Splunk Splunk Cloud Certified Admin SPLK-1005 Exam Dumps: Updated Questions & Answers (February 2026)
The following sample log event shows evidence of credit card numbers being present in the transactions. loc file.
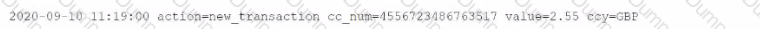
Which of these SEDCM3 settings will mask this and other suspected credit card numbers with an Y character for each character being masked? The indexed event should be formatted as follows:

A)
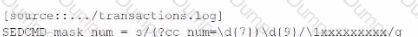
B)

C)

D)
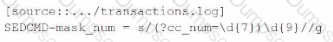
When is data deleted from a Splunk Cloud index?
Which of the following are valid settings for file and directory monitor inputs?
A)
B)

C)

D)

Given the following set of files, which of the monitor stanzas below will result in Splunk monitoring all of the files ending with .log?
Files:
/var/log/www1/secure.log
/var/log/www1/access.log
/var/log/www2/logs/secure.log
/var/log/www2/access.log
/var/log/www2/access.log.1
When should Splunk Cloud Support be contacted?
Consider the following configurations:
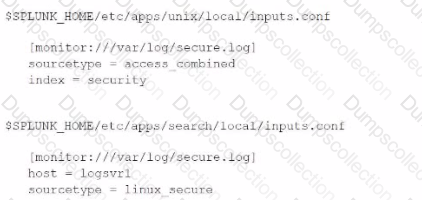
What is the value of the sourcetype property for this stanza based on Splunk's configuration file precedence?
Which of the following is not a path used by Splunk to execute scripts?
For the following data, what would be the correct attribute/value oair to use to successfully extract the correct timestamp from all the events?
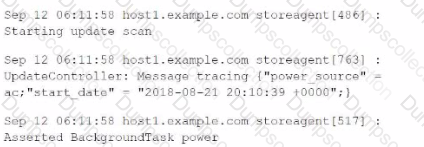
At what point in the indexing pipeline set is SEDCMD applied to data?
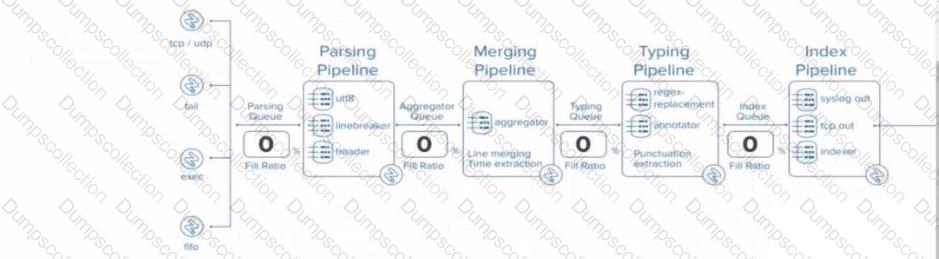
In what scenarios would transforms.conf be used?

