Microsoft Administering Information Security in Microsoft 365 SC-401 Exam Dumps: Updated Questions & Answers (January 2026)
You have a Microsoft 365 subscription.
You have a user named User1 Several users have full access to the mailbox of User1.
Some email messages sent to User 1 appeal to have been read and deleted before the user viewed them
When you search the audit log in the Microsoft Purview portal to identify who signed in to the mailbox of User l. the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-AuditConfig -Workload Exchange command.
Does that meet the goal?
You have a Microsoft 365 E5 subscription that contains four users named User1. User2, User3, and User4 and a file named File1.docx. File1 has a sensitivity label applied. The label is configured as shown in the following table.
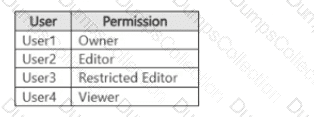
Which users can summarize File1 by using Microsoft 365 Copilot?
You have a Microsoft 565 E5 subscription.
You plan to use Microsoft Purview insider risk management.
You need to create an insider risk management policy that will detect data theft from Microsoft SharePoint Online by users that submitted their resignation or are near their employment termination date.
What should you do first?
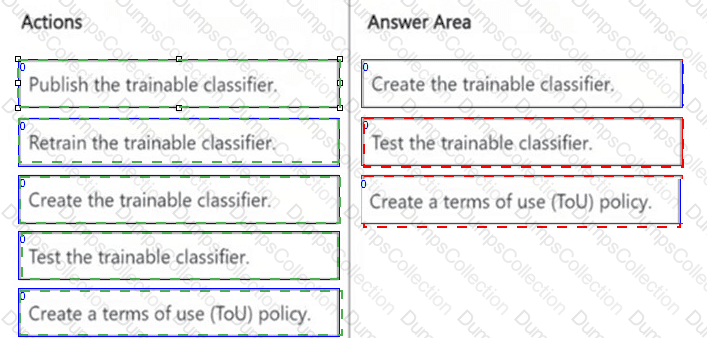
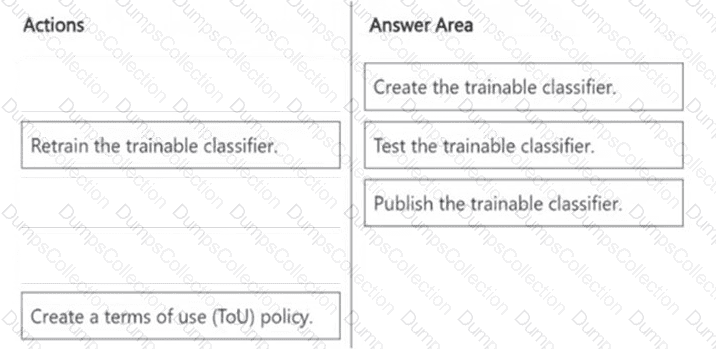
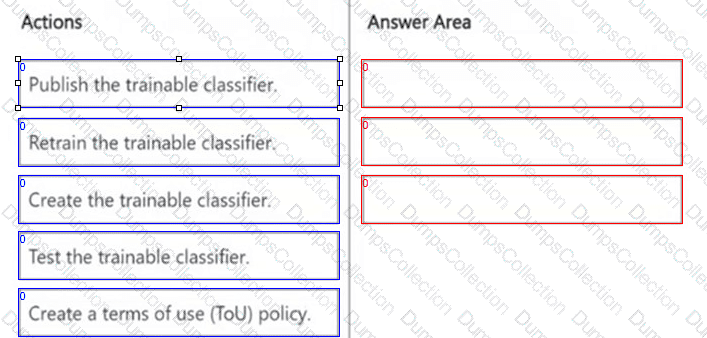
DRAG DROP
You need to create a trainable classifier that can be used as a condition in an auto-apply retention label policy.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
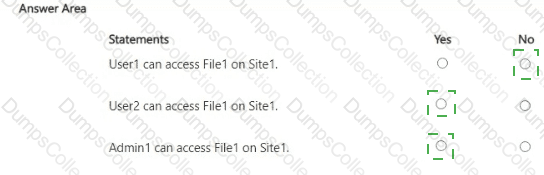
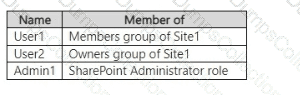
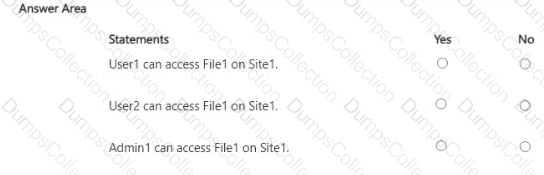
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1 and the users shown in the following table.
