Microsoft Microsoft 365 Administrator Exam MS-102 Exam Dumps: Updated Questions & Answers (March 2026)
You have a Microsoft 365 E5 subscription.
You plan to create an anti-malware policy named Policy1.
You need to ensure that Policy1 can detect malicious email messages that were already delivered to a user's mailbox.
What should you do in the Microsoft Defender portal?
You have a Microsoft 365 E5 tenant.
You create an auto-labeling policy to encrypt emails that contain a sensitive info type. You specify the locations where the policy will be applied.
You need to deploy the policy.
What should you do first?
You have a Microsoft 365 E5 subscription.
The subscription contains users that have devices onboarded to Microsoft Defender for Endpoint. Defender for Endpoint is configured to forward signals to Microsoft Defender for Cloud Apps.
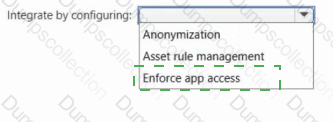
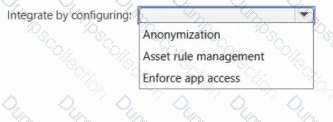
Cloud Discovery identifies a risky web app named App1.
You need to block users from connecting to App1 from Microsoft Edge. Users must be able to bypass the restriction.
Which type of app tag should you use, and what should you configure to integrate Defender for Endpoint with Defender for Cloud

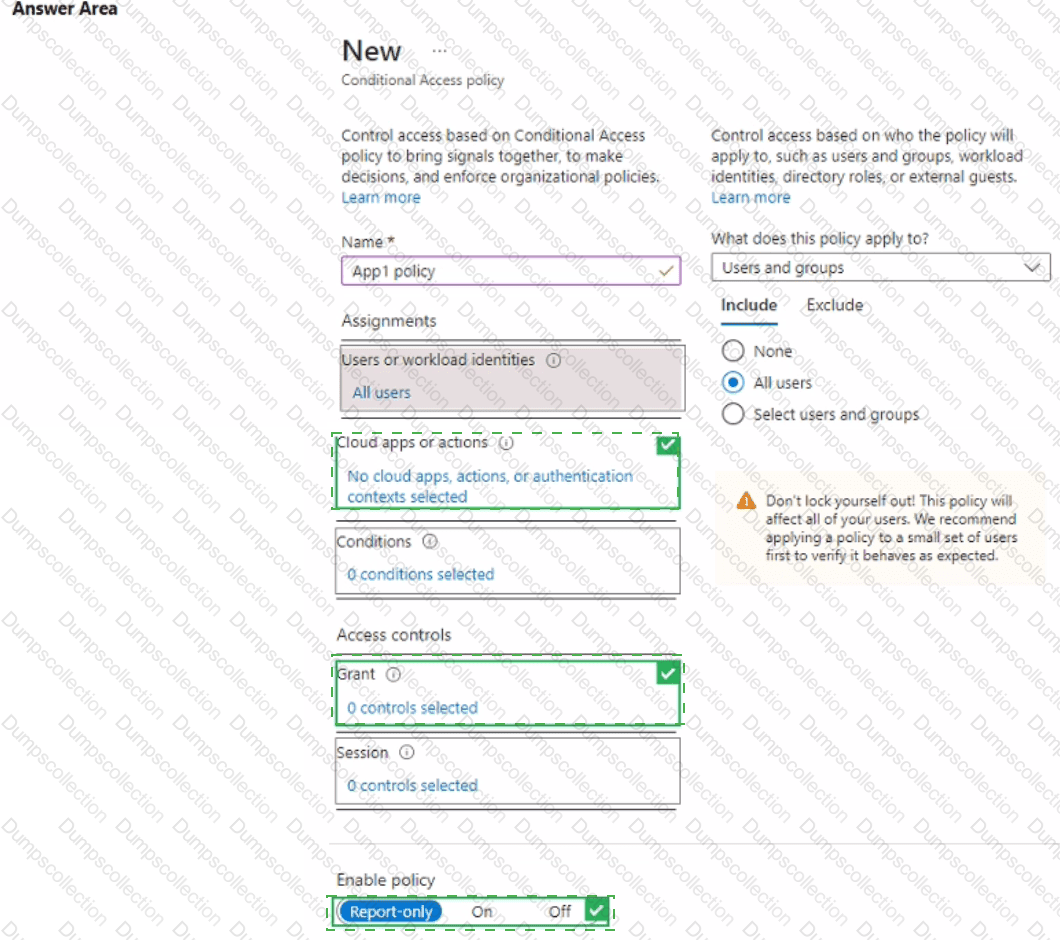
You have a Microsoft 365 Enterprise E5 subscription.
