RedHat Red Hat Certified Specialist in Ansible Automation exam EX407 Exam Dumps: Updated Questions & Answers (March 2026)
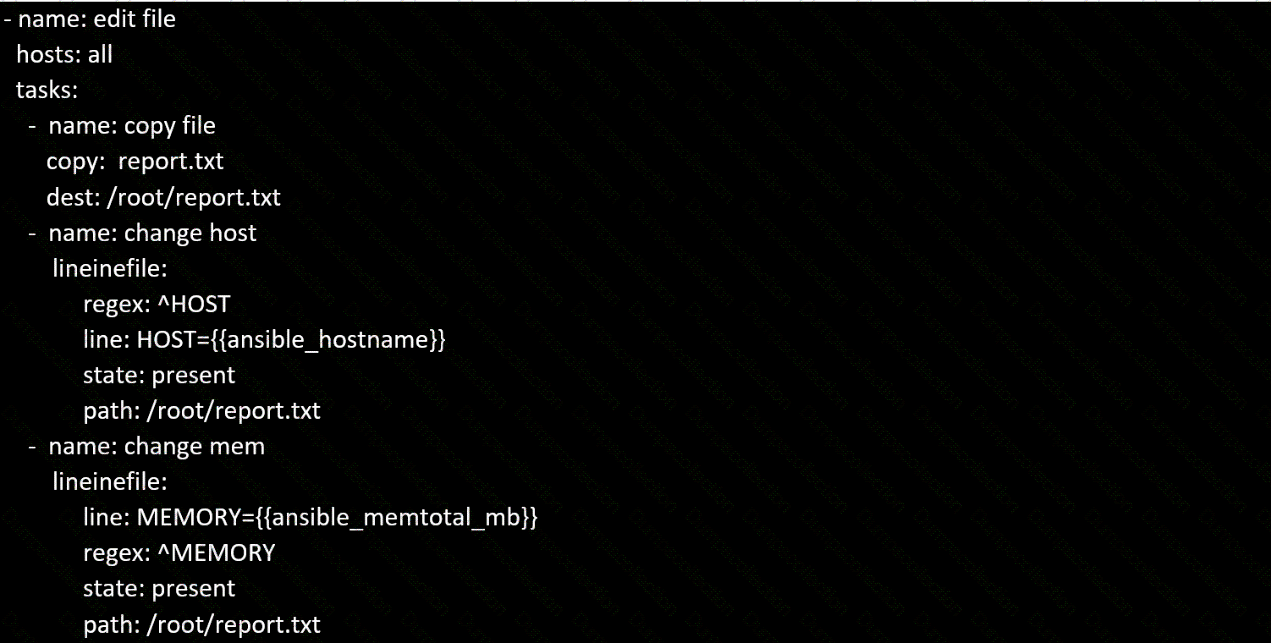
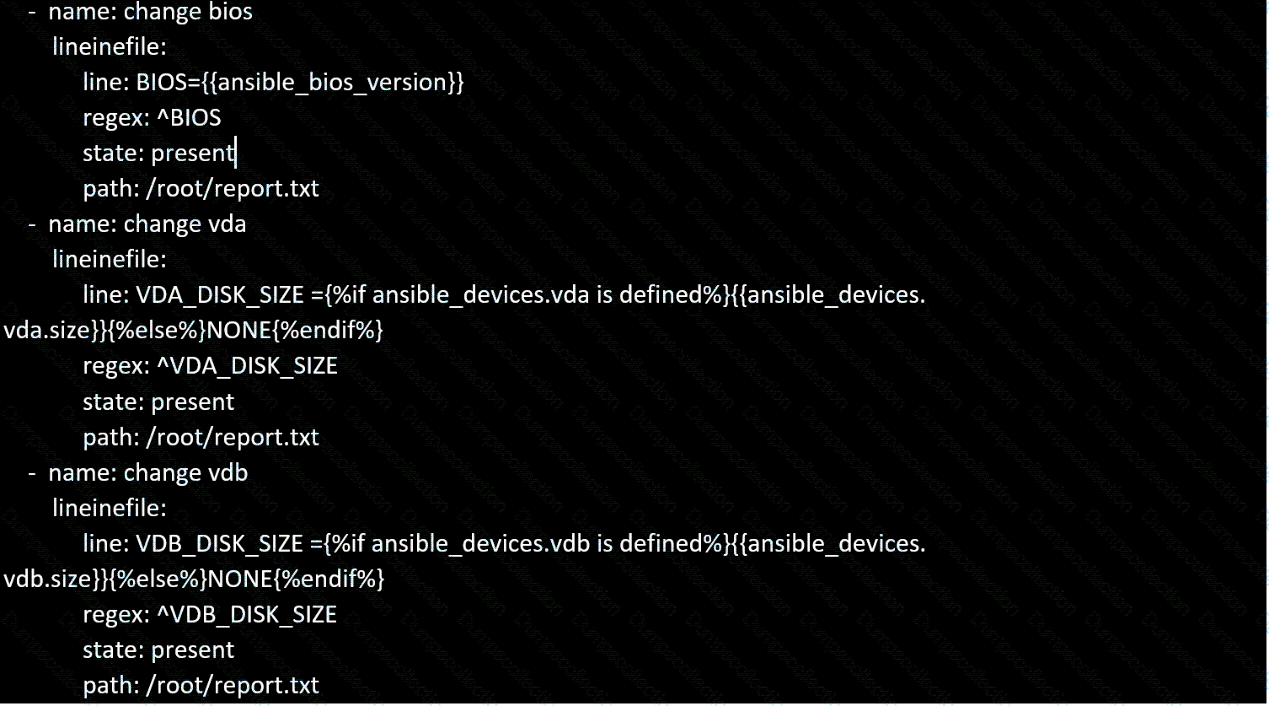
Create a file called specs.empty in home/bob/ansible on the local machine as follows:
HOST=
MEMORY=
BIOS=
VDA_DISK_SIZE=
VDB_DISK_SIZE=
Create the playbook /home/bob/ansible/specs.yml which copies specs.empty to all remote nodes' path /root/specs.txt. Using the specs.yml playbook then edit specs.txt on the remote machines to reflect the appropriate ansible facts.
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Create a role called apache in "/home/admin/ansible/roles" with the following
requirements:
--> The httpd package is installed, enabled on boot, and started.
--> The firewall is enabled and running with a rule to allow access to the web server.
--> template file index.html.j2 is used to create the file /var/www/html/index.html
with the output:
Welcome to HOSTNAME on IPADDRESS
--> Where HOSTNAME is the fqdn of the managed node and IPADDRESS is the IP-Address of
the managed node.
note: you have to create index.html.j2 file.
--> Create a playbook called httpd.yml that uses this role and the playbook runs on
hosts in the webservers host group.
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Install and configure Ansible on the control-node control.realmX.example.com as
follows:
-------------------------------------------------------------------------------------------
--> Install the required packages
--> Create a static inventory file called /home/admin/ansible/inventory as follows:
node1.realmX.example.com is a member of the dev host group
node2.realmX.example.com is a member of the test host group
node3.realmX.example.com & node4.realmX.example.com are members of the prod
host group
node5.realmX.example.com is a member of the balancers host group.
prod group is a member of the webservers host group
--> Create a configuration file called ansible.cfg as follows:
--> The host inventory file /home/admin/ansible/inventory is defined
--> The location of roles used in playbooks is defined as /home/admin/ansible/ roles
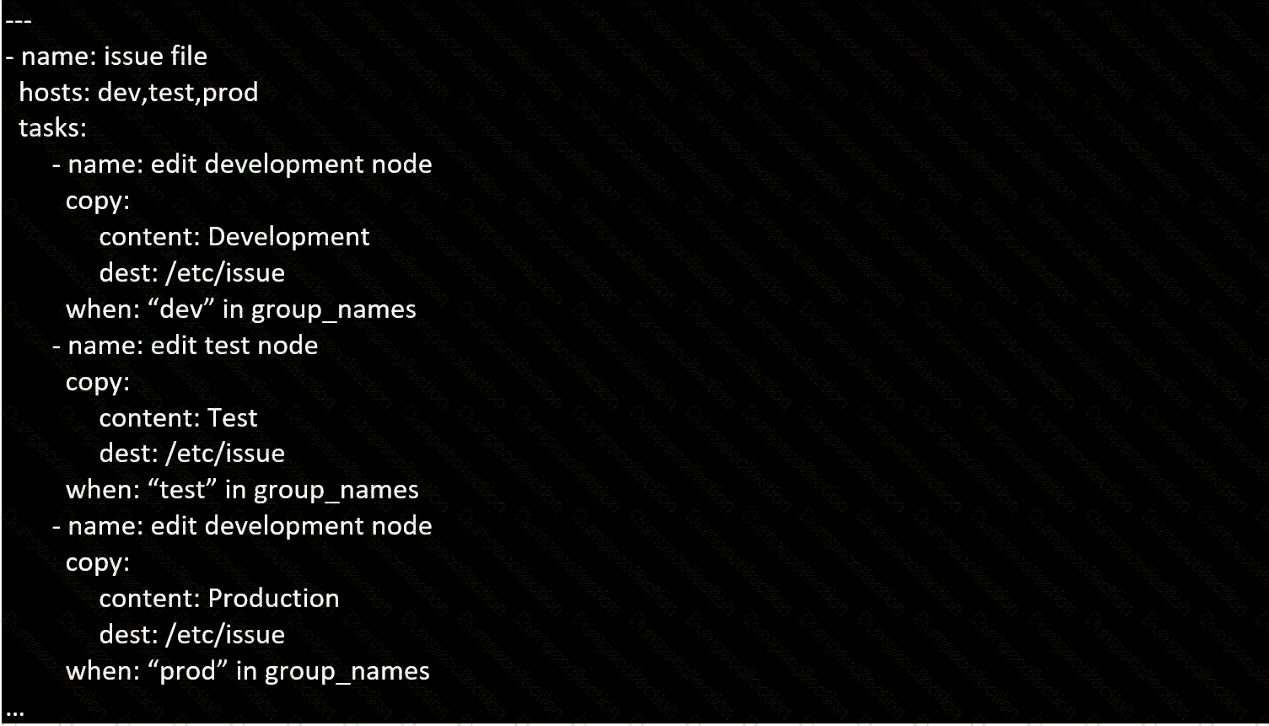
Create a playbook called issue.yml in /home/sandy/ansible which changes the file /etc/issue on all managed nodes: If host is a member of (lev then write "Development" If host is a member of test then write "Test" If host is a member of prod then write "Production"
Create a file called requirements.yml in /home/sandy/ansible/roles to install two roles. The source for the first role is geerlingguy.haproxy and geerlingguy.php. Name the first haproxy-role and the second php-role. The roles should be installed in /home/sandy/ansible/roles.
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Create Logical volumes with lvm.yml in all nodes according to following
requirements.
----------------------------------------------------------------------------------------
* Create a new Logical volume named as 'data'
* LV should be the member of 'research' Volume Group
* LV size should be 1500M
* It should be formatted with ext4 file-system.
--> If Volume Group does not exist then it should print the message "VG Not found"
--> If the VG can not accommodate 1500M size then it should print "LV Can not be
created with
following size", then the LV should be created with 800M of size.
--> Do not perform any mounting for this LV.
Create a file called adhoc.sh in /home/sandy/ansible which will use adhoc commands to set up a new repository. The name of the repo will be 'EPEL' the description 'RHEL8' the baseurl is 'https://dl.fedoraproject.org/pub/epel/epel -release-latest-8.noarch.rmp' there is no gpgcheck, but you should enable the repo.
* You should be able to use an bash script using adhoc commands to enable repos. Depending on your lab setup, you may need to make this repo "state=absent" after you pass this task.