You have a data loss prevention (DLP) policy named DLP1 as shown in the following exhibit.
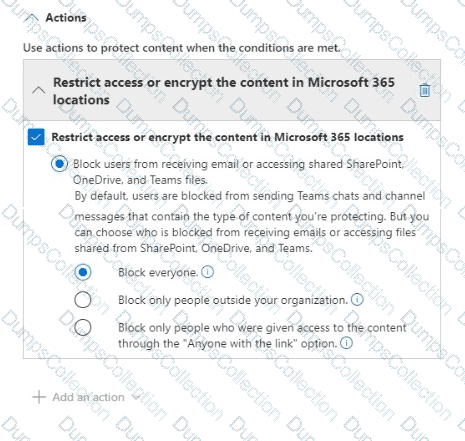
You apply DLP1 to Site1.
User1 uploads a file named File1 to Site1. File1 does NOT match any of the DLP1 rules. User2 updates File1 to contain data that matches the DLP1 rules.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
DRAG DROP
You have a Microsoft 365 E5 subscription that has data loss prevention (DLP) implemented.
You need to create a custom sensitive info type. The solution must meet the following requirements:
● Match product serial numbers that contain a 10-character alphanumeric string.
● Ensure that the abbreviation of SN appears within six characters of each product serial number.
● Exclude a test serial number of 1111111111 from a match.
Which pattern settings should you configure for each requirement? To answer, drag the appropriate settings to the correct requirements. Each setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 tenant that uses a domain named contoso.com.
A user named User 1 sends link based, branded emails that are encrypted by using Microsoft Purview Advanced Message Encryption to the recipients shown in the following table.
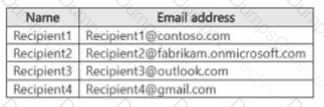
For which recipients Can User1 revoke the emails?
HOTSPOT
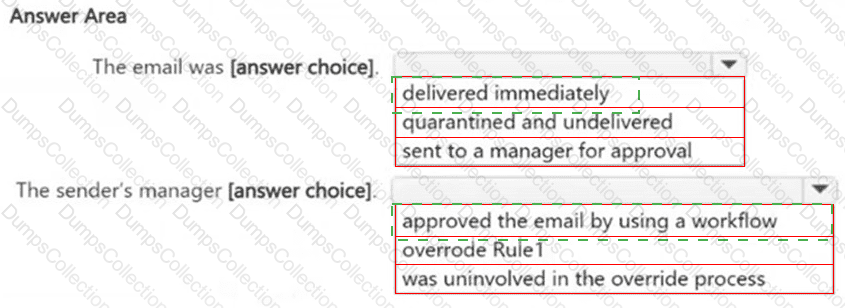
You have a Microsoft 365 E5 subscription.
You receive the data loss prevention (DLP) alert shown in the following exhibit.