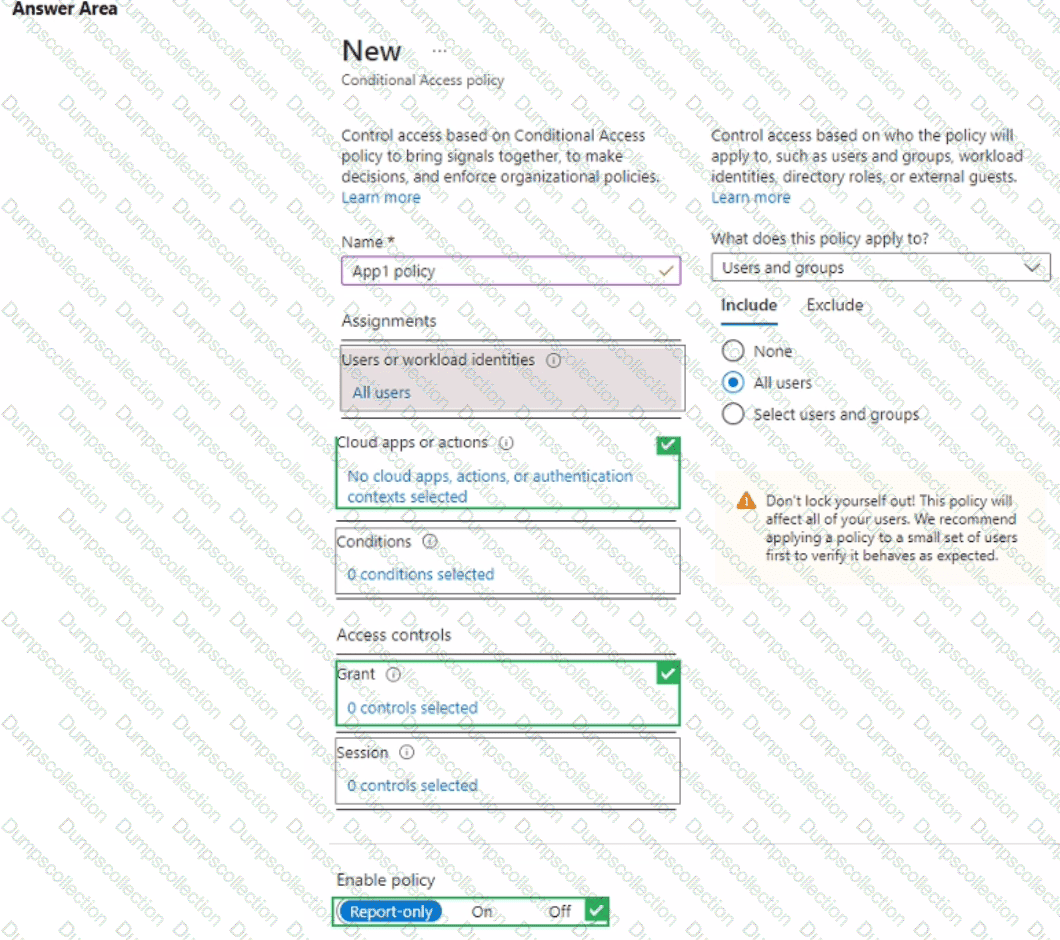
You add a cloud-based app named App1 to the Azure AD enterprise applications list.
You need to ensure that two-step verification is enforced for all user accounts the next time they connect to App1.
Which three settings should you configure from the policy? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription.
You create an account for a new security administrator named SecAdmin1.
You need to ensure that SecAdmin1 can manage Microsoft Defender for Office 365 settings and policies for Microsoft Teams, SharePoint, and OneDrive.
Solution: From the Microsoft 365 admin center, you assign SecAdmin1 the Exchange admin role.
Does this meet the goal?
You have a Microsoft 365 E5 subscription.
You need to configure threat protection tor Microsoft 365 to meet the following requirements:
• Limit a user named User 1 from sending more than 30 email messages per day.
• Prevent the delivery of a specific file based on the file hash.
Which two threat policies should you configure in Microsoft Defender for Office 365? To answer, select the appropriate threat policies in the answer area.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription.
You need to assign a Microsoft Defender for Endpoint baseline.
Which portal should you use?
You have a Microsoft 365 E5 subscription that contains a user named User1.
The subscription has a single anti-malware policy as shown in the following exhibit.
