wants to use a command to view all the current configurations of the firewall. May I ask the command he uses is ____[fill in the blank]*
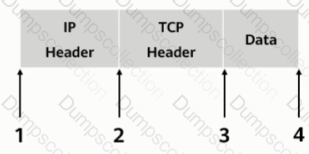
As shown, in transmission mode, which of the following locations should the AH header be inserted in?
In the TCP/P protocol core, which of the following protocols works at the application layer? ( )[Multiple choice]*
Which of the following descriptions of server authentication is correct?
When the Layer 2 switch receives a unicast frame and the MAC address table entry of the switch is empty, the switch discards the unicast frame.

