Juniper Security, Professional (JNCIP-SEC) JN0-637 Exam Dumps: Updated Questions & Answers (March 2026)
Exhibit:
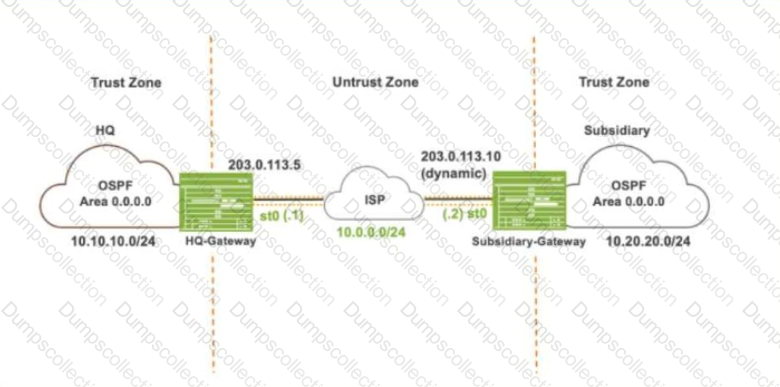
Referring to the exhibit, which IKE mode will be configured on the HQ-Gateway and Subsidiary-Gateway?
You are asked to create multiple virtual routers using a single SRX Series device. You must ensure that each virtual router maintains a unique copy of the routing protocol daemon (RPD) process.
Which solution will accomplish this task?
Which three statements about persistent NAT are correct? (Choose Three)
What are three configurable monitor components for a service redundancy group? (Choose two)
Referring to the exhibit,
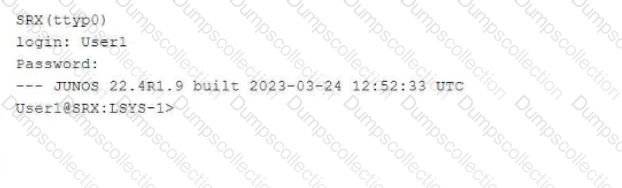
which two statements about User1 are true? (Choose two.)
Referring to the exhibit,
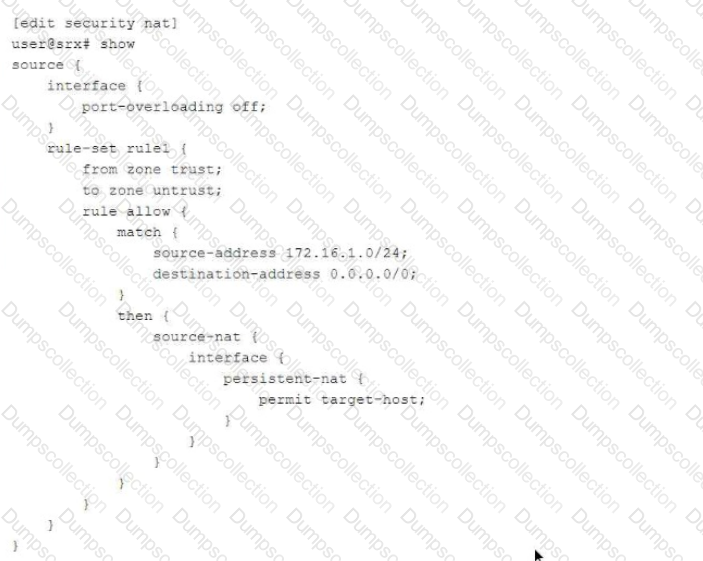
which two statements are correct about the NAT configuration? (Choose two.)
You have deployed an SRX Series device at your network edge to secure Internet-bound sessions for your local hosts using source NAT. You want to ensure that your users are able to interact with applications on the Internet that require more than one TCP session for the same application session.
Which two features would satisfy this requirement? (Choose two.)
You are asked to see if your persistent NAT binding table is exhausted.
Which show command would you use to accomplish this task?
Exhibit:
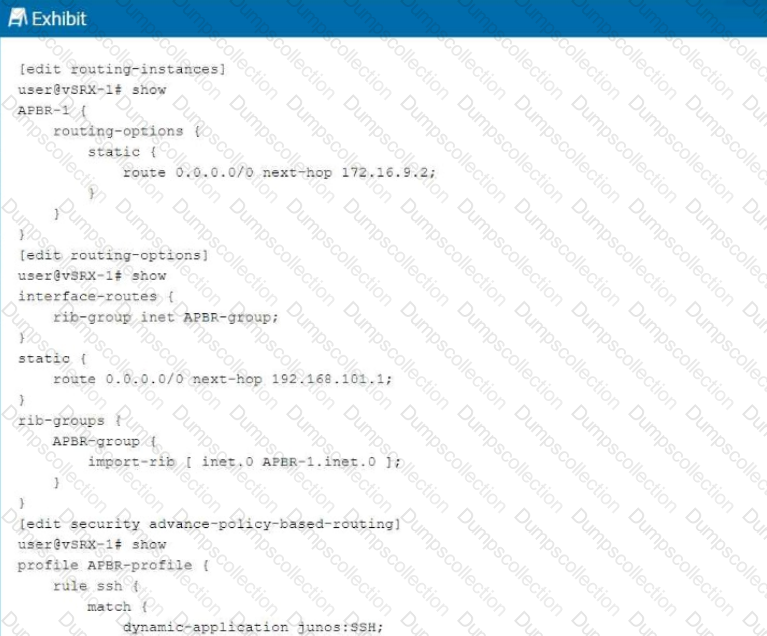
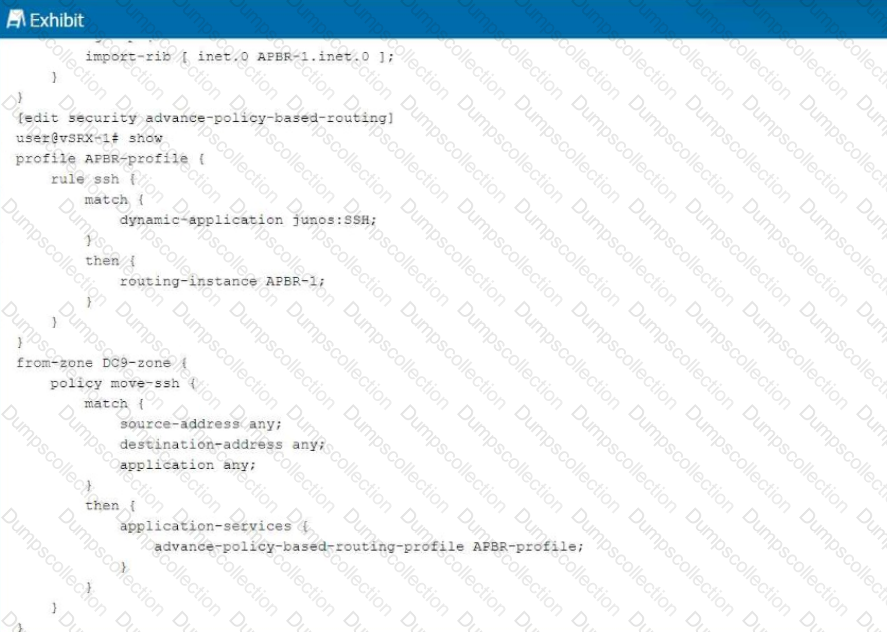
You are having problems configuring advanced policy-based routing.
What should you do to solve the problem?
You want to bypass IDP for traffic destined to social media sites using APBR, but it is not working and IDP is dropping the session.
What are two reasons for this problem? (Choose two.)

