Oracle Oracle Database Security Administration 1z0-116 Exam Dumps: Updated Questions & Answers (March 2026)
Which two are true about Database Privilege Analysis?
What Is the first step when analyzing security within a database?
Examine these commands and the output used to configure Real Application Security:
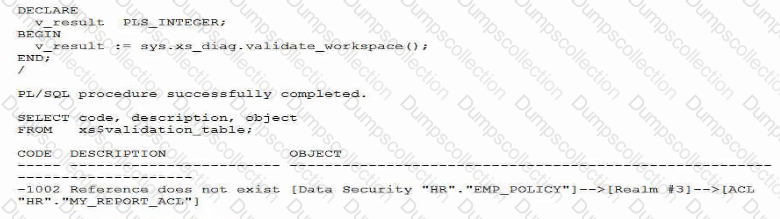
What does this output mean?
Examine this query:
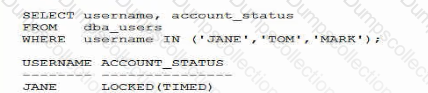
Why is this account in this status?
The listener configuration contains these lines related to Valid Node Checking for Registration (VNCR);
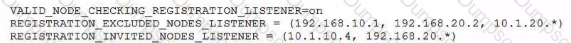
Which two statements are true?
Which two represent the set of users that are never affected by connect command rules?
For which two are Oracle Label Security policies not applied?
Examine these steps:
1. Run the DBSAT Collector
2. Run the DBSAT Discoverer
3. Run the DBSAT Reporter
Identify the minimum required steps for producing a report of schemas with sensitive data.
Database Vault is not used in your installation.
Why is a conventional secure application role more secure than a normal role?
Examine the statement:
CREATE BOLE hr_admin IDENTIFIED USING pac_mgr.hr_admin_rola_ch9ck;
Which three are true about the sec_mgr. hr_admin_role_check procedure?

