Oracle Oracle Cloud Infrastructure 2025 Security Professional 1z0-1104-25 Exam Dumps: Updated Questions & Answers (March 2026)
An OCI administrator notices that a compute instance running in the production compartment is unable to create Object Storage buckets using the OCI CLI command:
oci os bucket create --name mybucket --compartment-id
The error message returned states:
"NotAuthorizedOrNotFound: You are not authorized to perform this action."
The administrator verifies that the instance has Internet access and can reach OCI endpoints.
What then could be causing the issue?
Based on the provided diagram, you have a group of critical compute instances in a private subnet that require vulnerability using the Oracle Cloud Infrastructure(OCI) Vulnerability Scanning Service (VSS).
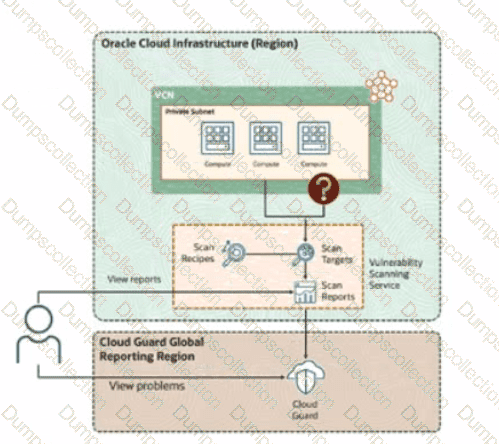
"What additional configuration is required to enable VSS to scan instances in the private subnet
Which Oracle Data Safe feature enables the Internal test, development, and analytics teams to operate effectively while minimizing their exposure to sensitive data?
"Your company is in the process of migrating its sensitive data to Oracle Cloud Infrastructure (OCI) and is prioritizing the strongest possible security measures. Encryption is a key part of this strategy, but you are particularly concerned about the physical security of the hardware where your encryption keys will be stored.
Which characteristic of OCI Key Management Service (KMS) helps ensure the physical security of your encryption keys?
Within OCI IAM identity domains, the AD Bridge component serves a critical role. How does the AD Bridge functionality specifically enhance Identity and Access Management (IAM) practices?
Task 5: Create a Certificate
Create a certificate, where:
Certificate name: PBT-CERT-01-
For example, if your username is 99008677-lab.user01, then the certificate name should be PBT-CERT-01990086771abuser01
Ensure you eliminate special characters from the user name.
Common name: PBT-CERT-OCICERT-01
Certificate Authority: PBT-CERT-CA-01 (created in the previous task)
Task 3: Create a Master Encryption Key
Note: OCI Vault to store the key required by this task is created in the root compartment as PBI_Vault_SP
Create an RSA Master Encryption Key (MEK), where:
Key name: PBT-CERT-MEK-01-
For example, if your username is 99008677-lab.user01, then the MEK name should be PBT-CERT-MEK-01990086771abuser01
Ensure you eliminate special characters from the user name.
Key shape: 4096 bits
Enter the OCID of the Master Encryption Key created in the provided text box:
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
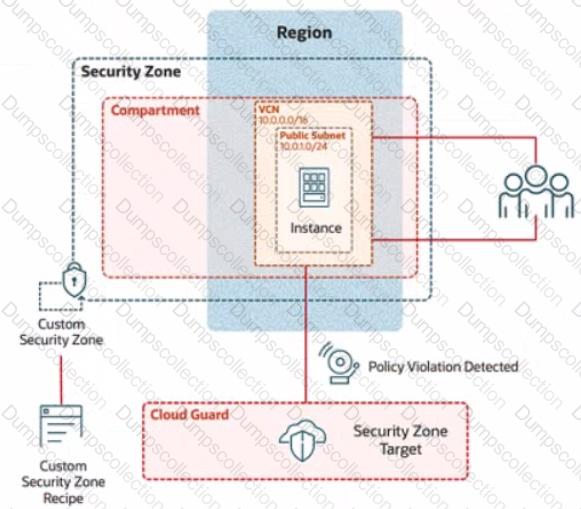
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 2: Create a Security Zone
Create a security Zone named IAD_SAP-PBT-CSZ-01 in your assigned compartement and associate it with the Custom Security Zone Recipe (IAD-SAP-PBT-CSP-01) created in the previous task.
Enter the OCID of the created Security zone in the box below.

Task 7: Verify the OCI Certificate with Load Balancer
Verify HTTPS connection to the load balancer by running the following command in Cloud Shell
curl -k https://
Enter the following URL in the web browser:
https://
If prompted with a certificate error, accept the risk and continue.
Verify web page content by ensuring the text, "You are visiting Web Server 1" from the index.html file is displayed in the browser
Challenge 2 -Task 1
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
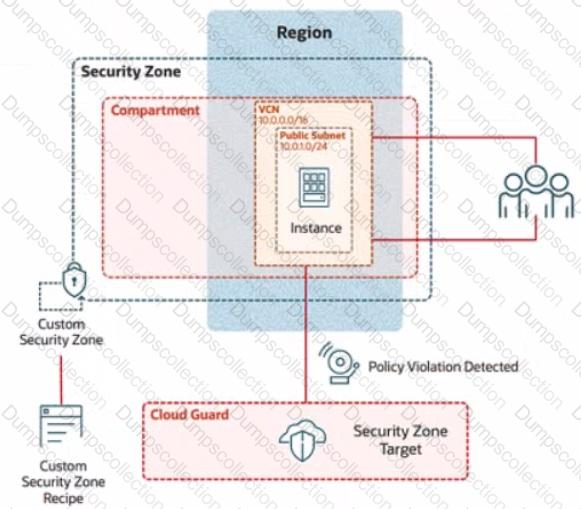
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 1: Create a Custom Security Zone Recipe
Create a Custom Security Zone Recipe named IAD-SP-PBT-CSP-01 that allows the provisioning of compute instances in the public subnet.
Enter the OCID of the created custom security zone recipe in the text box below.