Create a file called mysecret.yml on the control host using ansible vault in home/bob/ansible. Set the password to 'notasafepass' and inside the file create a variable called dev_pass with the value of devops. Save the file. Then go back in the file and change dev_pass value to devops123. Then change the vault password of mysecret.yml to verysafepass
===================================================================================
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don’t change ‘root’ or ‘admin’ password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
===================================================================================
Create user accounts
------------------------
--> A list of users to be created can be found in the file called user_list.yml
which you should download from http://classroom.example.com/user_list.yml and
save to /home/admin/ansible/
--> Using the password vault created elsewhere in this exam, create a playbook called
create_user.yml
that creates user accounts as follows:
--> Users with a job description of developer should be:
--> created on managed nodes in the "dev" and "test" host groups assigned the
password from the "dev_pass"
variable and these user should be member of supplementary group "devops".
--> Users with a job description of manager should be:
--> created on managed nodes in the "prod" host group assigned the password from
the "mgr_pass" variable
and these user should be member of supplementary group "opsmgr"
--> Passwords should use the "SHA512" hash format. Your playbook should work using
the vault password file
created elsewhere in this exam.
while practising you to create these file hear. But in exam have to download as per
questation.
user_list.yml file consist:
---
user:
- name: user1
job: developer
- name: user2
job: manager
Create a playbook called timesvnc.yml in /home/sandy/ansible using rhel system role timesync. Set the time to use currently configured nip with the server 0.uk.pool.ntp.org. Enable burst. Do this on all hosts.