Symantec Administration of Symantec Data Loss Prevention 15 250-438 Exam Dumps: Updated Questions & Answers (March 2026)
What is the correct configuration for “BoxMonitor.Channels” that will allow the server to start as a Network Monitor server?
A company needs to implement Data Owner Exception so that incidents when employees send or receive their own personal information.
What detection method should the company use?
Refer to the exhibit.
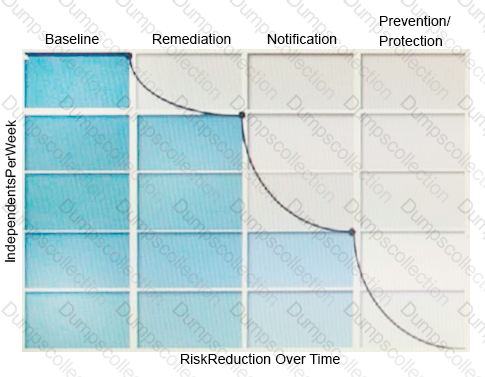
What activity should occur during the baseline phase, according to the risk reduction model?
Refer to the exhibit. Which type of Endpoint response rule is shown?
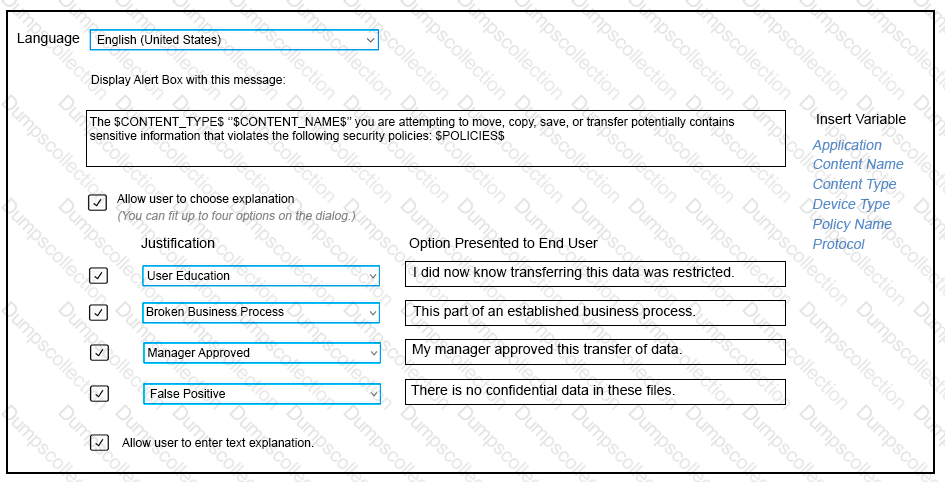
How should a DLP administrator change a policy so that it retains the original file when an endpoint incident has detected a “cope to USB device” operation?
A DLP administrator is preparing to install Symantec DLP and has been asked to use an Oracle database provided by the Database Administration team.
Which SQL *Plus command should the administrator utilize to determine if the database is using a supported version of Oracle?
Which two technologies should an organization utilize for integration with the Network Prevent products? (choose two.)
Why is it important for an administrator to utilize the grid scan feature?
A DLP administrator determines that the \SymantecDLP\Protect\Incidents folder on the Enforce server contains. BAD files dated today, while other. IDC files are flowing in and out of the \Incidents directory. Only .IDC files larger than 1MB are turning to .BAD files.
What could be causing only incident data smaller than 1MB to persist while incidents larger than 1MB change to .BAD files?
Which network Prevent action takes place when the network Incident list shows the message is “Modified”?

