ISC CC - Certified in Cybersecurity CC Exam Dumps: Updated Questions & Answers (March 2026)
Representation of data at OSI Layer 3 is called a:
A transaction over $50,000 requires approval from both a manager and an accountant. Which concept applies?
What is the potential impact of an IPSec replay attack?
A standard that defines wired communication for network devices:
Exhibit.
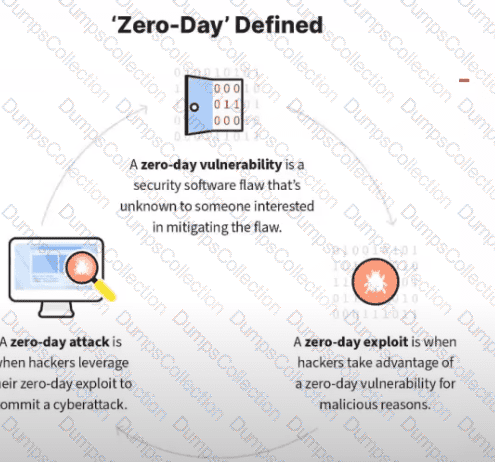
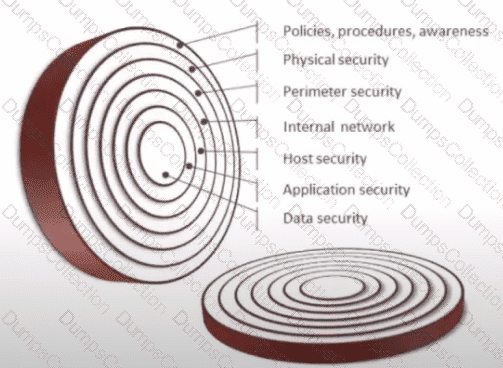
What kind of vulnerability is typically not identifiable through a standard vulnerability assessment?
In which phase of an incident response plan are incidents prioritized?
Why is the recovery of IT often crucial to the recovery and sustainment of business operations?
Which protocol would be most suitable to fulfill the secure communication requirements between clients and the server for a company deploying a new application?
What is the end goal of a Disaster Recovery Plan (DRP)?
An external entity attempts unauthorized access to your IT environment. This is a(n):

