Cisco Conducting Forensic Analysis and Incident Response Using Cisco CyberOps Technologies (CBRFIR) 300-215 Exam Dumps: Updated Questions & Answers (March 2026)

A website administrator has an output of an FTP session that runs nightly to download and unzip files to a local staging server. The download includes thousands of files, and the manual process used to find how many files failed to download is time-consuming. The administrator is working on a PowerShell script that will parse a log file and summarize how many files were successfully downloaded versus ones that failed. Which script will read the contents of the file one line at a time and return a collection of objects?
Which tool should be used for dynamic malware analysis?
Which issue is associated with gathering evidence from virtualized environments provided by major cloud vendors?
An incident response team is recommending changes after analyzing a recent compromise in which:
a large number of events and logs were involved;
team members were not able to identify the anomalous behavior and escalate it in a timely manner;
several network systems were affected as a result of the latency in detection;
security engineers were able to mitigate the threat and bring systems back to a stable state; and
the issue reoccurred shortly after and systems became unstable again because the correct information was not gathered during the initial identification phase.
Which two recommendations should be made for improving the incident response process? (Choose two.)
A financial company handling international transactions recently experienced a complex security incident The incident involves simultaneous DDoS attacks, suspected internal data leakage and the discovery of sophisticated malware implants that have remained dormant until triggered remotely During the incident it became clear that the current procedures are inadequate and plans to tackle issues were created on the go To counter this problem going forward, the IR team is developing an incident playbook to be used if a similar incident reoccurs Which set of elements of the playbook must be introduced?
A company had a recent data leak incident. A security engineer investigating the incident discovered that a malicious link was accessed by multiple employees. Further investigation revealed targeted phishing attack attempts on macOS systems, which led to backdoor installations and data compromise. Which two security solutions should a security engineer recommend to mitigate similar attacks in the future? (Choose two.)
An incident response analyst is preparing to scan memory using a YARA rule. How is this task completed?
Refer to the exhibit.
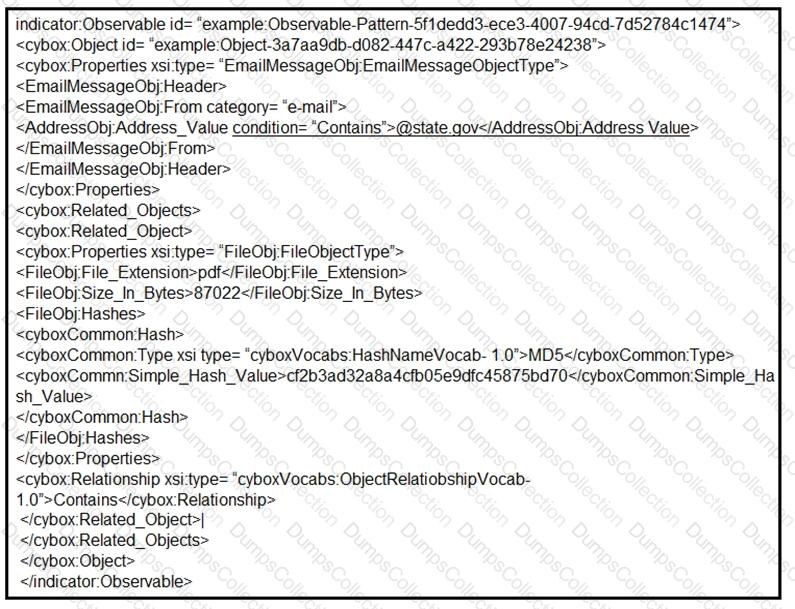
Which two actions should be taken as a result of this information? (Choose two.)
An organization experienced a sophisticated phishing attack that resulted in the compromise of confidential information from thousands of user accounts. The threat actor used a land and expand approach, where initially accessed account was used to spread emails further. The organization's cybersecurity team must conduct an in-depth root cause analysis to uncover the central factor or factors responsible for the success of the phishing attack. The very first victim of the attack was user with email 500236186@test.com. The primary objective is to formulate effective strategies for preventing similar incidents in the future. What should the cybersecurity engineer prioritize in the root cause analysis report to demonstrate the underlying cause of the incident?

