Fortinet Fortinet NSE 7 - OT Security 7.2 NSE7_OTS-7.2 Exam Dumps: Updated Questions & Answers (March 2026)
Which two statements are true when you deploy FortiGate as an offline IDS? (Choose two.)
The OT network analyst runs different level of reports to quickly explore threats that exploit the network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting method helps to identify these type of exploits of image firmware files?
An OT administrator has configured FSSO and local firewall authentication. A user who is part of a user group is not prompted from credentials during authentication.
What is a possible reason?
Refer to the exhibit.
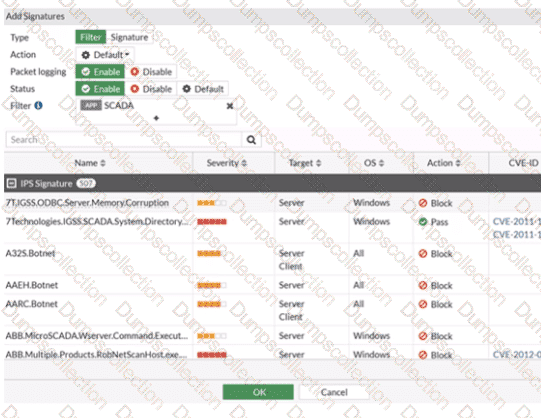
The IPS profile is added on all of the security policies on FortiGate.
For an OT network, which statement of the IPS profile is true?
To increase security protection in an OT network, how does application control on ForliGate detect industrial traffic?
What can be assigned using network access control policies?
What are two critical tasks the OT network auditors must perform during OT network risk assessment and management? (Choose two.)
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
Refer to the exhibit.
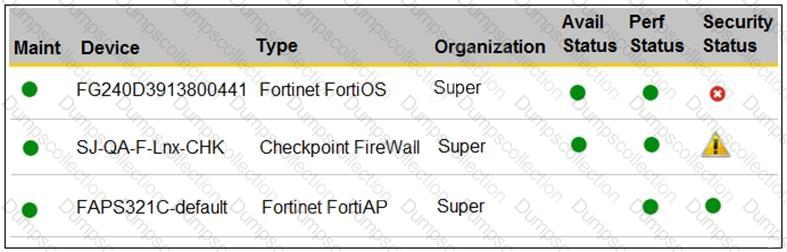
You are navigating through FortiSIEM in an OT network.
How do you view information presented in the exhibit and what does the FortiGate device security status tell you?
Which statement is correct about processing matched rogue devices by FortiNAC?

