Huawei HCIP-Security V4.0 Exam H12-725_V4.0 Exam Dumps: Updated Questions & Answers (March 2026)
Multiple links can be deployed at the egress of an enterprise network to improve network reliability.
Which of the following is the function of Message 1 and Message 2 during IKEv1 phase-1 negotiation in main mode?
Before configuring DDoS attack defense, you must configure different thresholds for defense against different types of attacks. Each threshold can be considered an upper limit for normal network traffic. When the rate of traffic exceeds the pre-configured threshold, the firewall considers it to be attack traffic and takes a corresponding action to defend against it.
When an IPsec VPN is established in aggressive mode, AH+ESP can be used to encapsulate packets in NAT traversal scenarios.
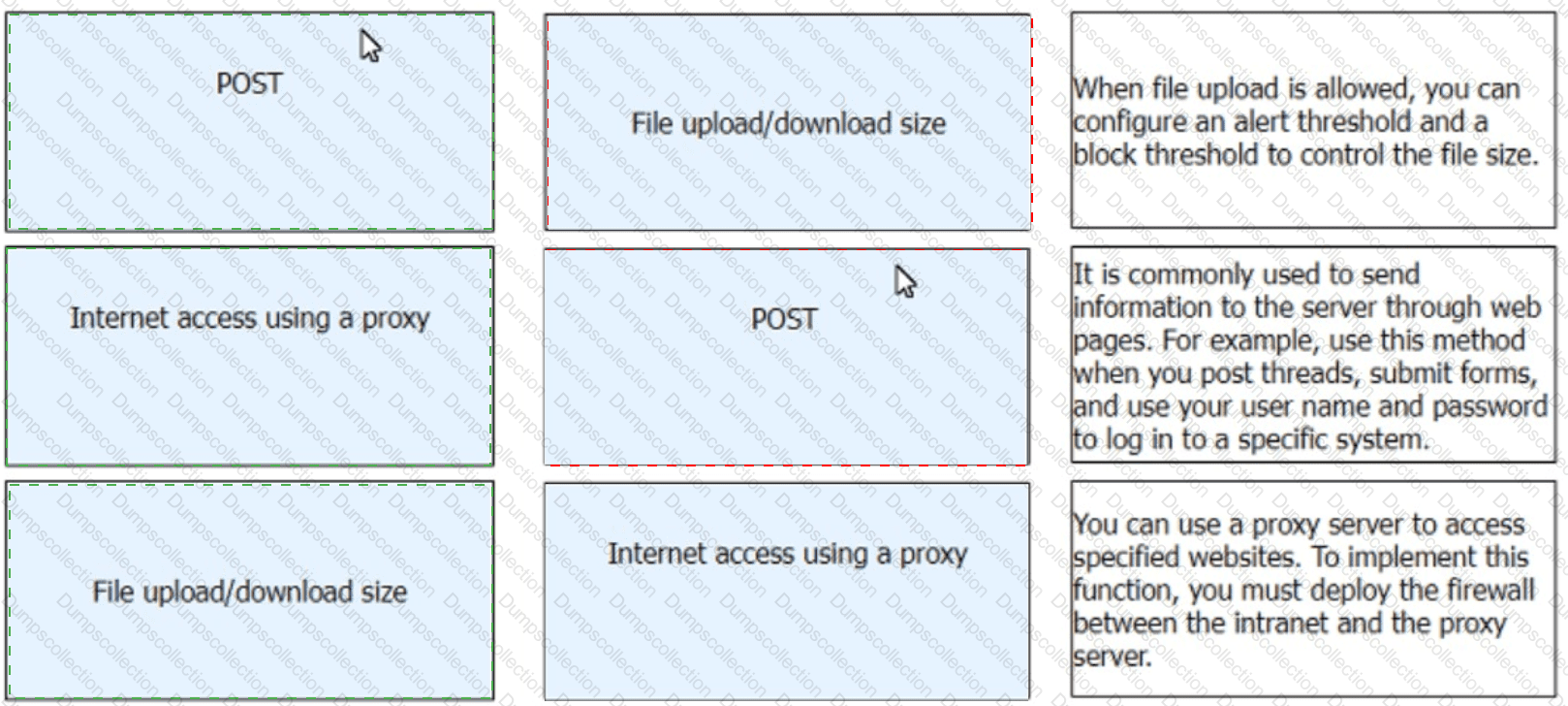
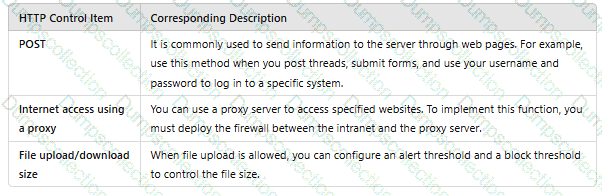
Match the HTTP control items with the corresponding descriptions.

Which of the following statements is false about HTTP behavior?
Which of the following statements is false about Eth-Trunk?(Select All that Apply)
When gateways are connected using GRE over IPsec, the IPsec encapsulation mode must be tunnel mode.
Predefined URL categories on Huawei firewalls reside in the URL category database delivered with the device and do not need to be manually loaded.
Which of the following protocols can be encapsulated through GRE over IPsec?(Select All that Apply)

 A screenshot of a computer error message
AI-generated content may be incorrect.
A screenshot of a computer error message
AI-generated content may be incorrect.