Trend Micro Trend Micro Certified Professional for Deep Security Exam Deep-Security-Professional Exam Dumps: Updated Questions & Answers (March 2026)
Which of the following correctly describes the Firewall rule Action of Force Allow?
Which of following statements best describes Machine Learning in Deep Security?
An administrator attempts to activate the Deep Security Agent installed on a server by typing the following command in the Command Prompt on the Deep Security Agent computer:
dsa_control -a dsm://server1.acme.com:4120
The Agent does not activate as expected. What is a valid reason for this issue?
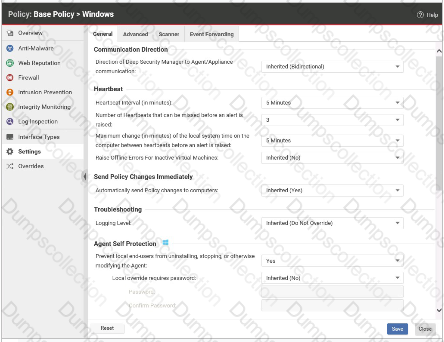
Which of the following statements is correct regarding the policy settings displayed in the exihibit?
Which of the following statements is FALSE regarding Firewall rules using the Bypass action?
Which of the following statements correctly identifies the purpose of the Integrity Monitoring Protection Module?
Which of the following statements correctly describes Smart Folders?
Which of the following VMware components is not required to enable agentless protection using Deep Security.
Which Deep Security Protection Modules can be used to provide runtime protection for the Kubernetes and Docker platforms? Select all that apply.
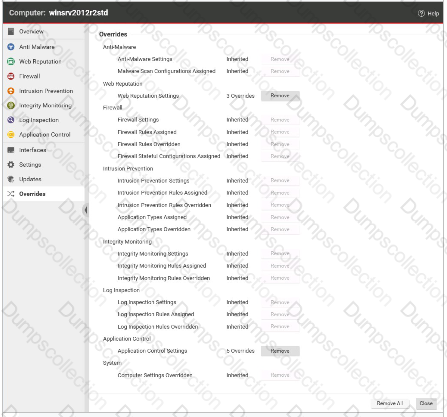
The Overrides settings for a computer are displayed in the exhibit. Which of the following statements is true regarding the displayed configuration?