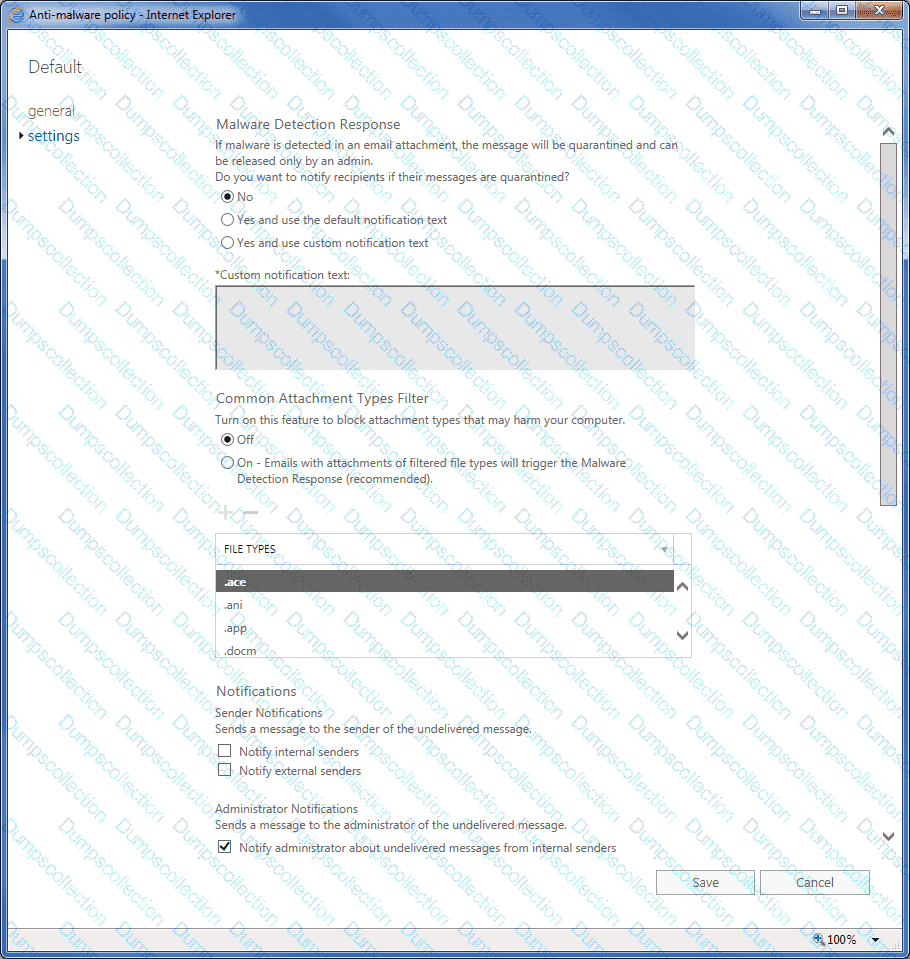
An email message that contains text and two attachments is sent to User1. One attachment is infected with malware.
How will the email message and the attachments be processed?
Your company has a Microsoft E5 tenant.
The company must meet the requirements of the ISO/IEC 27001:2013 standard.
You need to assess the company’s current state of compliance.
What should you use?
HOTSPOT
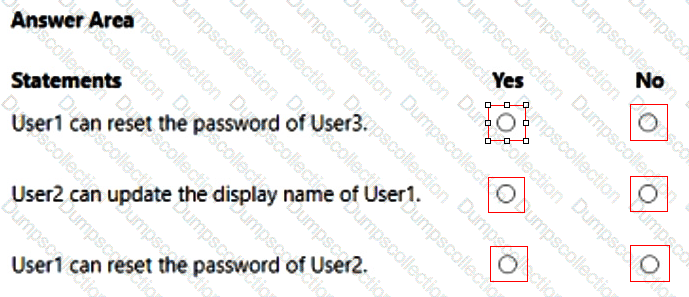
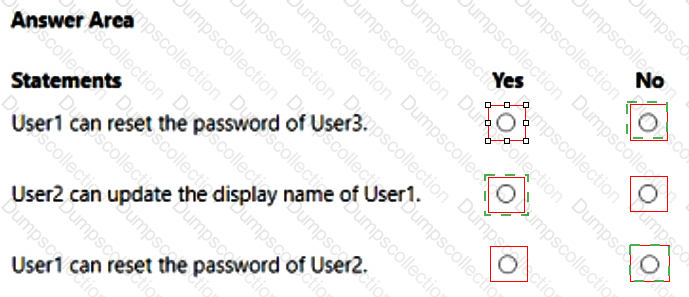
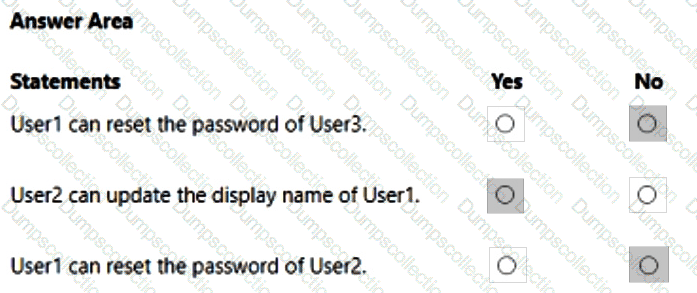
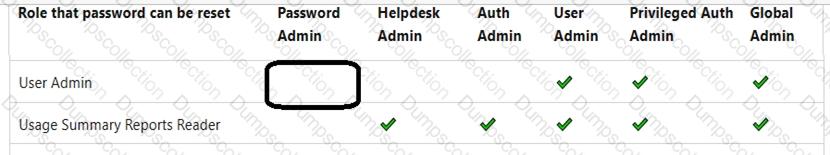
You have an Azure AD tenant that contains the administrative units shown in the following table.
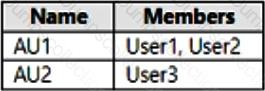
You have the following users:
A user named User1 that is assigned the Password Administrator for AU1 and AU2.
A user named User2 that is assigned the User Administrator for AU1.
A user named User3 that is assigned the User Administrator for the tenant.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.