Paloalto Networks Palo Alto Networks XSIAM Engineer XSIAM-Engineer Exam Dumps: Updated Questions & Answers (February 2026)
A vulnerability analyst asks a Cortex XSIAM engineer to identify assets vulnerable to newly reported zero-day CVE affecting the "ai_app" application and versions 12.1, 12.2, 12.4, and 12.5.
Which XQL query will provide the required result?
A)

B)

C)

D)

What is the primary function of the URL "https://
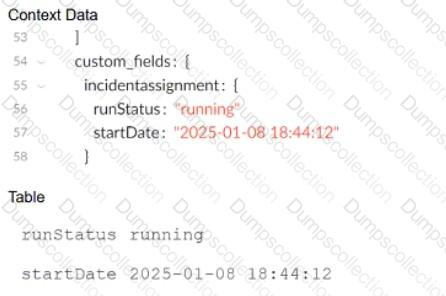
Based on the images below, which command will allow the context data to be displayed as a table when troubleshooting a playbook task?
A Cortex XSIAM engineer plans to add Kafka and Syslog Collectors to a Broker VM cluster.
What are two expected behaviors of the applets when they are added to the cluster? (Choose two.)
What is a key characteristic of a parsing rule in Cortex XSIAM?
Which types of content may be included in a Marketplace content pack?
Which section of a parsing rule defines the newly created dataset?
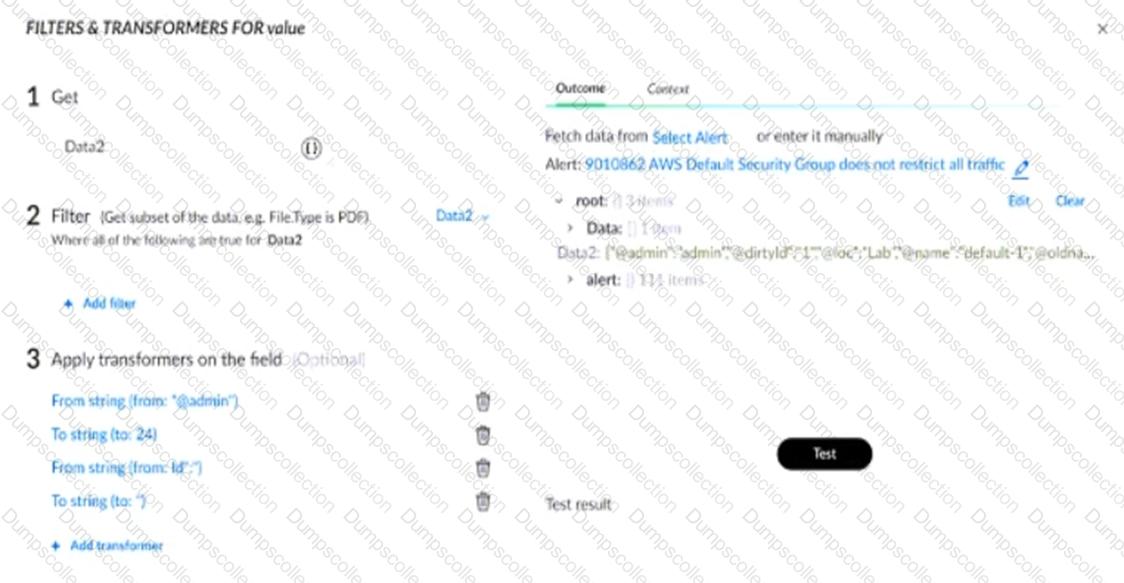
The following string is a value of a key named "Data2" in the context:
{"@admin":"admin","@dirtyld":"1","@loc":"Lab","@name":"default‑1","@oldname":"Test","@time":"2024/08/28 07:45:15","alert":{"@admin":"admin","@dirtyld":"2","@time":"2024/08/28 07:45:15","member":{"#text":"
Based on the image below, what will be displayed in the "Test result" field when the "Test" button is pressed?
In which two locations can correlation rules be monitored for errors? (Choose two.)
A systems engineer overseeing the integration of data from various sources through data pipelines into Cortex XSIAM notices modifications occurring during the ingestion process, and these modifications reduce the accuracy of threat detection and response. The engineer needs to assess the risks associated with the pre-ingestion data modifications and develop effective solutions for data integrity and system efficacy.
Which set of steps must be followed to meet these goals?