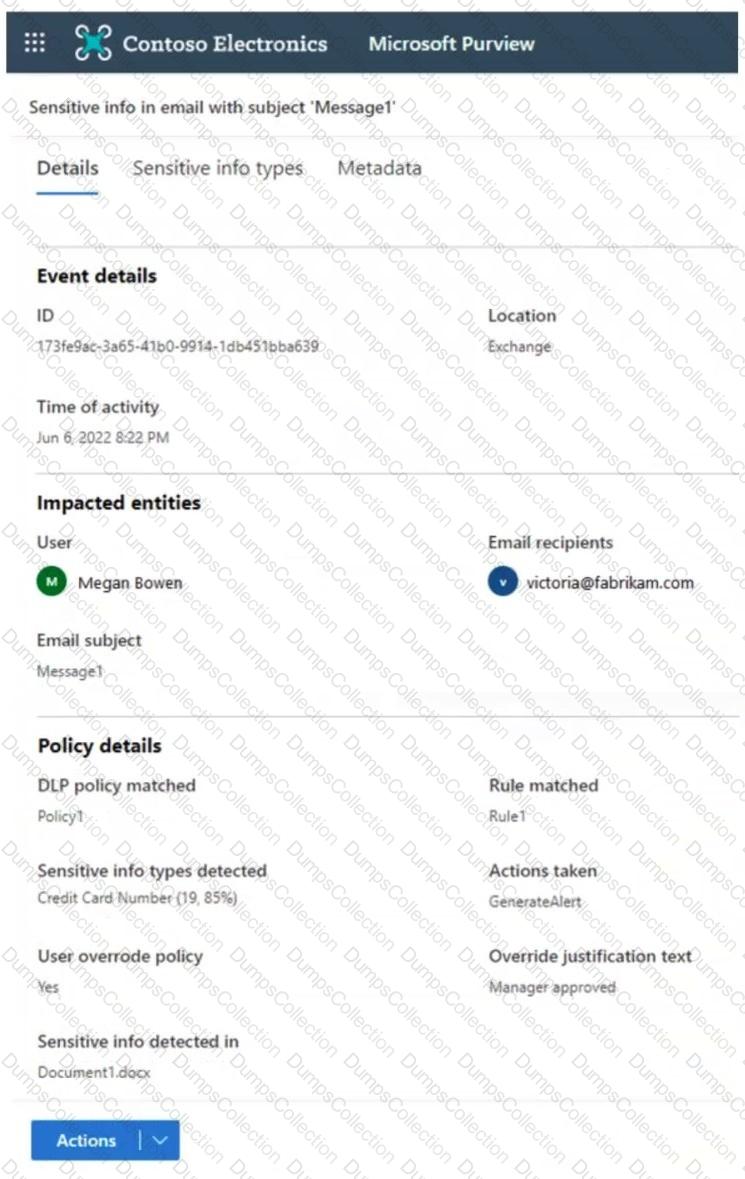
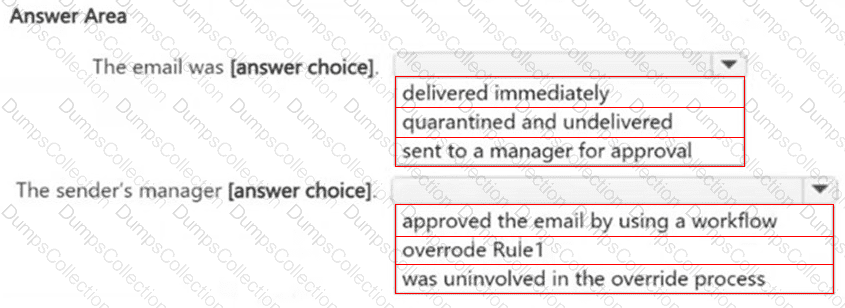
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
You have a Microsoft 565 subscription that contains 100 users and a Microsoft 365 group named Group1. All users have Windows 11 devices and use Microsoft SharePoint Online and Exchange Online. A sensitivity label named Label! is published as the default label for Group1. You add two sublabels named Sublabel1 and Sublabel2 lo Label1. You need to ensure that the settings in Sublabel 1 are applied by default to Group 1. What should you do?
At the end of a project, you upload project documents to a Microsoft SharePoint Online library that contains many files. The following is a sample of the project document file names:
• aei_AA989.docx
• bd_WS098.docx
• cei_DF112.docx
• ebc_QQ454.docx
• ecc_BB565.docx
All documents that use this naming format must be labeled as Project Documents:
You need to create an auto-apply retention label policy.
What should you use to identify the files?