Oracle Oracle Hyperion Data Relationship Management Essentials 1z0-588 Exam Dumps: Updated Questions & Answers (March 2026)
Per the following example:
All Products

A user is assigned to two node access group, G_Colas and G_Diet Cola. G_Colas is assigned Add permission for the Colas node in the product hierarchy and the G_Diet Cola group is assigned I dit permission for the Diet Cola node.
He is assigned the Interactive User role. Identify the three true statements.
Identify the two true statement about Action Scripts.
Review the example below:
Product
All Products
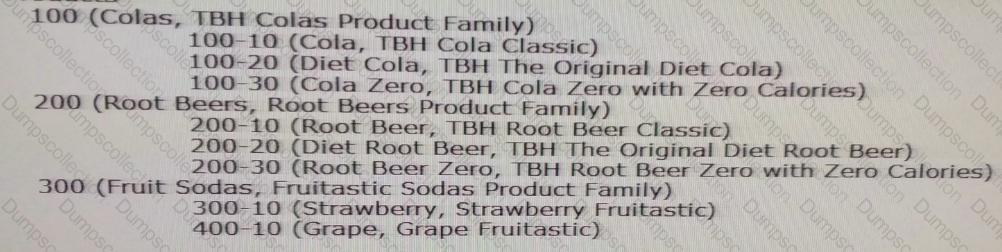
Alternate Product Hierarchy
All Products
High Calorie, Sugar Filled Products
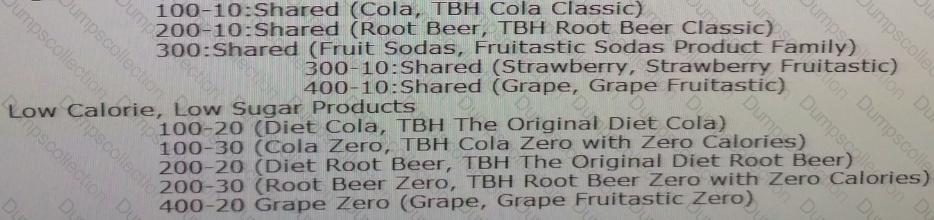
Your target Essbase database requires an alternate of the Product, rolling up product SKUs by Caffeinated and NonCaffeinated. You currently maintain this value as a property. Once a valid export is built, what are the two ways you can create the new hierarchy in an existing version?
Identify the four true statements about designing property categories, property definitions, and validations for target and source systems.
Identify three ways to narrow the scope of the first phase of the DRM implementation.
Identify the two true statements about user permissions.
Identify the three true statements about using the "Asc" property types.
"Primary" and "LE_Restructure" are both versions in your DRM application and both have a hierarchy named "Legal Entity".
The nodes and structure of each hierarchy are as follows:
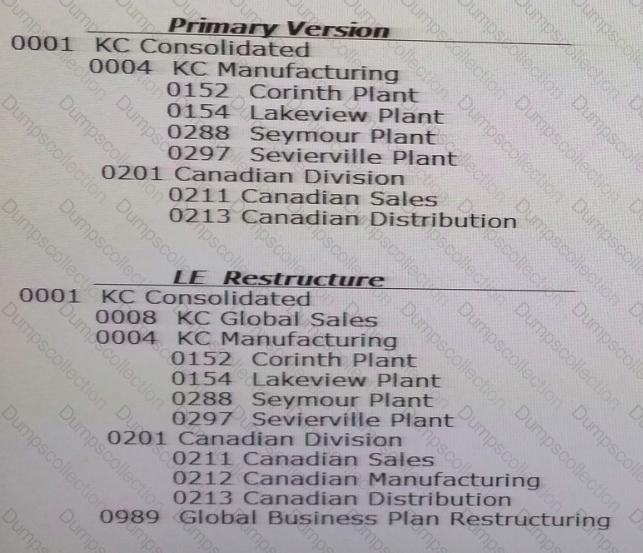
Select the nodes that would be included in a Structure Compare for Differences.
Per the example:
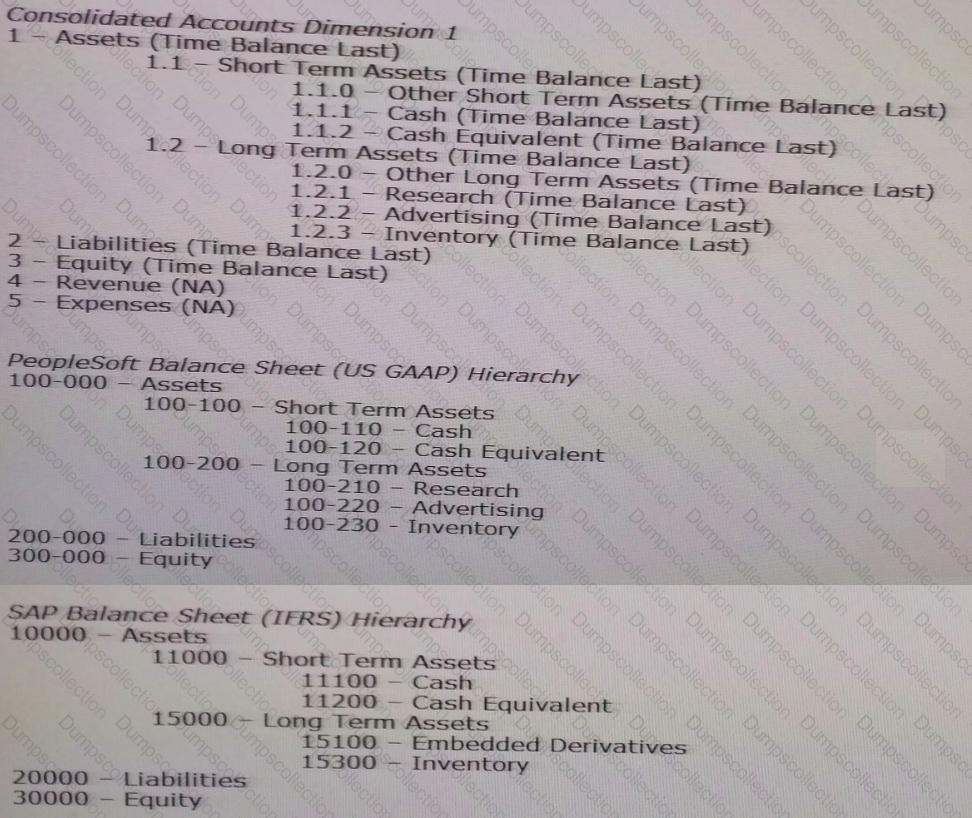
Your organization has two ERPs: PeopleSoft (PS) and SAP. Each ERP has its own chart of accounts. Each chart of accounts is mapped to a consolidated chart of accounts. The Finance department maintains the consolidated account hierarchy.
Identify the steps in the correct order to manage the mapping of the local chart of accounts in the consolidated chart of accounts structure using DRM hierarchies.
1. Build the consolidated chart of accounts hierarchy.
2. Build the PeopleSoft and SAP chart of accounts hierarchies.
3. Create a property category called CoA Map with two property definitions: PS CoA Mapping and SAP CoA Mapping.
4. Create an alternate Market hierarchy with limb nodes "large", "Medium", and "Small". Insert cities as leaf nodes under the appropriate Market Size nodes.
5. Use the Blend function to merge the PeopleSoft and sap chart of accounts to the correct consolidated account node In the consolidated hierarchy.
6. Drag and drop the PeopleSoft and SAP chart of accounts to the correct consolidated account in the consolidated hierarchy.
Identify the three true statements about External Connections.

